Generation method and device of safe keys
A security key and key generation technology, applied in security devices, wireless communications, electrical components, etc., can solve the problems of reducing resource utilization and increasing the delay of the key generation system, and achieve the effect of reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
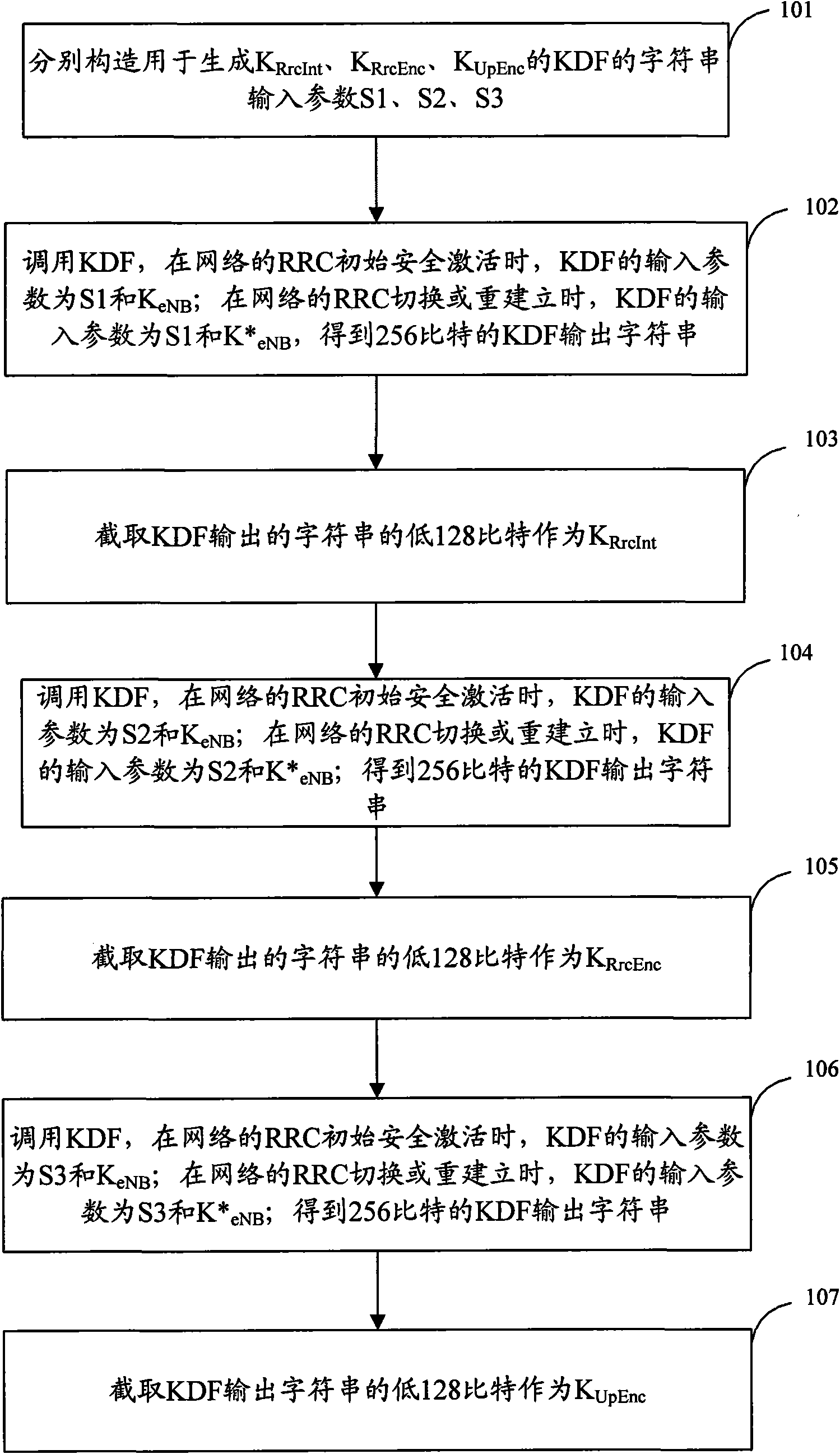
[0058] Embodiment 1: The generation process of the security key is as follows figure 2 As shown, before generating the security key, the communication parties of the network negotiate the interception method of the KDF output string that generates the three keys, and the interception methods should not be the same, that is, the three keys generated are different , Can enhance security, the method includes the following steps:
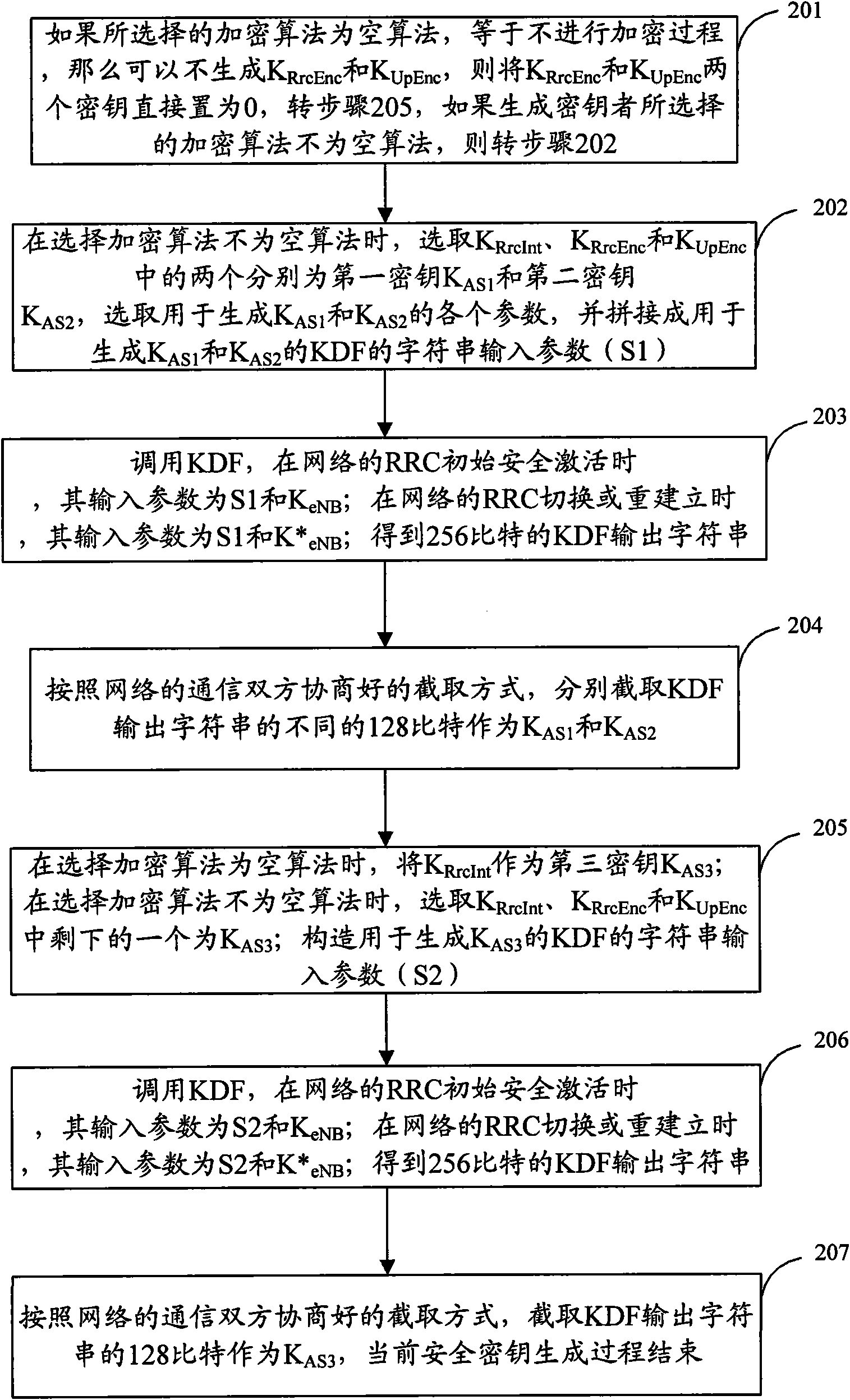
[0059] Step 201: If the selected encryption algorithm is an empty algorithm, which means that the encryption process is not performed, then K may not be generated RrcEnc And K UpEnc , Then K RrcEnc And K UpEnc Set the two keys directly to 0, go to step 205, if the selected encryption algorithm is not an empty algorithm, go to step 202;
[0060] Step 202: When the selected encryption algorithm is not an empty algorithm, select K RrcInt , K RrcEnc And K UpEnc Two of them are the first key K AS1 And the second key K AS2 , Select for generating K AS1 A...
Embodiment 2
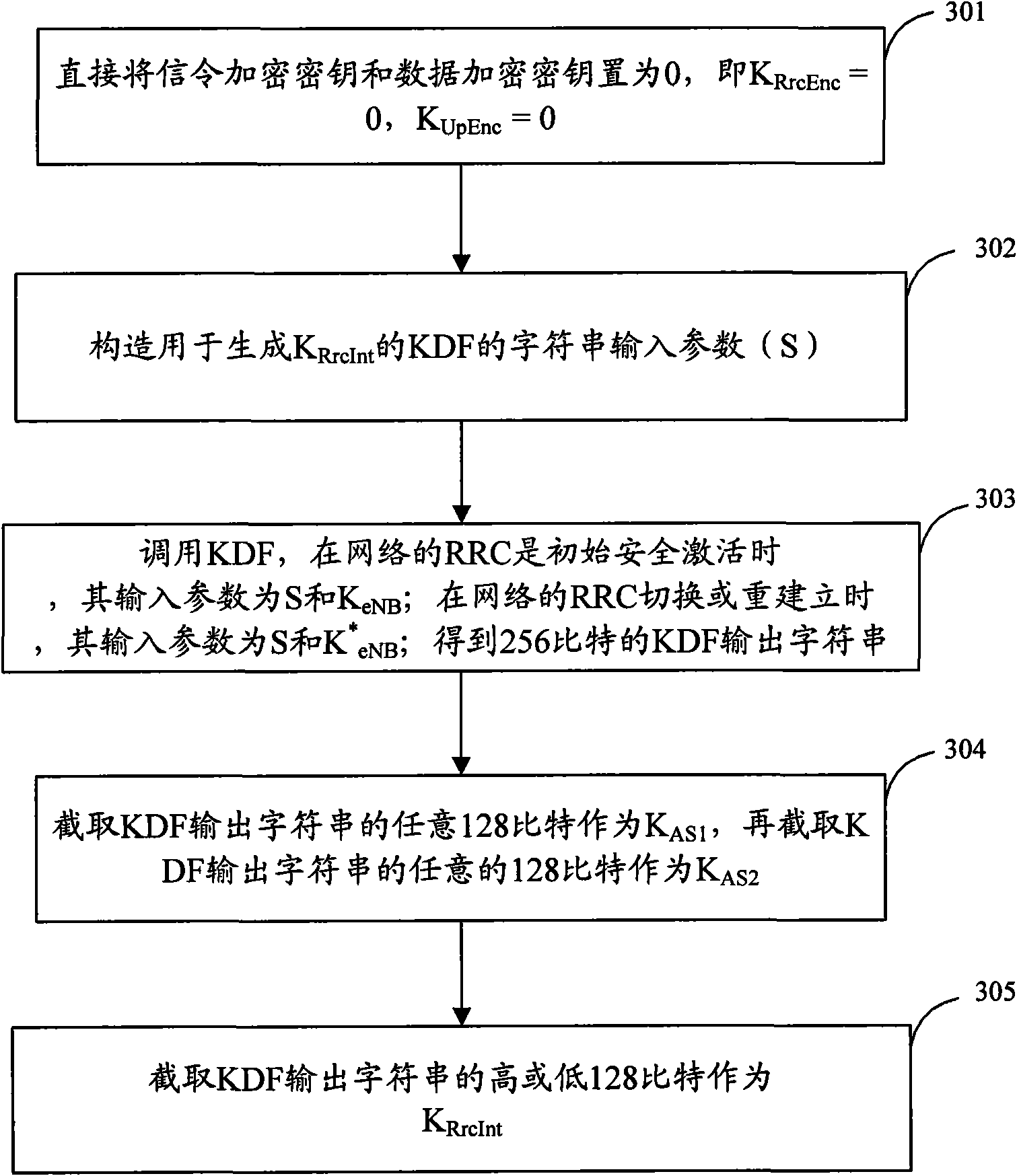
[0078] Embodiment 2: When the selected encryption algorithm is an empty algorithm, the interception of the KDF output string is to intercept the KDF output string with high or low 128 bits. The present invention implements an embodiment of the security key generation method, such as image 3 As shown, including the following steps:
[0079] Step 301: directly set the signaling encryption key and data encryption key to 0, namely K RrcEnc =0, K UpEnc =0;
[0080] Step 302: Construct for generating K RrcInt The KDF string input parameter(S);
[0081] Choose to generate K RrcInt Parameters: P0 RrcInt , L0 RrcInt , P1 RrcInt , L1 RrcInt , FC=0x15, construct K RrcInt The string input parameters of KDF are:
[0082] S=FC||P0 RrcInt ||L0 RrcInt ||P1 RrcInt ||L1 RrcInt ,
[0083] Among them, P0 RrcInt Select according to Table 1, namely P0 RrcInt 0x04, P1 RrcInt Select according to Table 3, L0 RrcInt For P0 RrcInt Length in bytes, L1 RrcInt For P1 RrcInt The byte length, acco...
Embodiment 3
[0089] Embodiment 3: When the selected encryption algorithm is not an empty algorithm, set K RrcEnc And K UpEnc Generated in the process of invoking KDF once, the interception of the KDF output character string adopts the interception of the KDF output character string with high 128 bits or low 128 bits. The present invention implements an embodiment of a security key generation method, such as Figure 4 As shown, including the following steps:
[0090] Step 401: Select for generating K RrcEnc And K UpEnc Each parameter of, and spliced into KDF string input parameters (S1);
[0091] Specifically, select to generate K RrcEnc Parameters: P0 RrcEnc , L0 RrcEnc , P1 RrcEnc , L1 RrcEnc , And used to generate K UpEnc Parameters: P0 UpEnc , L0 UpEnc , P1 UpEnc , L1 UpEnc ; Among them, P0 i Select according to Table 1, P1 i Select according to Table 3, L0 i For P0 i Length in bytes, L1 i For P1 i The byte length, according to Table 1 and Table 3, L0 i , L1 i The value of is 0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com