Data security system applicable to sharing encrypted file and restoring secrete key and method thereof
A technology for encrypting files and data security, applied in the field of data security systems for sharing encrypted files and key recovery, can solve the problems of encrypted file key cracking, complicated encryption/decryption procedures, etc., and achieve the effect of key recovery.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
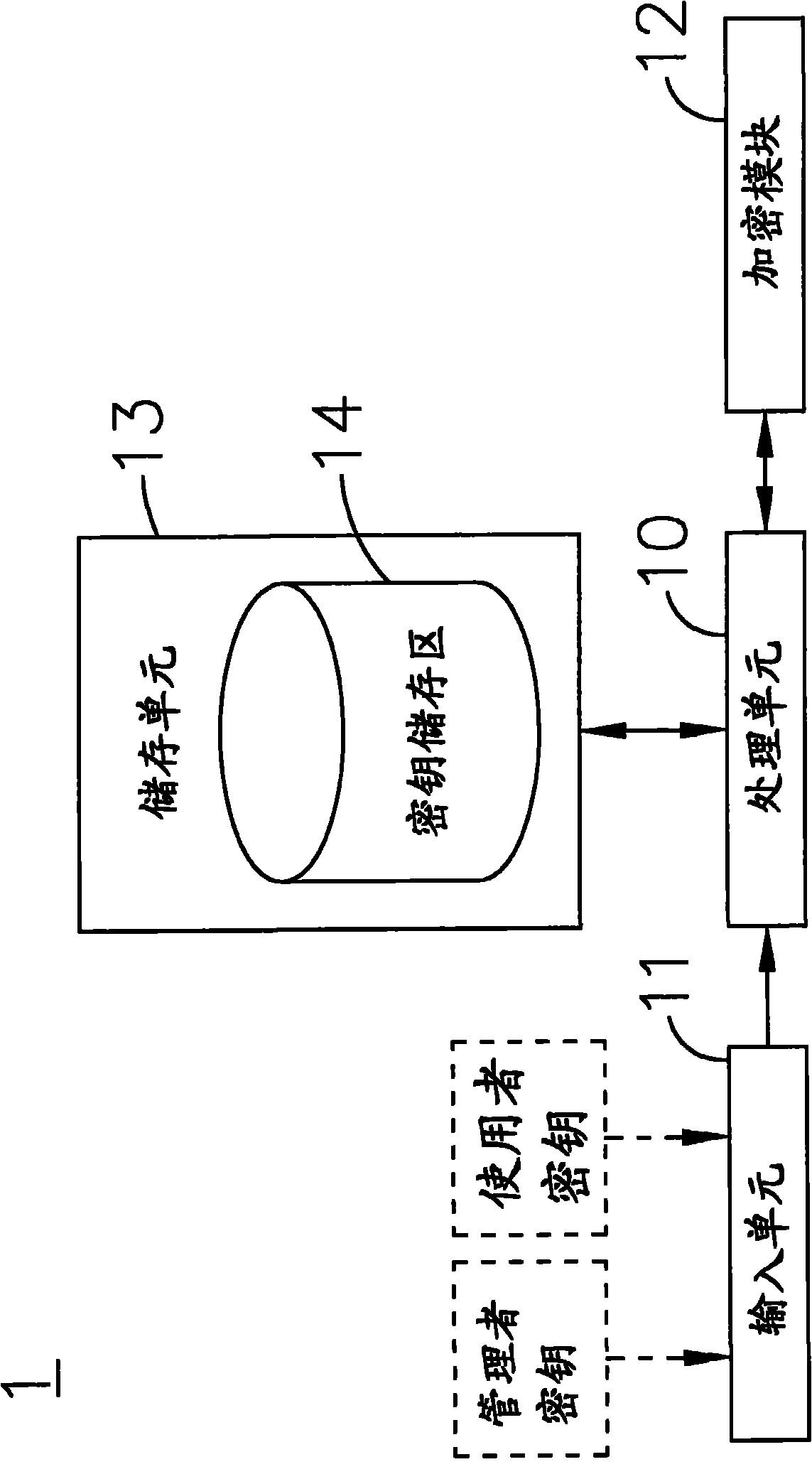
[0061] See figure 1 , Which is a block diagram of the data security system of the present invention. Such as figure 1 As shown, the data security system 1 suitable for sharing encrypted files and recovering keys is connected to the input unit 11, the encryption module 12, and the storage unit 13 by the processing unit 10, respectively. Among them, the input unit 11 may include a keyboard, a mouse, a card reader, a fingerprint recognition device or a face recognition device; the storage unit 13 is used to store the input master key (Master Key) and the user key (User Key), the storage unit 13 includes a key storage area (Key Store) 14, and the storage unit 13 can be a built-in hard disk, an external hard disk, a flash drive or a memory card.
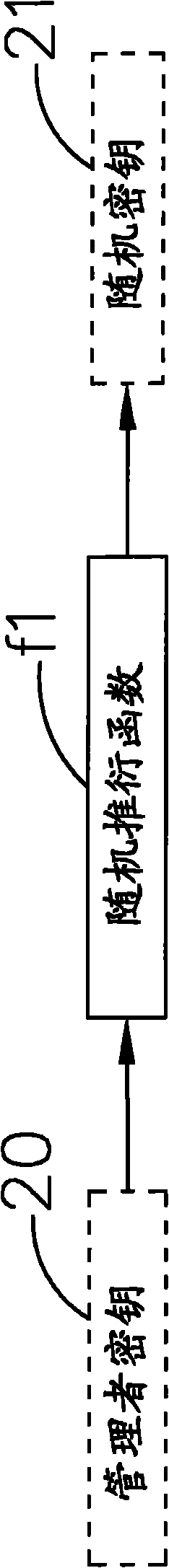
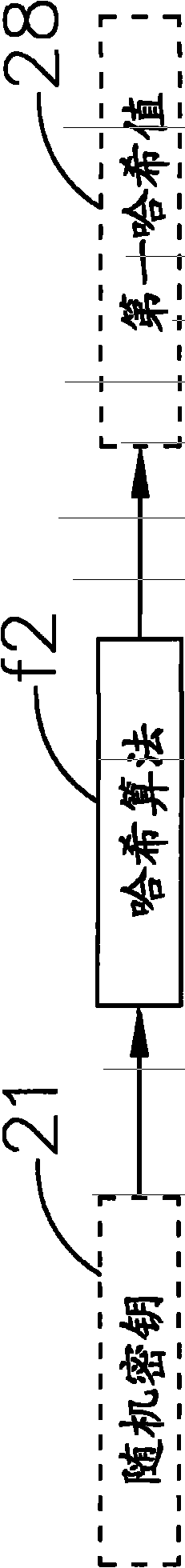
[0062] Please refer to Figure 2 to Figure 4 , Which is a block diagram of generating a random key, a block diagram of generating a first hash value, and a schematic diagram of a key storage area of the data security system of the present...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com