Multicast message processing method and device and equipment
A technology of multicast message and processing method, which is applied in the branch office to provide special service devices, data exchange details, digital transmission system, etc., and can solve the problem of affecting multicast services, inability to distinguish legal multicast streams from illegal multicast streams, etc. It cannot solve the problem of excessive consumption of the multicast table and achieve the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
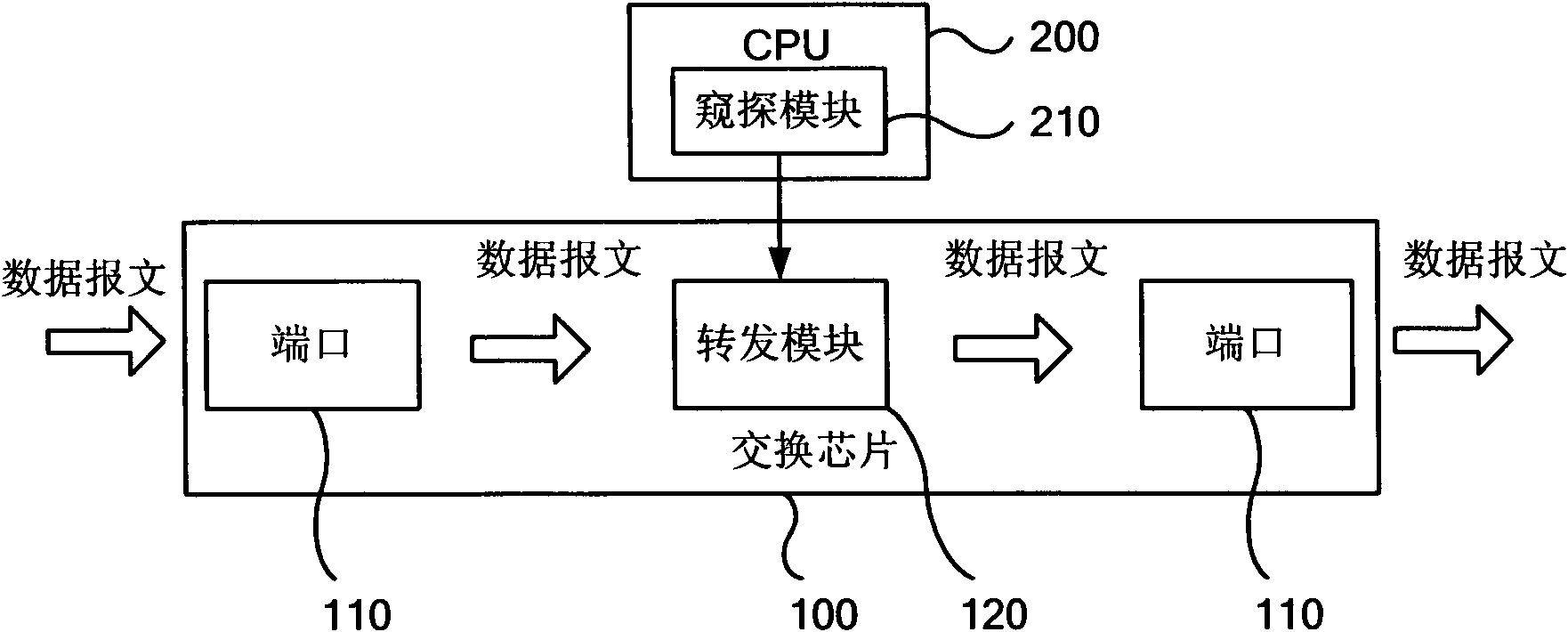
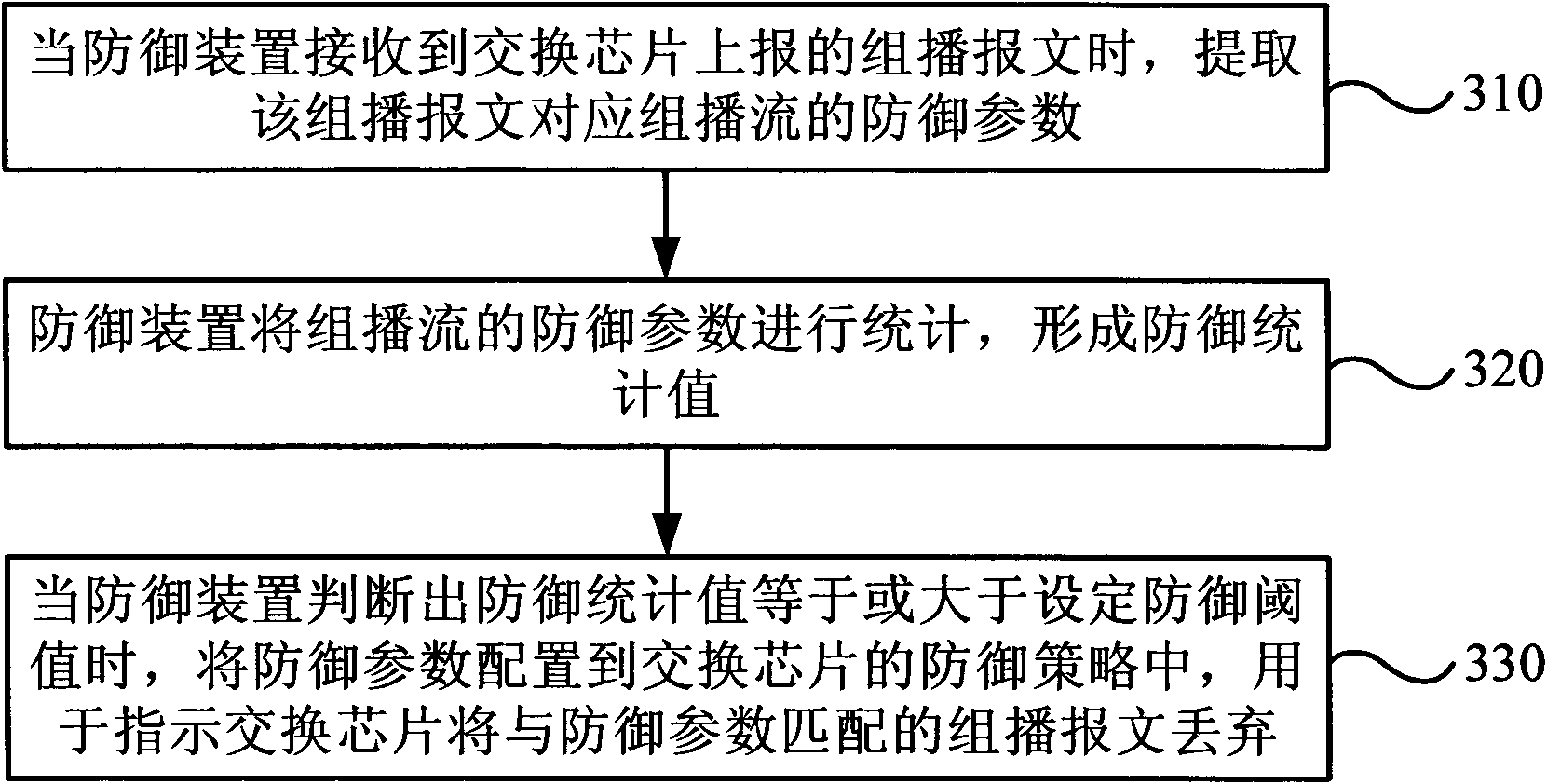
[0031] image 3 The flow chart of the multicast message processing method provided by Embodiment 1 of the present invention, this embodiment can be specifically executed by a Layer 2 switching device or a routing device supporting a Layer 2 switching function, wherein a defense device is added, and the defense device can be implemented by a CPU It can also be a control component independent of the CPU. The concrete process of this embodiment is as follows:
[0032] Step 310, when the defense device receives the multicast message reported by the switching chip, extract the defense parameters of the multicast flow corresponding to the multicast message;
[0033] Each multicast flow generally includes multiple multicast packets, and in step 310, the defense parameters of the multicast flow corresponding to the multicast packets are specifically extracted.
[0034] Step 320, the defense device counts the defense parameters of each multicast flow to form a defense statistics valu...
Embodiment 2
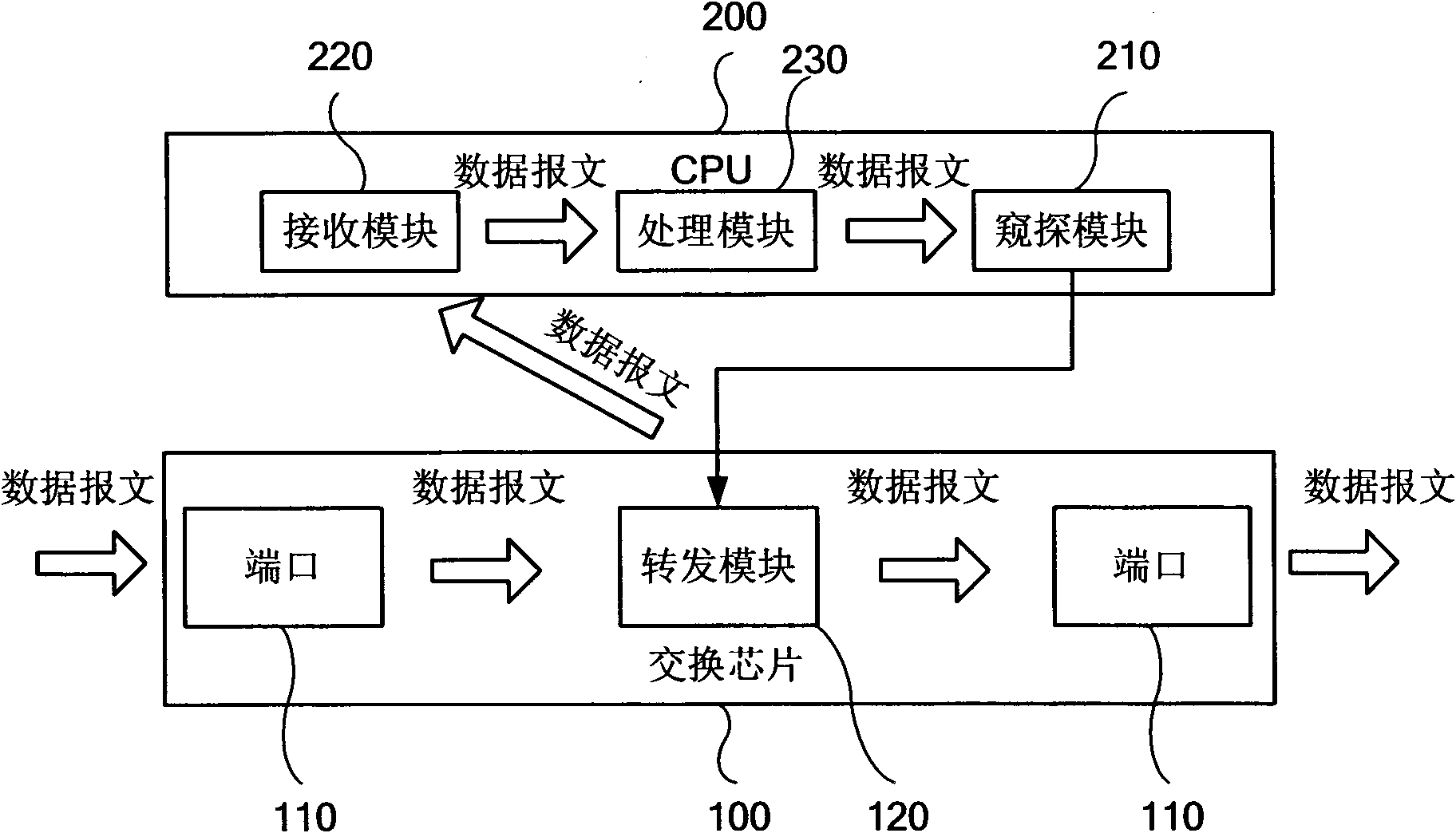
[0046] Figure 4 It is a flow chart of the method for processing multicast packets provided by Embodiment 2 of the present invention. On the basis of Embodiment 1, this embodiment further includes the following steps:
[0047] Step 410, when the defense device acquires the aging information of the multicast flow, delete the multicast flow from the defense statistics;
[0048] Step 420: When the defense device determines that the defense statistics value is lower than the set deletion threshold, delete the defense parameter from the defense policy of the switch chip.
[0049] In this embodiment, a dynamic deletion mechanism of defense policies is added. When a multicast flow ages out, that is, almost no packets of this multicast flow will be received, the defense statistics value can be reduced by one. When the defense statistic value decreases below the set deletion threshold, it means that the attack behavior corresponding to the defense parameter has basically ended or is ...
Embodiment 3
[0055] Figure 5 The flow chart of the multicast packet processing method provided by Embodiment 3 of the present invention, this embodiment provides a preferred example of implementing the solution of the present invention by a Layer 2 switching device, the Layer 2 switching device includes a switching chip and a CPU, and in the CPU It includes a multicast flow attack defense module and a snooping module (MLD Snopping). This defense module is equivalent to a defense device, which is used to collect statistics on multicast flow packets and determine whether to trigger the activation of defense strategies. The snooping module can create a multicast forwarding entry according to the multicast packet as a conventional operation. The defense strategy of this embodiment is illustrated by taking the defense parameter statistics of the receiving port and the host that initiates the message as an example. The defense parameters can be set in advance in the defense module as the receiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com