Method and system for auditing and distributing sensitive data based on evolution strategy
A sensitive data and evolutionary strategy technology, applied in the field of information security, can solve problems such as content change, loss of effectiveness in confirming the original data source, highly sensitive data leakage audit application, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
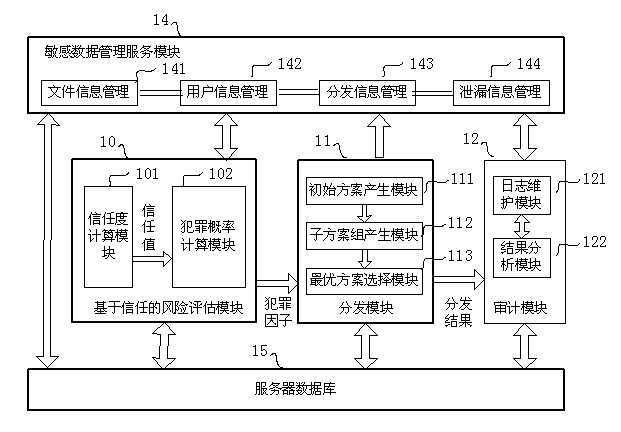
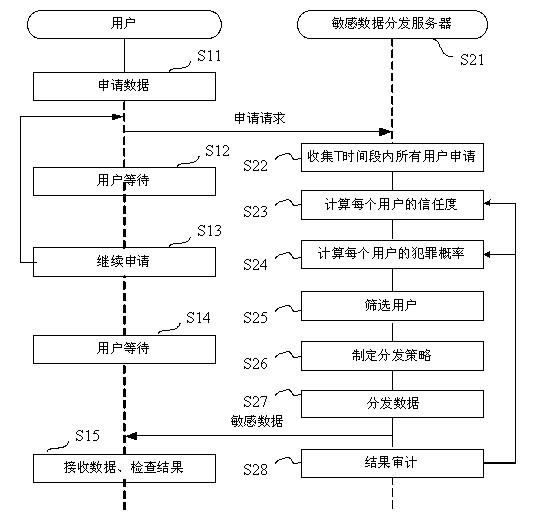
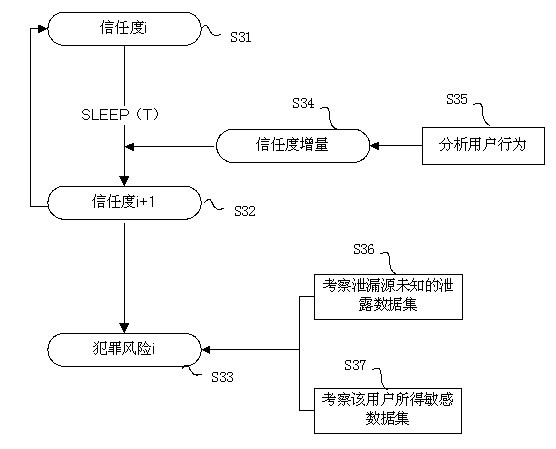
[0055] The evolution strategy-based sensitive data audit distribution method and system provided by the present invention can be applied to the technical field of anti-leakage applications such as enterprise design drawings and confidential documents of confidential institutions, without any preprocessing of sensitive data carriers (such as embedding watermarks) operation), and because the distribution refers to the user attributes of the received data, once a data leak is found, the system can detect the leak source with a high probability in a short period of time, thereby rejecting the leak source’s subsequent application and suppressing its leak behavior , effectively preventing the leakage of sensitive data.
[0056] The present invention needs to generate an initial allocation plan based on whether there is a distribution history, obtain a group of feasible allocation sub-schemes from the initial plan, and analyze the allocation plan by using evaluation criteria; in addit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com