Method for intrusion detection based on negative selection and information gain
An information gain and intrusion detection technology, applied in the field of network security, can solve the problems of low positive detection rate, unstable detection effect, and high false alarm rate, and achieve the effect of good detection effect and stable detection effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
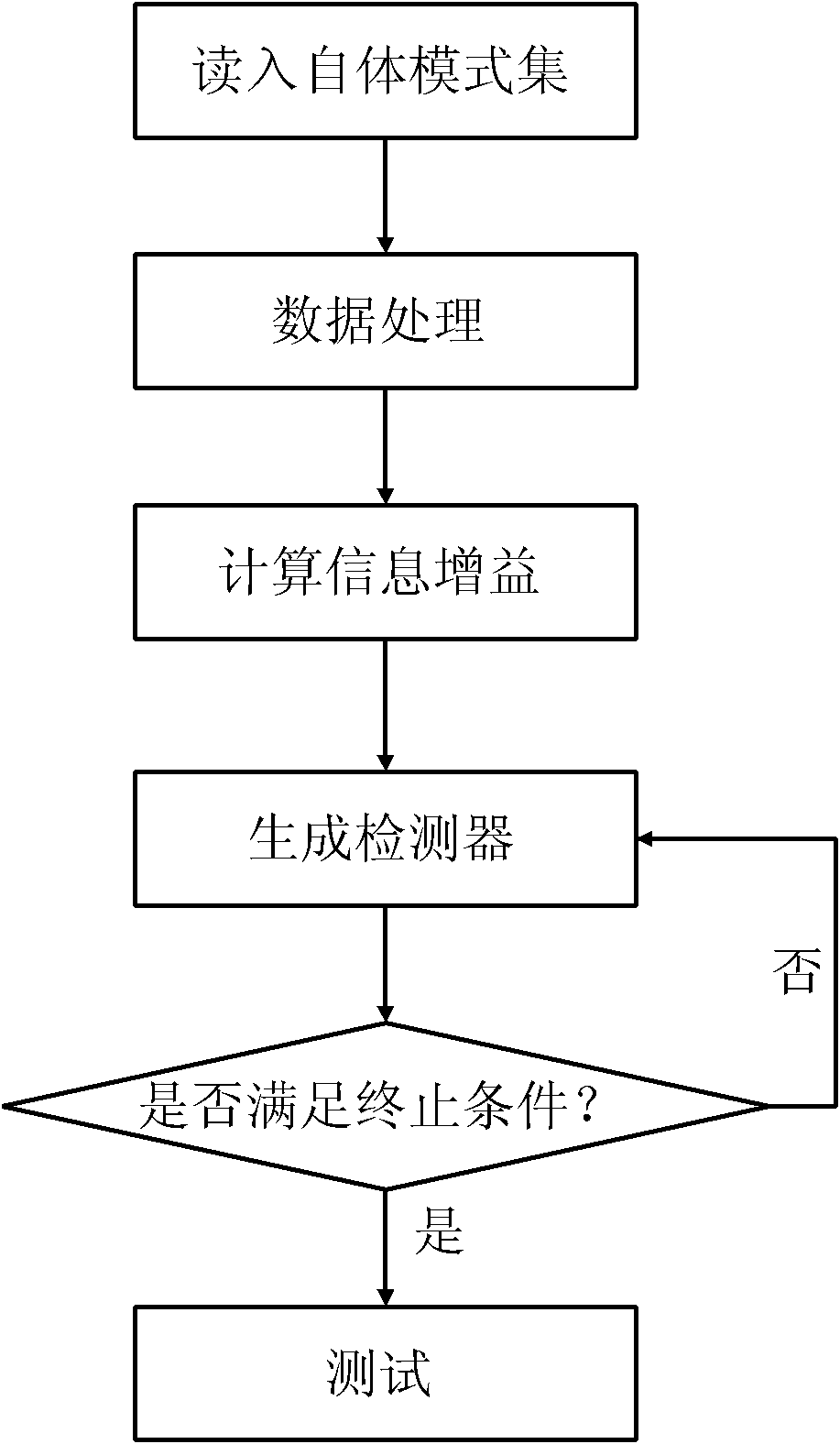
[0027] refer to figure 1 , the specific implementation steps of the present invention are as follows:
[0028] Step 1. Read the normal network data from the KDD99 training data set as the self-pattern set. During the reading process, assign a radius r to each self-pattern s , the radius is constant.
[0029] Step 2, transform, normalize and discretize the data in the read-in self-pattern set.
[0030] (2a) Each piece of data read has 41 dimensional features, 3 of which are text features. For a certain dimensional text feature, the various types it contains are assigned integer values in turn, and then converted into numerical features, using protocol_type Take this dimension as an example. It has three different types: TCP, UDP, and ICMP. Assign values 1, 2, and 3 to these three types in turn to realize the conversion from text features to numerical features. The remaining two-dimensional text features follow this method. transformation;
[0031] (2b) Normalize the con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com