Inter-system subscriber identity authentication system and method
A user identity and verification system technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve problems such as unfavorable work efficiency, increase user operations, and user session expiration, so as to reduce login verification operations and secure the system. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
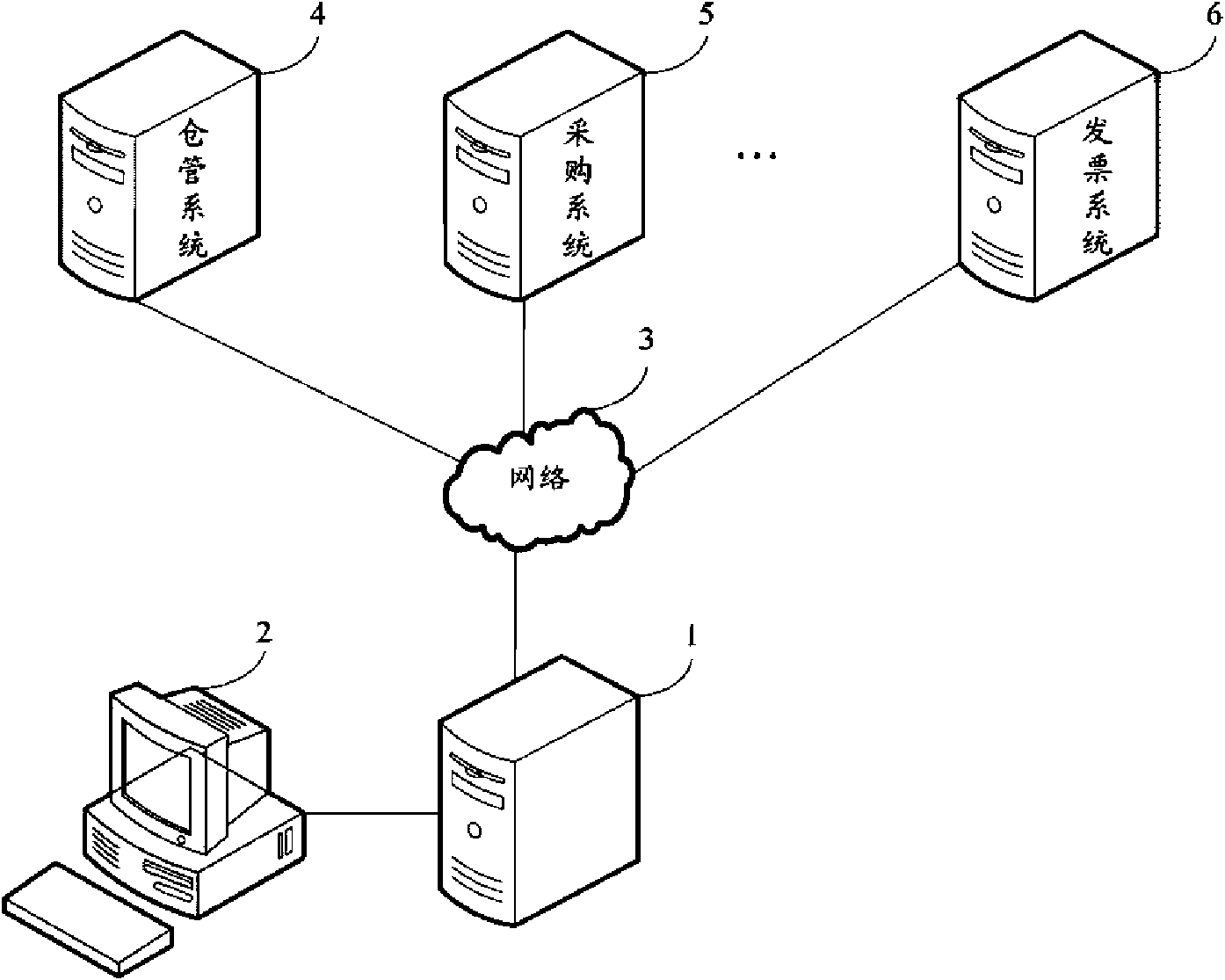
[0012] refer to figure 1 Shown is an implementation environment diagram of a preferred embodiment of the cross-system user identity verification system of the present invention. The cross-system user identity verification system 10 runs in an application server 1 and is used to realize cross-system user identity verification. The application server 1 is connected to a plurality of application systems through a network 3, such as a warehouse management system 4, a purchasing system 5, and an invoice system 6, etc. The multiple application systems may run on the same web server, or may run on different web servers, figure 1 shown in , running on a different web server. The network 2 can be an enterprise intranet or the Internet.
[0013] The application server 1 is also connected with at least one client computer 2, which provides a user interface for logging into the above-mentioned multiple application systems.
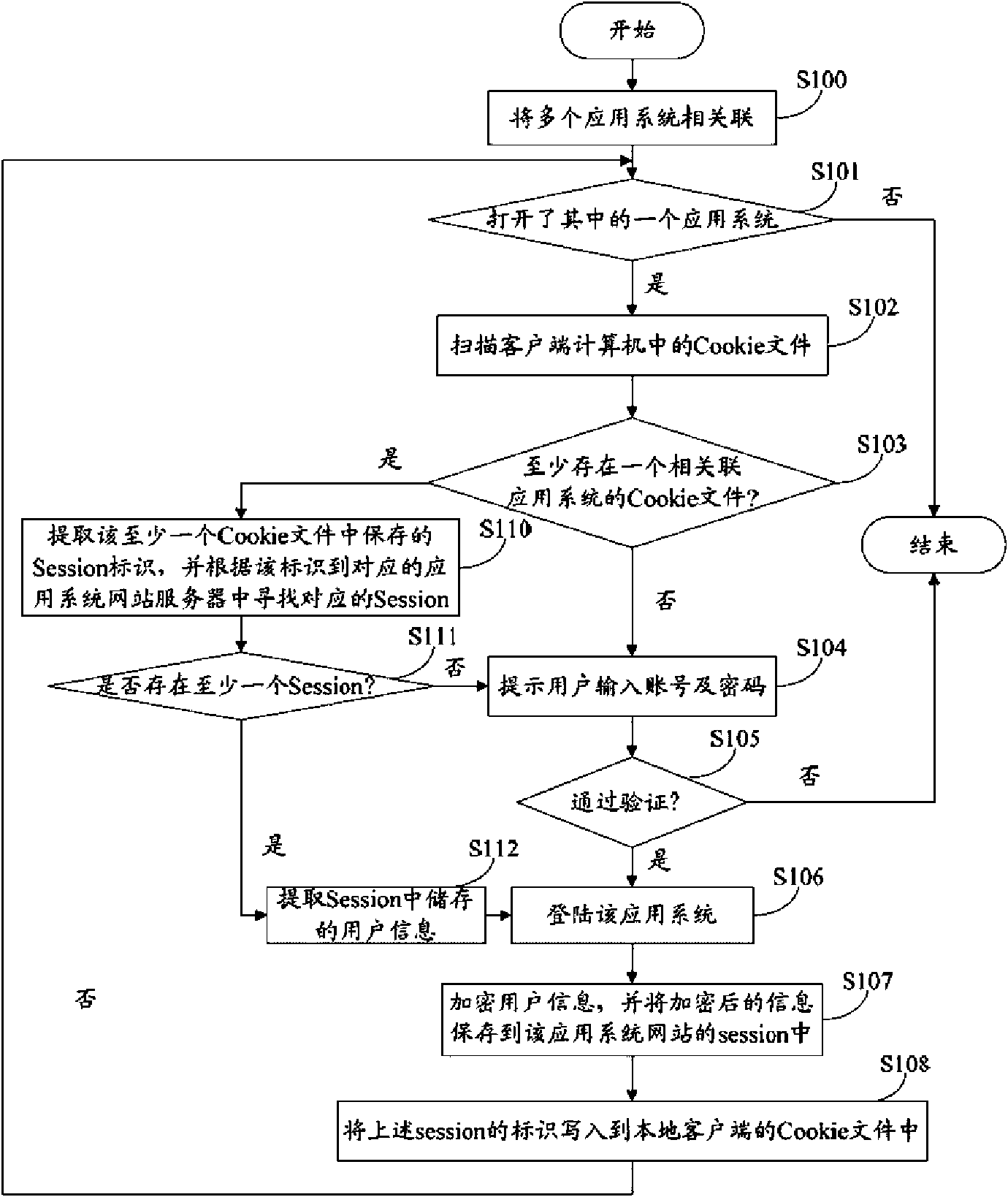
[0014] refer to figure 2 As shown, it is a functional bloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com