Method and arrangement relating to a communication device
A technology of equipment and equipment models, applied in security devices, wireless communications, computer security devices, etc., can solve the problems that third parties cannot propose MIDlets, and there is no safe way
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
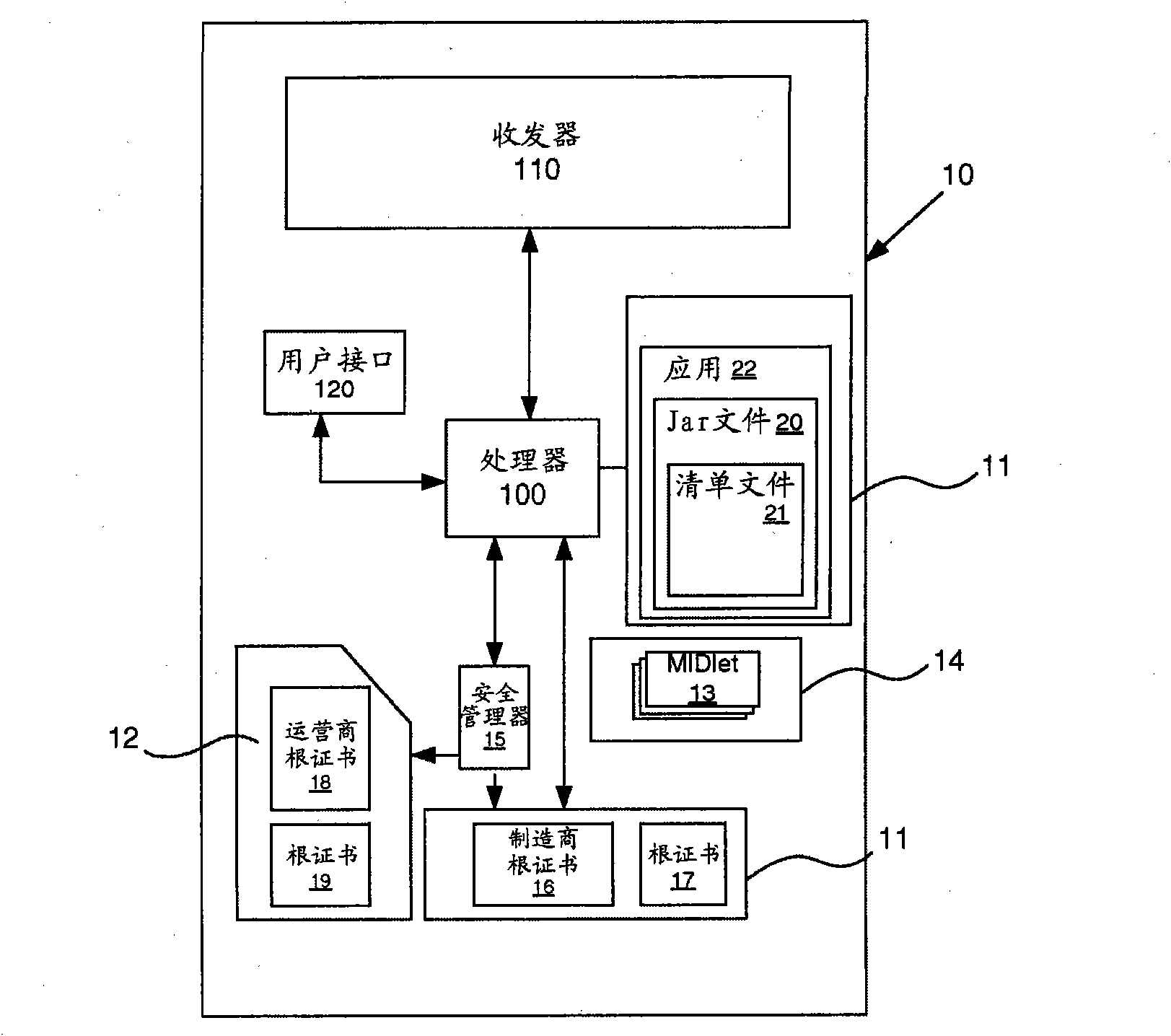
[0032] In the following, the invention will be illustrated with reference to a mobile telephone operating in a telecommunications network. A mobile phone is usually associated with a subscriber and a specific phone number using a SIM card, which is an active (smart) card inserted into the phone. However, a built-in special memory can also be used for the same purpose. The mobile phone is provided with a reader for obtaining information from the ISM card, and can also write information to the card (eg using the card as memory for storing telephone numbers etc. as is known in the art). Applications can be downloaded to the phone and run on a special platform (a so-called virtual machine, usually implemented as a Java environment). The present invention does not exclude any kind of third-party applications like native code, and the phone can be an open phone based on any operating system, which can implement mechanisms similar to the Java environment. Also, the present inventio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com