Method and device for building tunnels as well as network equipment
A technology for tunnel establishment and network protocol, which is applied in the field of network communication and can solve the problems of inability to meet the requirements of 6rd tunnel and 6rd tunnel.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
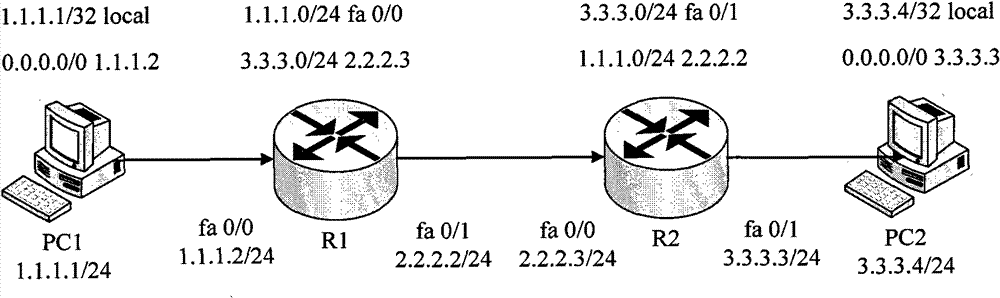
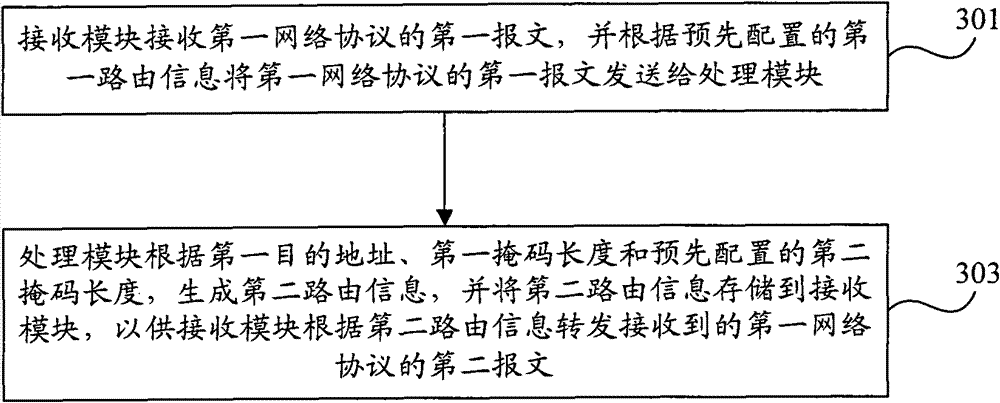
[0032] image 3 It is a flow chart of the method for establishing a tunnel provided by Embodiment 1 of the present invention. The executor of this embodiment may be a router, especially a router at the border of an IPv6 network and an IPv4 network, that is, the router is in both an IPv6 network and an IPv4 network. Such as image 3 As shown, the tunnel establishment method in this embodiment includes:
[0033] Step 301, the receiving module receives the first message of the first network protocol, and sends the first message of the first network protocol to the processing module according to the pre-configured first routing information; the first routing information includes the first network protocol a protocol address prefix and a first mask length, the first packet of the first network protocol includes a first destination address;
[0034] First, before step 301 is executed, first routing information is pre-configured on the router, where the first routing information i...
Embodiment 2
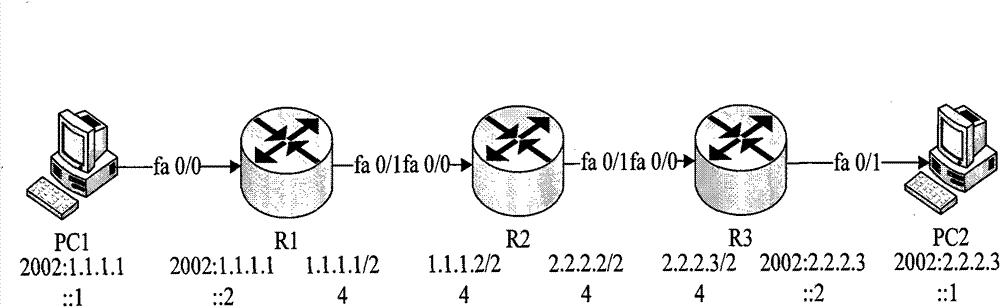
[0051] Figure 4 It is a flow chart of the tunnel establishment method provided by Embodiment 2 of the present invention. This embodiment is based on embodiment one, such as Figure 4 As shown, the difference from Embodiment 1 is that step 303 specifically includes:
[0052] Step 303a, the processing module generates second routing information according to the first destination address, the first mask length and the pre-configured second mask length;
[0053] Specifically, the processing module may use the methods described in steps 3031 to 3034 to generate the second routing information, but it is not limited thereto. Wherein, the pre-configured second mask length may also be other values, for example: 32.
[0054] Step 303b, the processing module encapsulates the first packet of the first network protocol into the first packet of the second network protocol according to the second routing information, and forwards the first packet of the second network protocol according ...
Embodiment 3
[0062] Figure 5 It is a flow chart of an implementation method for the receiving module to forward the second packet of the first network protocol provided by Embodiment 3 of the present invention. Such as Figure 5 As shown, the forwarding method of this embodiment includes:
[0063] Step 501, the receiving module receives a second message of the first network protocol, and the second message of the first network protocol includes a second destination address;
[0064] This step specifically refers to that the exchange chip receives an IPv6 message other than the first IPv6 message, and the IPv6 message includes a destination IPv6 address, such as a destination IPv6 address 1000:303:300::1; wherein, due to the second IPv6 message The first IPv6 message and the first IPv6 message are sent by the same device and sent to the same other device, therefore, the first IPv6 message and the second IPv6 message have the same source IPv6 address and destination IPv6 address, that is,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com