ARP (Address Resolution Protocol) message processing method and device
An ARP message and ARP cache table technology, applied in the field of ARP message processing methods and devices, can solve the problem of inability to effectively defend against ARP message spoofing, and achieve the effects of avoiding ARP message spoofing, ensuring security, and improving user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
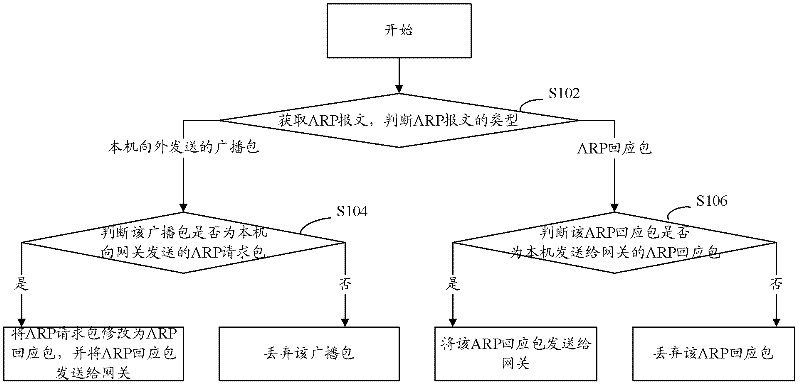
[0042] refer to figure 1 , which shows a flow chart of steps of an ARP packet processing method according to Embodiment 1 of the present application.
[0043] The ARP message processing method of the present embodiment comprises the following steps:
[0044] Step S102: Obtain the ARP message, and determine the type of the ARP message.
[0045] Step S104: If the type of the ARP message is a broadcast packet sent by the local machine, it is judged whether the broadcast packet is an ARP request packet sent by the local machine to the gateway, if so, the ARP request packet is modified into an ARP response packet, and Send the ARP response packet to the gateway; if not, discard the broadcast packet.
[0046] Modify the ARP request packet to an ARP response packet, so that the data packet is directed to the gateway instead of being broadcast, so that the MAC address of the host will not be scanned by other hosts, and will not be maliciously impersonated or used; and , modify the ...
Embodiment 2
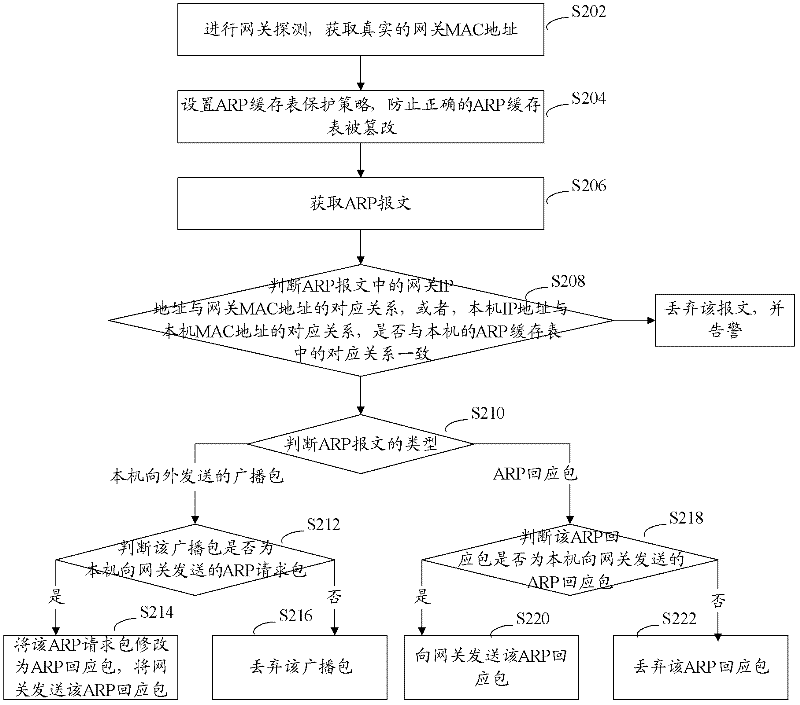
[0051] refer to figure 2 , shows a flow chart of steps of an ARP packet processing method according to Embodiment 2 of the present application.
[0052] The ARP message processing method of the present embodiment comprises the following steps:
[0053] Step S202: Perform gateway detection to obtain the real gateway MAC address.
[0054] The real gateway MAC address is the basis for normal communication between the host and the gateway, and those skilled in the art can obtain the real gateway MAC address in any appropriate manner during implementation.
[0055] Preferably, in this embodiment, standard ARP data packets are sent to the gateway at different time intervals, so as to determine the real MAC address of the gateway.
[0056] A preferred method of sending standard ARP packets to the gateway at different time intervals is the variable frequency packet sending method, that is, the interval time is T×2 n Send a standard ARP packet, where T is a set time constant, gener...
Embodiment 3
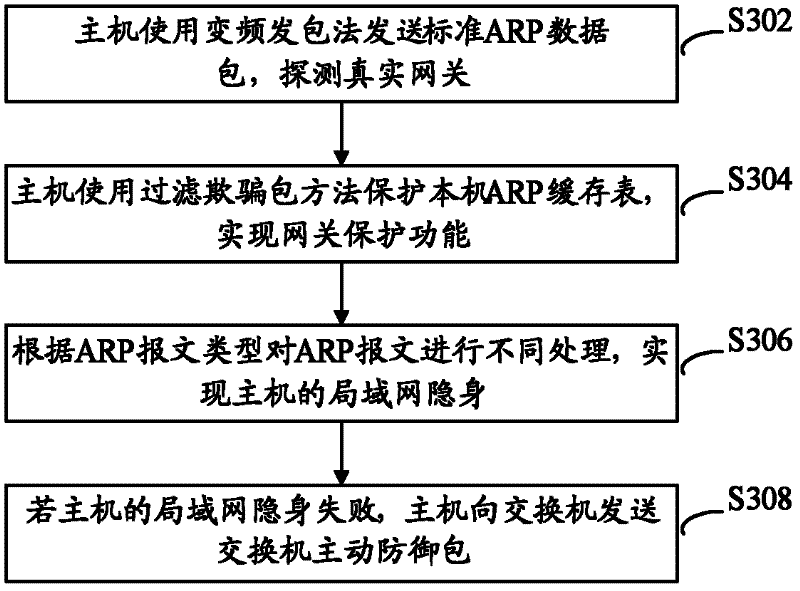
[0073] refer to image 3 , shows a flow chart of steps of an ARP packet processing method according to Embodiment 3 of the present application.
[0074] This embodiment realizes the defense of switch port spoofing on the basis of defending against ARP message spoofing.
[0075] Switch port spoofing refers to the spoofing of the CAM table in the switch based on the principle of switch data exchange. Data sniffing and hijacking can be carried out through switch port spoofing. In theory, just like ARP spoofing, Trojan horses can modify hijacked data to hang horses and steal accounts. P2P tools will also use switch port spoofing principles to control LAN network speed, resulting in unbalanced LAN speed distribution. disrupt the LAN environment. At present, in the security field, there is no good technical solution to defend against such attacks. However, this embodiment adopts the stealth technology of the local area network and the active defense technology of the switch, so a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com