Access authentication method, equipment and system of P2P (peer-to-peer) network
A technology of P2P network and network equipment, applied in the field of access authentication of P2P network, can solve the problems of heavy workload of PKI certificate management, complex access authentication method and mechanism, complicated key management work, etc., and achieve easy access authentication work. , convenient encryption and decryption, the effect of simplifying the process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] In order to make the access authentication of the P2P network easier and simpler, the embodiment of the present invention provides an access authentication method of the P2P network. The network equipment in the P2P network adopts the IBC mechanism for access authentication. See figure 1 , the method includes:
[0035] 101: The local network device receives the access request sent by the peer network device. The access request carries the identity information of the peer network device and the first negotiation parameter. The identity information includes the identity of the peer network device and the private key of the peer network device. key level;
[0036] 102: According to the private key level of the local network device and the private key level of the peer network device, select one of the private keys of the local network device as the session private key of the local network device;
[0037] 103: Calculate the local network address based on the session priva...
Embodiment 2
[0041] In order to make the access authentication of the P2P network easier and simpler, the embodiment of the present invention provides an access authentication method of the P2P network, and the network equipment in the P2P network adopts the IBC mechanism to perform the access authentication.
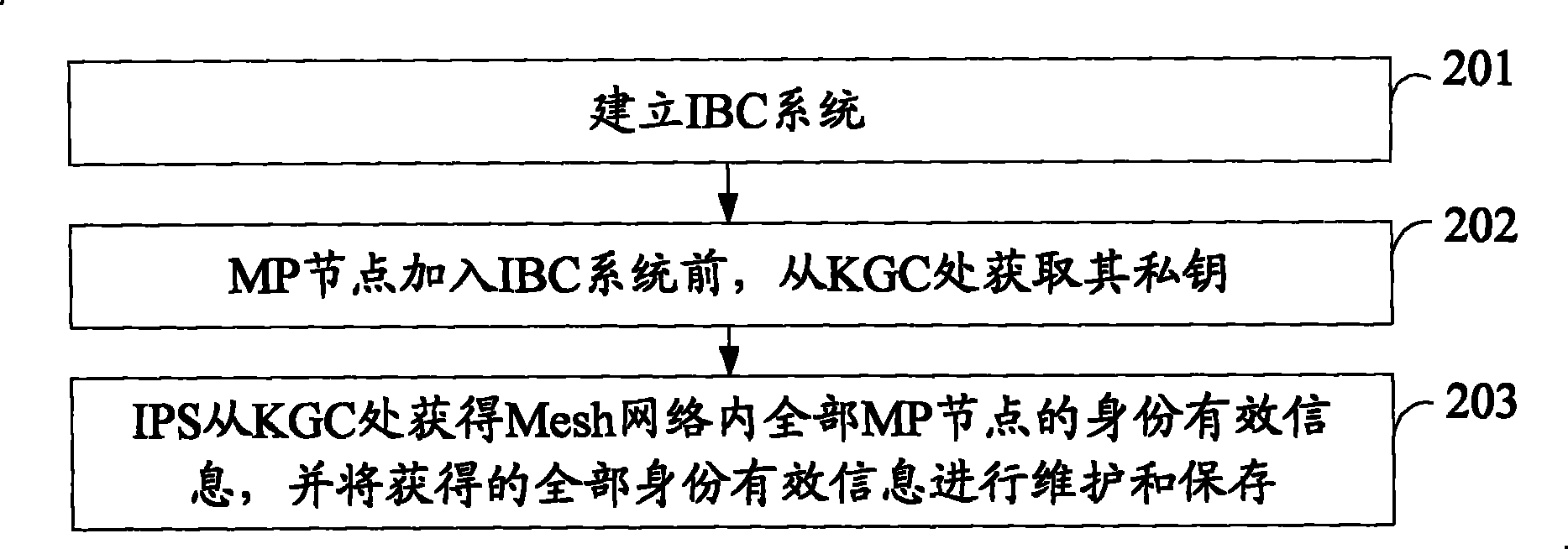
[0042] Take Mesh as an example of a typical P2P network, see figure 2 , the preparations for the access authentication method of the P2P network include:
[0043] 201: Establish an IBC system.
[0044] (1) Generate system parameters by an offline trusted organization KGC (Key Generation Center, key distribution center) params = G 1 , G 2 , q , e ‾ , P , H 1 , H 2 , H > ...
Embodiment 3
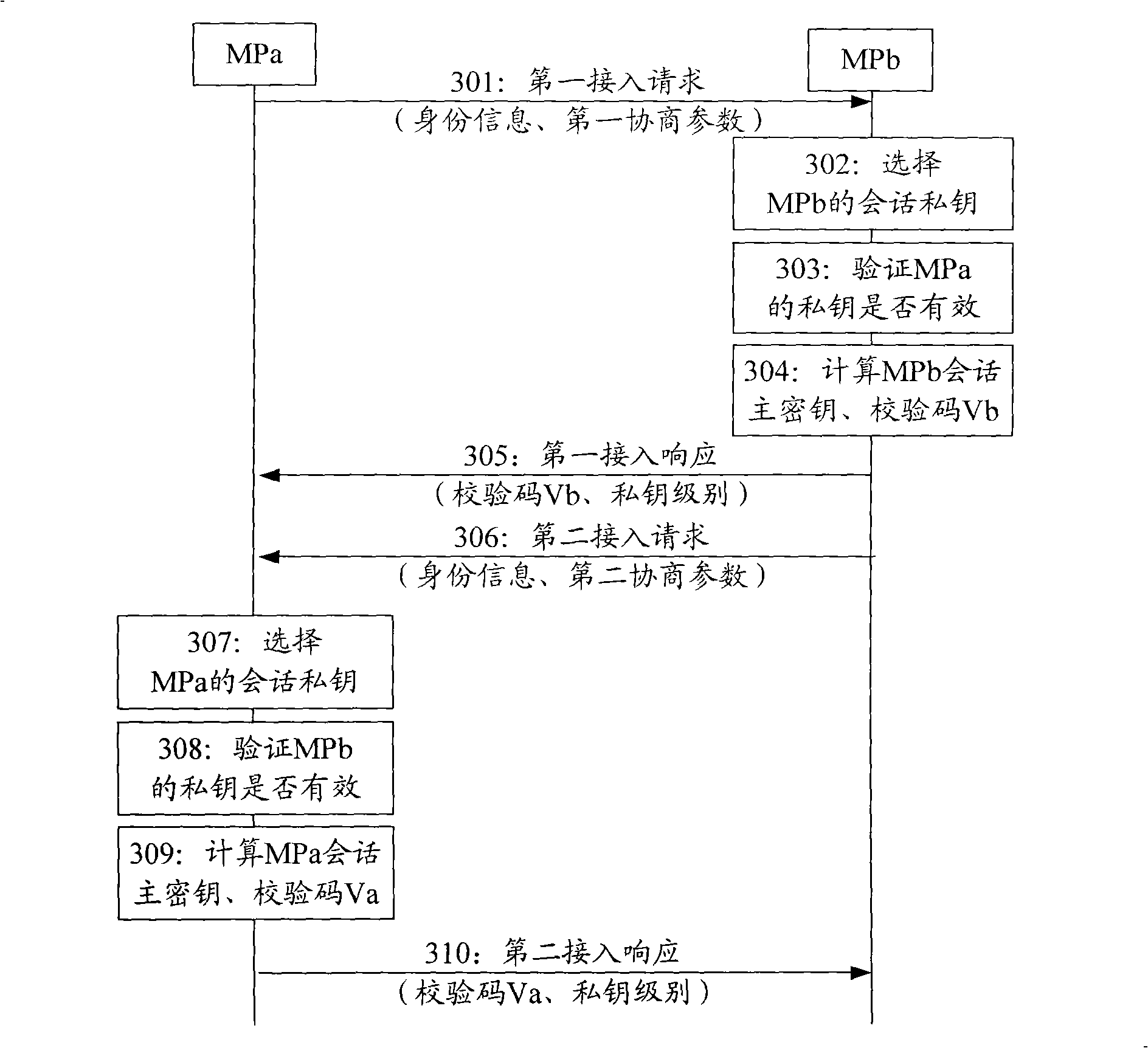
[0150] In order to make the access authentication of the P2P network easier and simpler, the embodiment of the present invention provides an access authentication method of the P2P network, and the network equipment in the P2P network adopts the IBC mechanism to perform the access authentication. For the convenience of discussion, it is assumed that the local network device MPb has a private key Pri_Keyb, whose private key level is SN1, and the peer network device MPa has two private keys Pri_Keya0 and Pri_Keya1, whose private key levels are SN0 and SN1 respectively. The access authentication methods include, refer to Figure 4a , Figure 4b :
[0151] 401: Node MPb receives an access request sent by node MPa, where the access request includes: the identity of MPa, all private key levels, and first negotiation parameters corresponding to the private key levels.
[0152] The first negotiation parameter can be: (a×Pub_Keya), wherein, the first random number a is a random numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com