New password authentication method and device
An authentication method and a technology of an authentication device, which are applied in the field of information network security, can solve problems such as the real-time effect of decryption, and achieve the effects of protecting security, increasing random characteristics, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
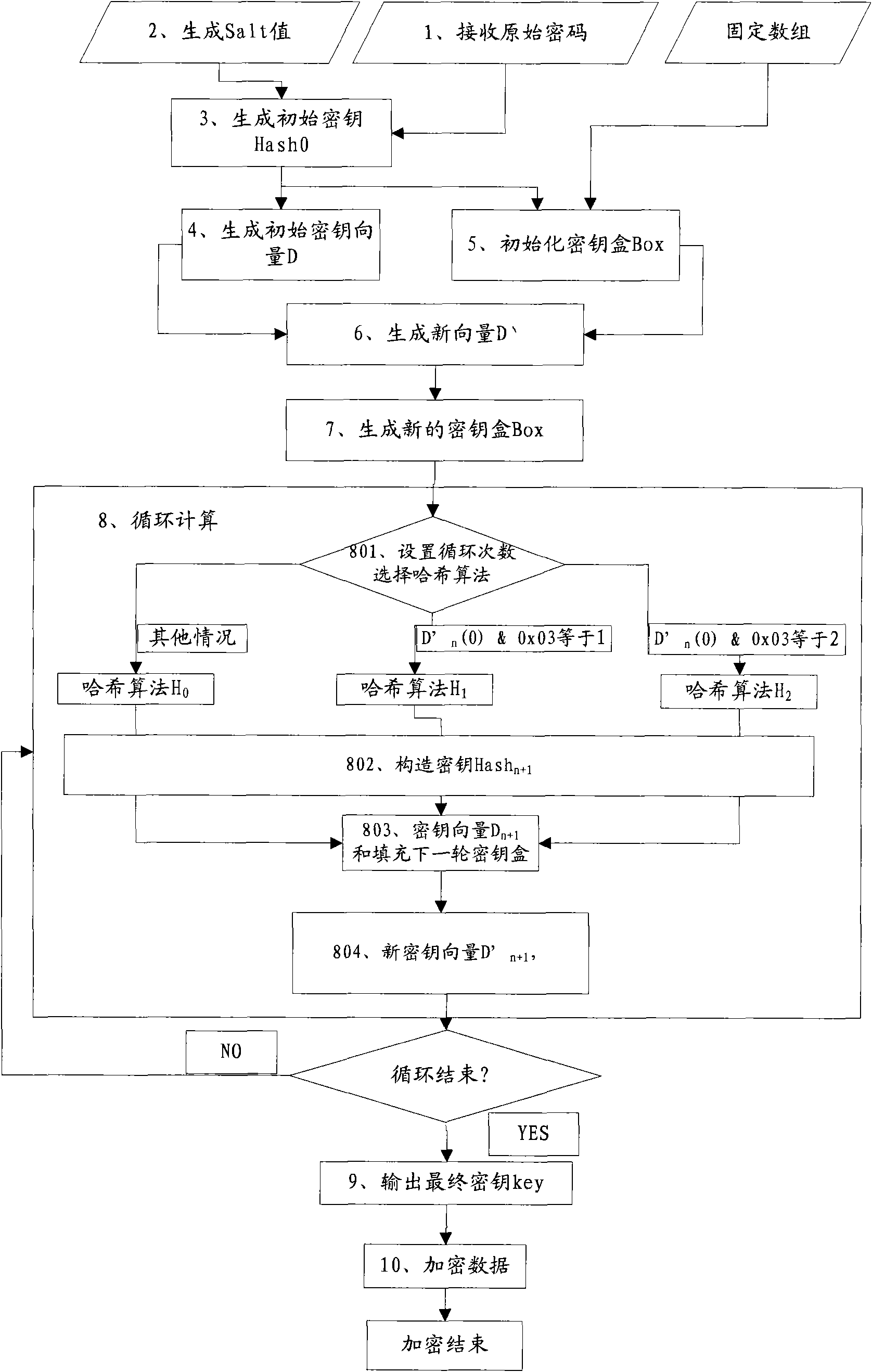
[0044] see figure 1 Shown, a kind of new password authentication method of the present invention comprises:
[0045] Step 1, receiving the input original password;
[0046] Step 2, generate a random value, which is customarily called the Salt value in password science;
[0047] In this step, a random Salt value is generated to ensure that even with the same password and the same data, the encrypted data output at different times is different, increasing the randomness of the method.
[0048] Step 3, according to the random value Salt value and the original password (Password), generate the initial key Hash through the hash algorithm 0 ;
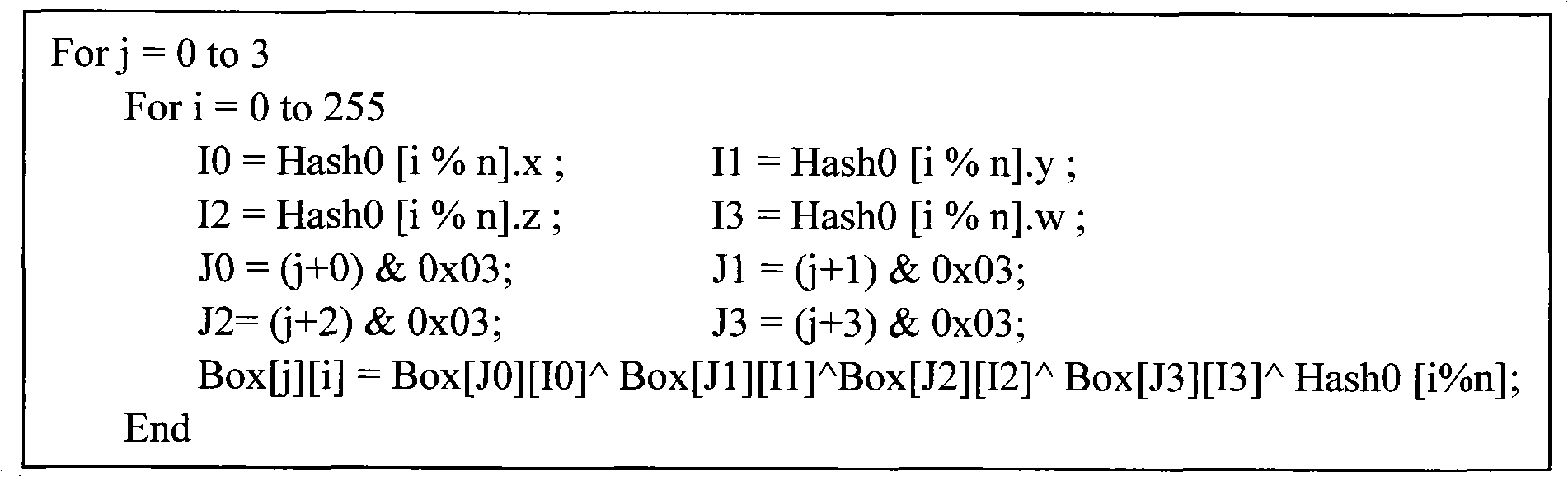
[0049] In this step, the random value Salt value and the original password (Password) are input, and one of the existing hash algorithms is selected as the default hash algorithm H 0 , H 0 It can be MD5, SHA1, RIPEMD160 and other algorithms. Specifically: Hash 0 =H 0 (salt+password); remember Hash 0 The size is L 0 bytes.
[0050] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com