Method and system for deploying application of smart card, and security module
A security module and deployment system technology, applied in the field of financial payment, can solve the problems of smart card application deployment relying on upper computer software upgrades, application deployment security relying on multiple links, etc., to reduce system risks and management complexity, reduce system risks effect of stress
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] Embodiment 1. A deployment method for a smart card application, comprising:
[0051] Save the application in the security module;
[0052] The user requests the security module to install the application on the smart card through the terminal;
[0053] The security module establishes a secure connection with the smart card, and installs the application requested by the user to be installed on the smart card through the secure connection.
[0054] In this embodiment, the actual form of the security module can be but not limited to smart card, UKEY or other modules, devices, etc.; the security module is used as the security carrier of the application to realize the end-to-end application security off-line deployment, and the security is controlled by the security module. It does not depend on the upper computer application software or SAM certification.
[0055] In this embodiment, the security module can be reused. For example, when a new application is issued, it can ...
Embodiment 2
[0072] Embodiment 2. A security module, comprising:
[0073] a storage unit for storing applications;
[0074] The installation unit is configured to establish a secure connection with the smart card after receiving a request from the user to install the application on the smart card, and install the application requested by the user to the smart card through the secure connection.
[0075] In this embodiment, the security module may also include:
[0076] A receiving unit, configured to receive a security module-oriented WEB application installation service package;
[0077] A parsing unit, configured to parse out the received WEB application installation service package; optionally parse the WEB application installation service package into a format that is convenient for the application;
[0078] The checking unit is used to check the integrity of the parsed WEB application installation service package; it can also further check other security attributes of the WEB applic...
Embodiment 3
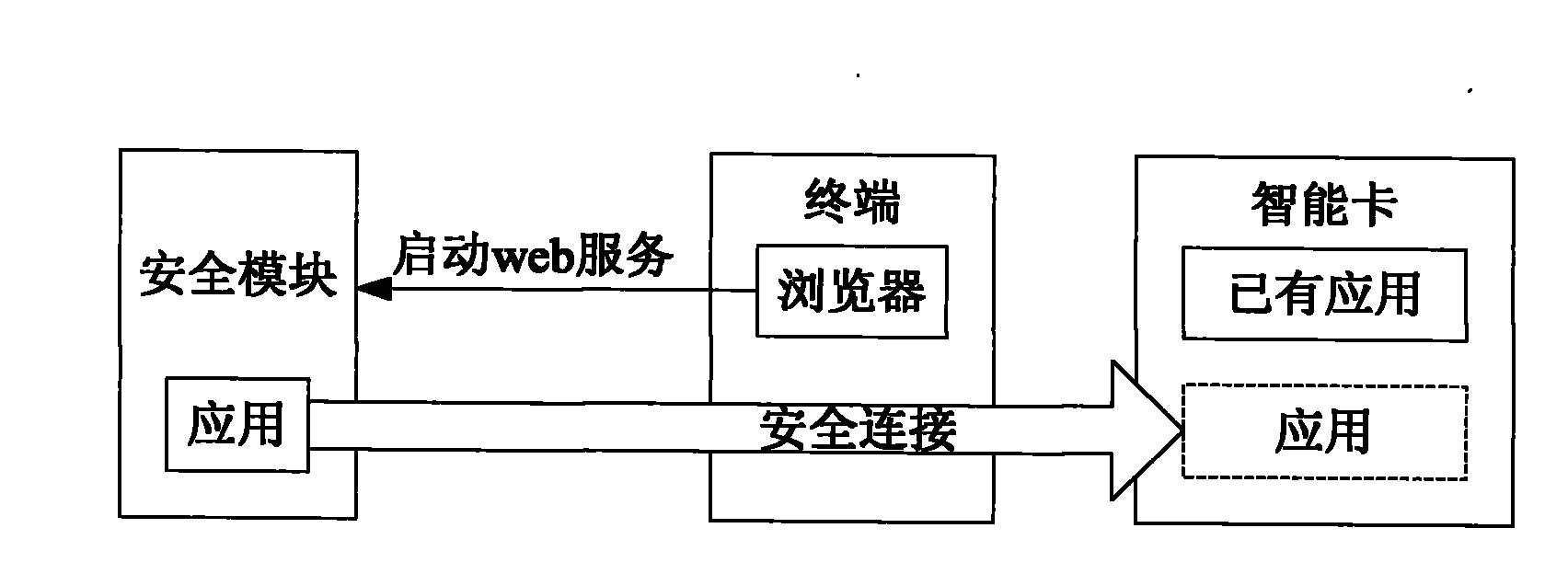
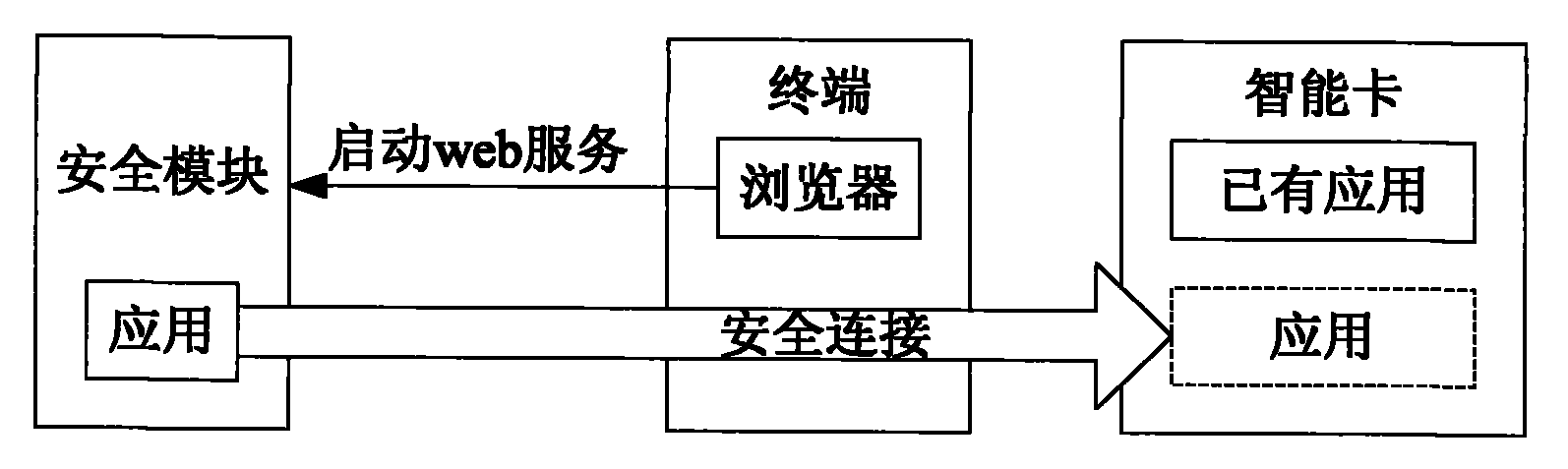
[0083] Embodiment 3. A deployment system for smart card applications, such as figure 1 As shown, including: the terminal and the security module in Embodiment 2;
[0084] The terminal is used for the user to request the security module to install an application on the smart card, and to connect the security module and the smart card.
[0085] In this embodiment, the terminal may specifically include:
[0086] a first interface unit, configured to connect to the security module;
[0087] a second interface unit, configured to connect to the smart card;
[0088] The browser is used to know the applications provided in the WEB application installation service package saved by the security module, and display them to the user in the form of an application list. When the user clicks on an application in the application list, a request for installing the application is generated to all the security module described above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com