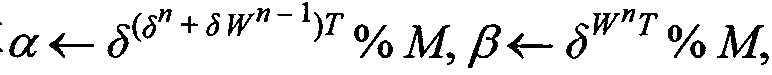A lightweight digital signature method based on the hyperlogarithm problem
A digital signature, lightweight technology, applied to the public key of secure communication, user identity/authority verification, etc., can solve the problem of public key system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0127] The characteristic of the lightweight digital signature method based on the superlogarithmic problem is that it allows each user to obtain two keys, one key can only be privately owned for digital signature, and one key can be made public for identity verification . In this way, verification is not restricted by time, place and confidentiality policy, which becomes very convenient. When the correspondent is agreed to transmit information on the Internet, the sender uses his own private key to sign the message, and the receiver uses the sender's public key to verify it after receiving the message and signature code.
[0128] Each user can obtain the corresponding key certificate from the designated CA digital certificate center. The CA center is an organization that registers and manages users and generates, distributes and controls keys. It uses the key generation component to output a pair of public key and private key of the subject user, and only outputs the public...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com