Arithmetic circuit for montgomery multiplication and encryption circuit
一种运算电路、乘法的技术,应用在运算电路领域
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
other Embodiment approach
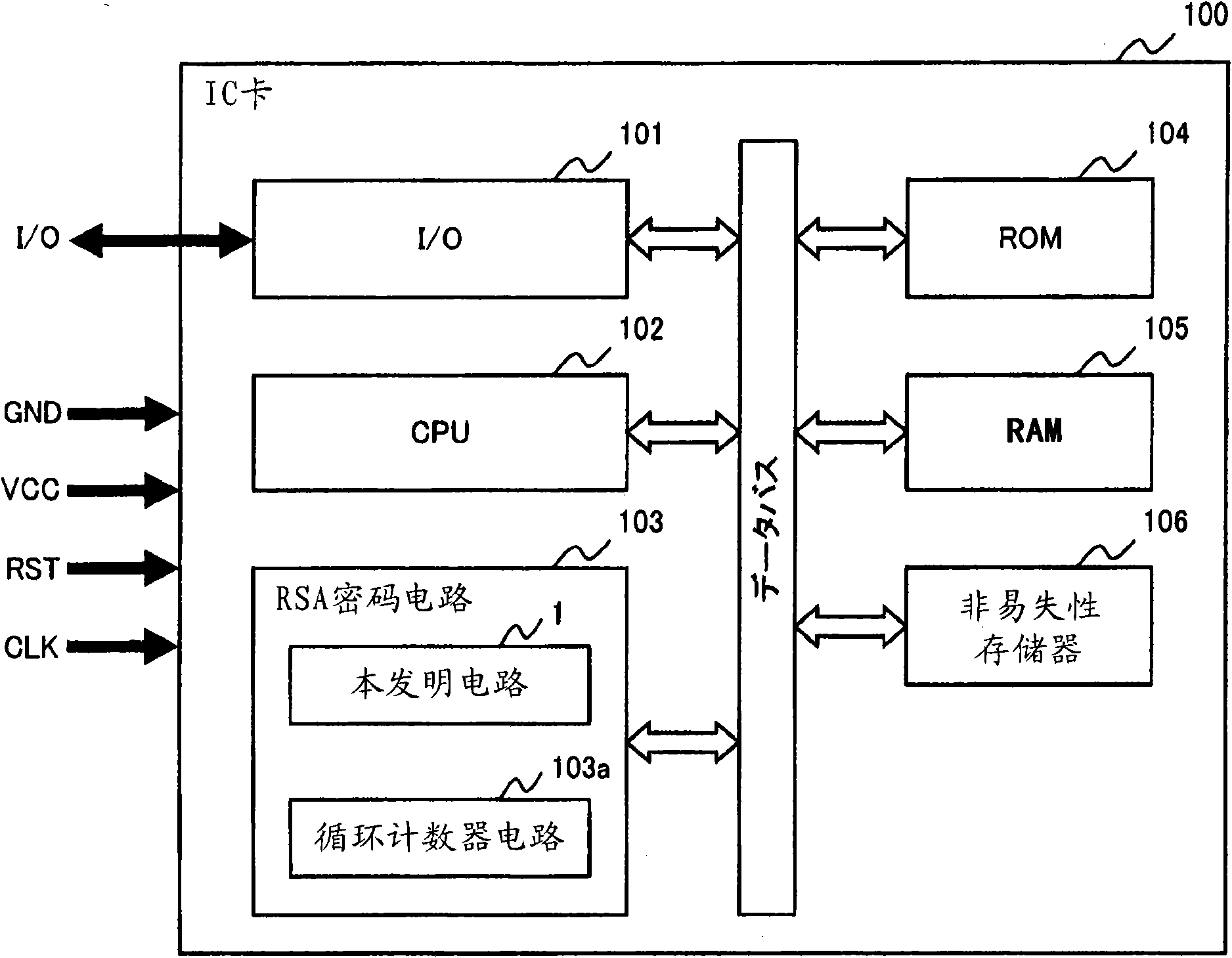
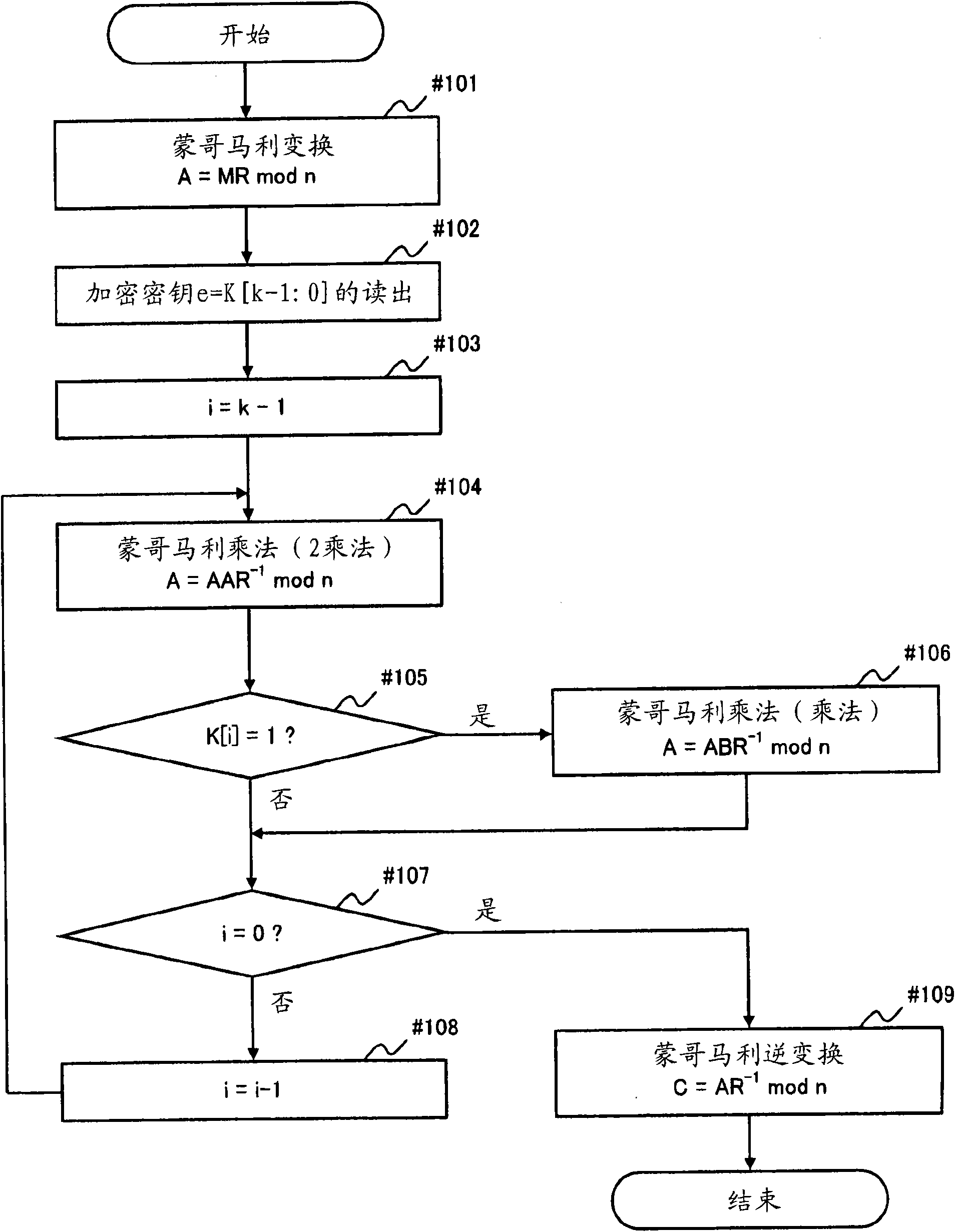
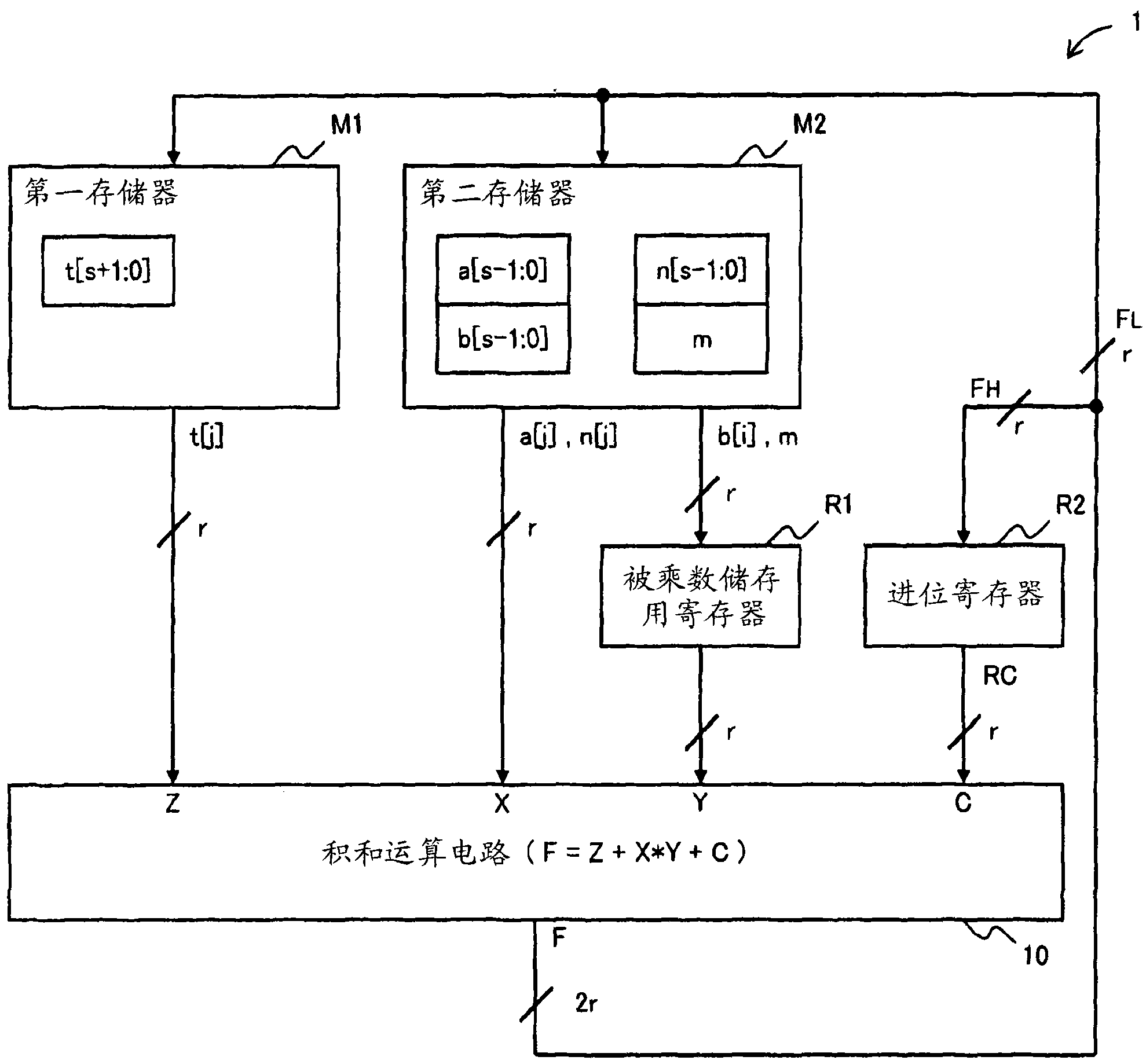
[0074] (1) In the above-mentioned embodiment, the case where the RSA encryption circuit 103 is mounted on the IC card 100 and the encryption process is performed using the circuit 1 of the present invention has been described. In the circuit 103 and the like, decryption processing is performed using the circuit 1 of the present invention.
[0075] (2) In the above embodiment, the case where the circuit 1 of the present invention is used in the RSA encryption circuit 103 has been described, but it can also be used in other encryption circuits or arithmetic circuits using Montgomery multiplication.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com