Digital signing system and method
A digital signature and digital signature technology, applied in the field of information security, can solve problems such as troublesome, low security, and inability to verify whether the bitmap has been changed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
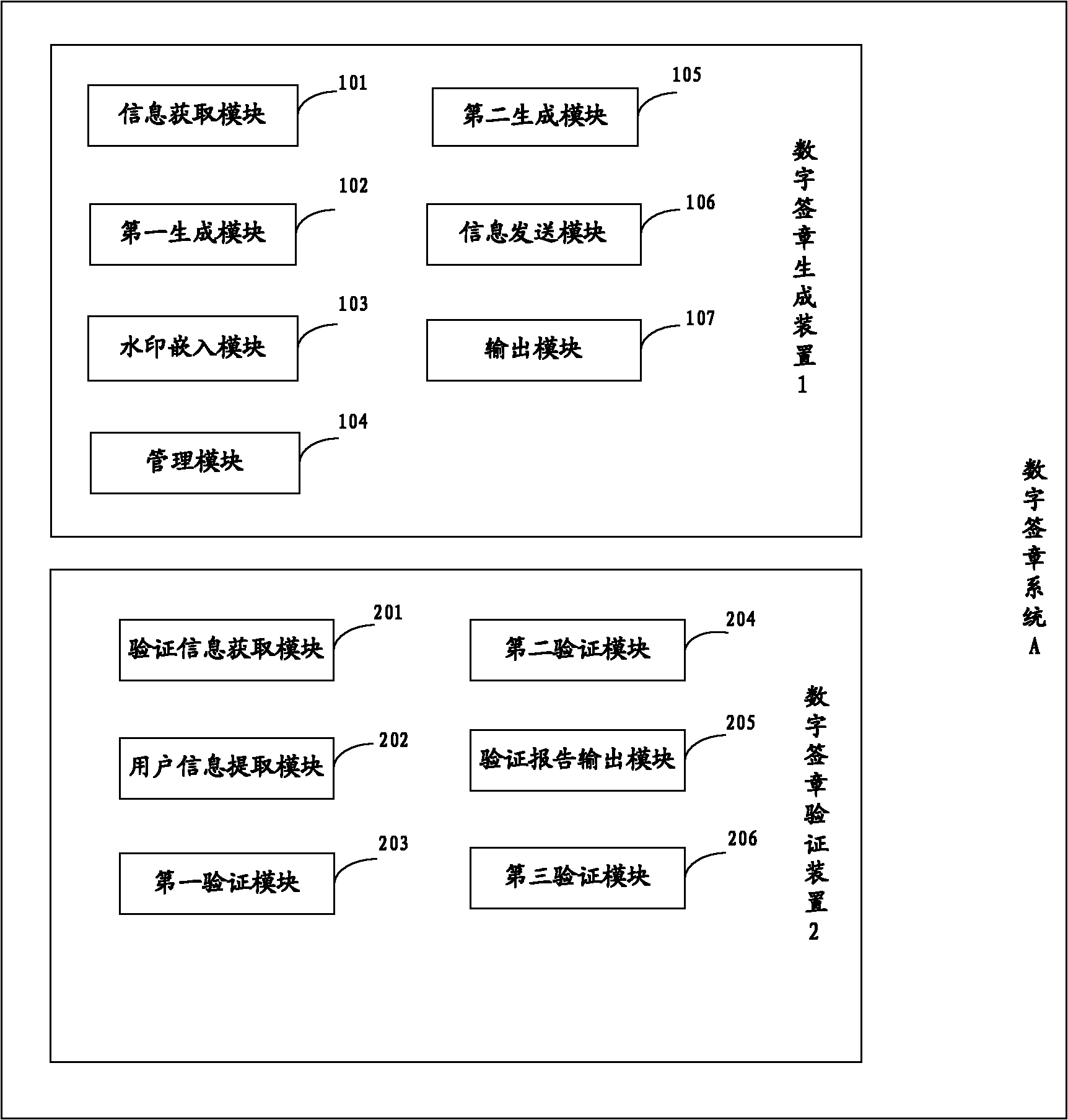
[0131] figure 1 , is a schematic block diagram of a digital signature system A provided by the present invention, specifically comprising: a digital signature generation device 1, a digital signature verification device 2;
[0132] Digital signature generation device 1, used to complete the digital signature operation process;
[0133] The digital signature generation device 1 specifically includes: an information acquisition module 101 , a first generation module 102 , a watermark embedding module 103 , a management module 104 , a second generation module 105 , an information sending module 106 and an output module 107 .
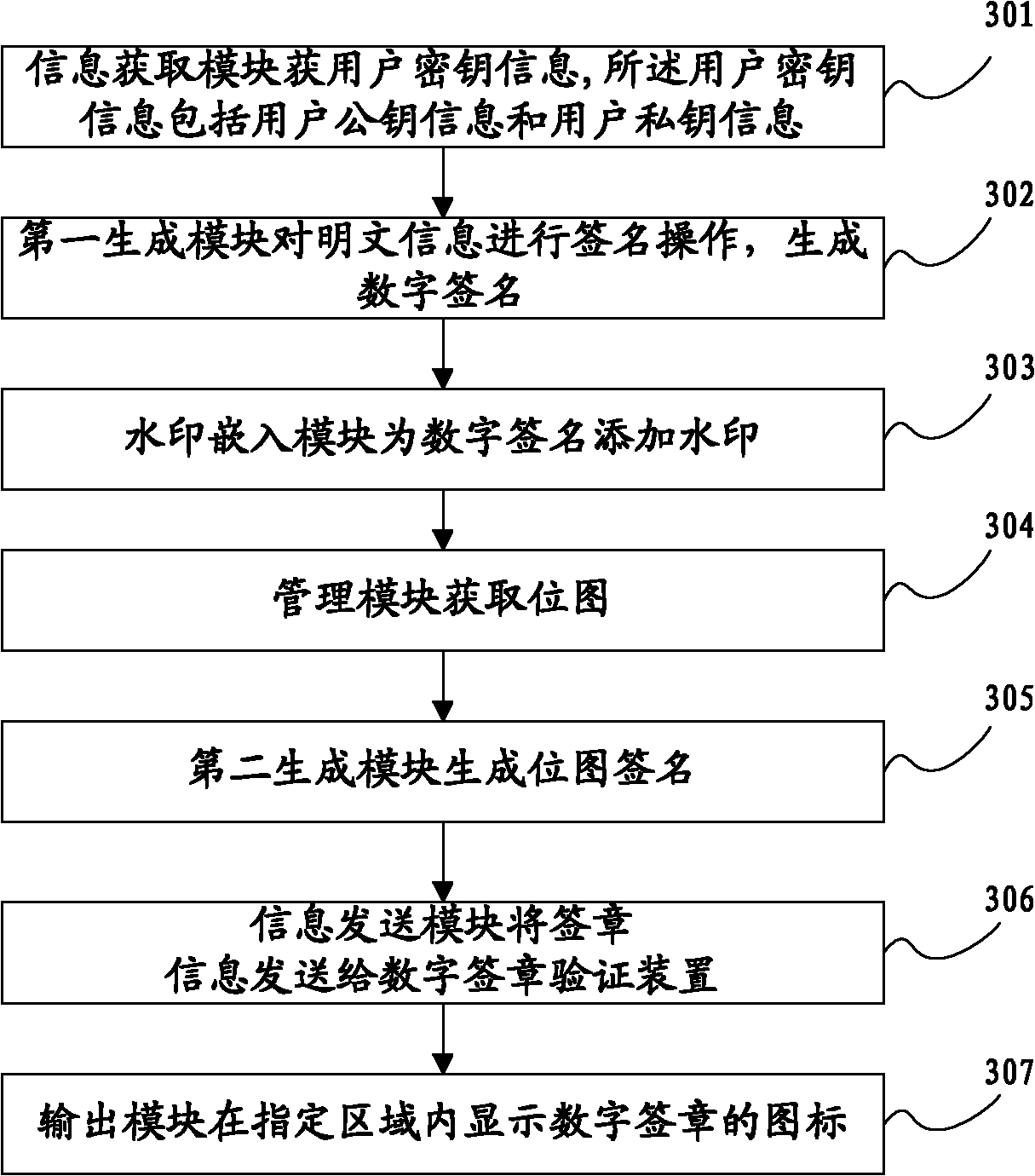
[0134] An information acquisition module 101, configured to acquire user key information, where the user key information includes user public key information and user private key information;
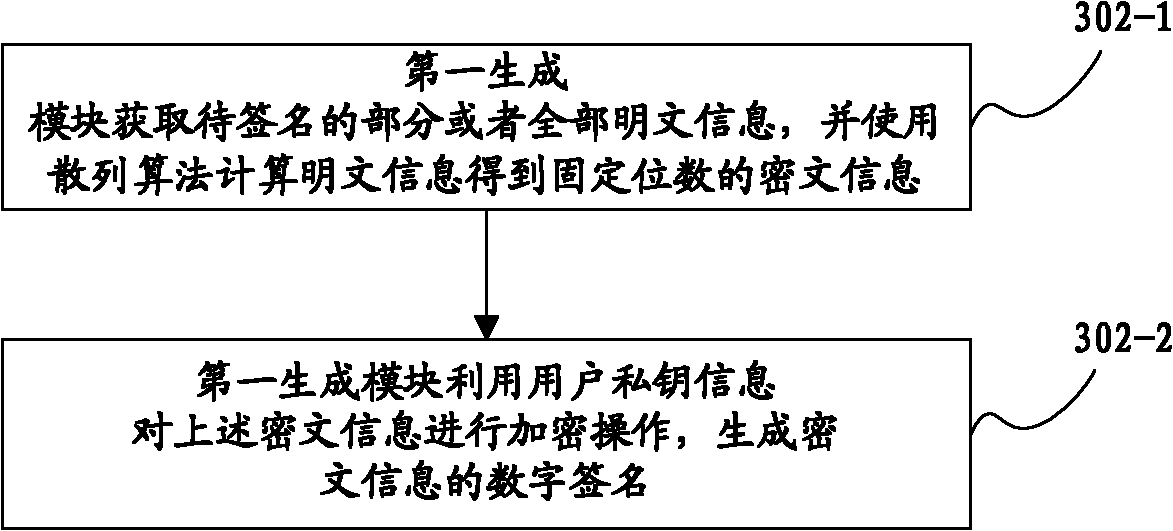
[0135] The first generation module 102 specifically includes: a first information acquisition unit 201-1, a first signature unit 101-2;
[0136] The first informa...
Embodiment 2
[0217] Figure 4 , is a schematic block diagram of the second digital signature system B provided by the present invention, specifically comprising: a digital signature generation device 5, a digital signature verification device 6;
[0218] Digital signature generation device 5, used to complete the digital signature operation process;
[0219] The digital signature generation device 5 specifically includes: an information acquisition module 501, a first generation module 502, a watermark embedding module 503, a management module 504, a second generation module 505, an information sending module 506, and an output module 507;
[0220] Information acquisition module 501: used to acquire user key information, the user key information includes user public key information and user private key information;
[0221] The first generation module 502 specifically includes: a first information acquisition unit 502-1, a first signature unit 502-2;
[0222] The first information obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com