Method for realizing calling authentication gateway
An authentication and gateway technology, applied in the field of call authentication gateway, can solve the problems of high risk, complex implementation and operation, and large investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
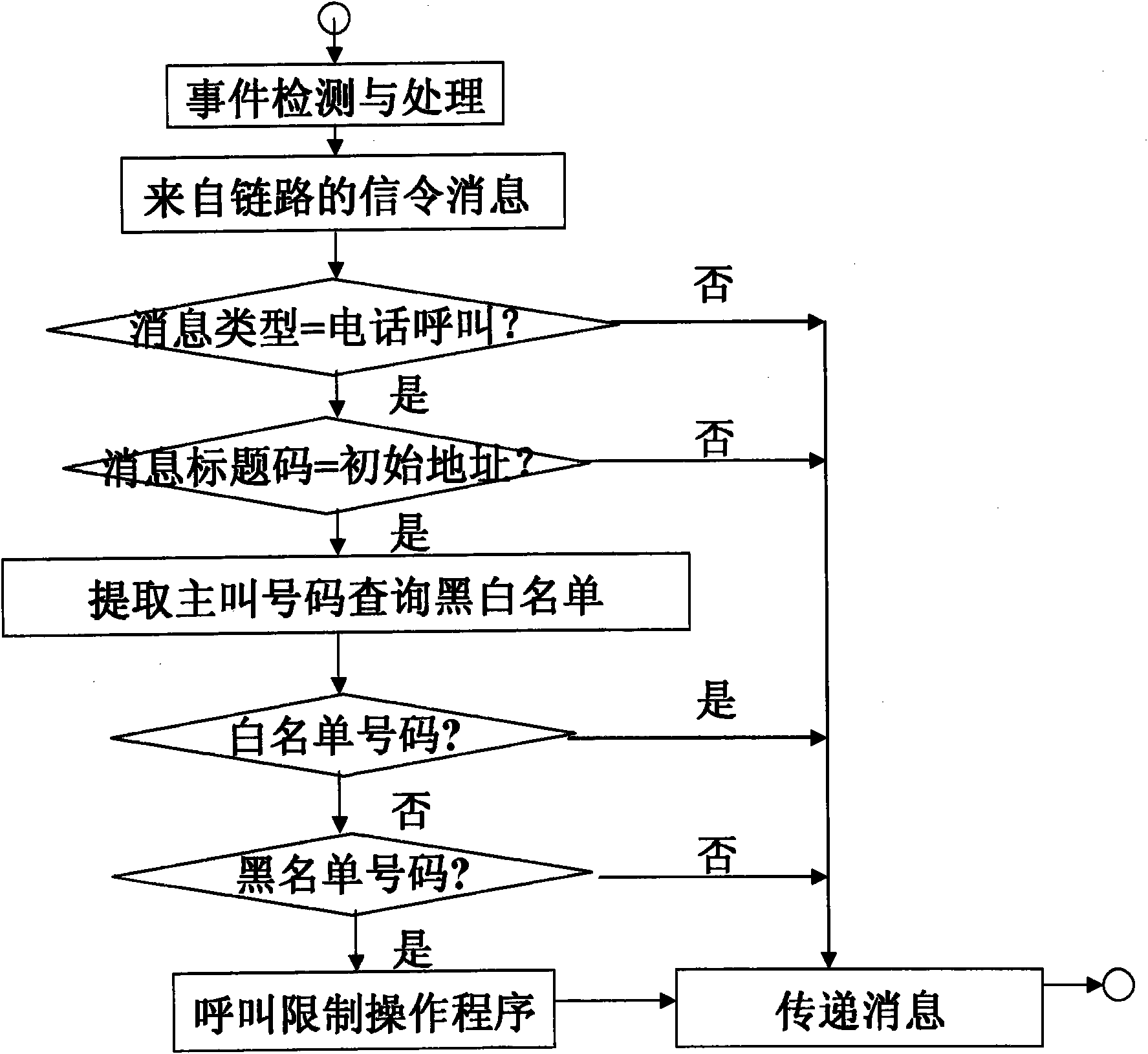
[0009] figure 1 It is a schematic diagram of the service flow realization of the call authentication gateway. The analysis processing steps are as follows:
[0010] First deploy the call authentication gateway system, and the MPM is serially connected to the relevant signaling links that require call authentication in a non-signaling point coding working mode. The system enters the working state:
[0011] The first step: detecting the signaling message in transmission, and when it is recognized that the type of the signaling message is a telephone call, then enter the call authentication analysis processing program of the second step, otherwise pass the signaling message;
[0012] Second step: detect the title code of the signaling message, if it is not the initial address message, then pass the signaling message; if it is the initial address message, then extract the calling number, and use the calling number as an index to query the black and white list data table, Divide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com