Security guarantee method and system for Windows terminals based on auto white list
A terminal security and whitelist technology, applied in the field of information security, can solve problems such as privilege escalation, misappropriation, frequent upgrades, etc., to achieve the effect of prohibiting invisible Trojan horses, improving terminal security, and expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
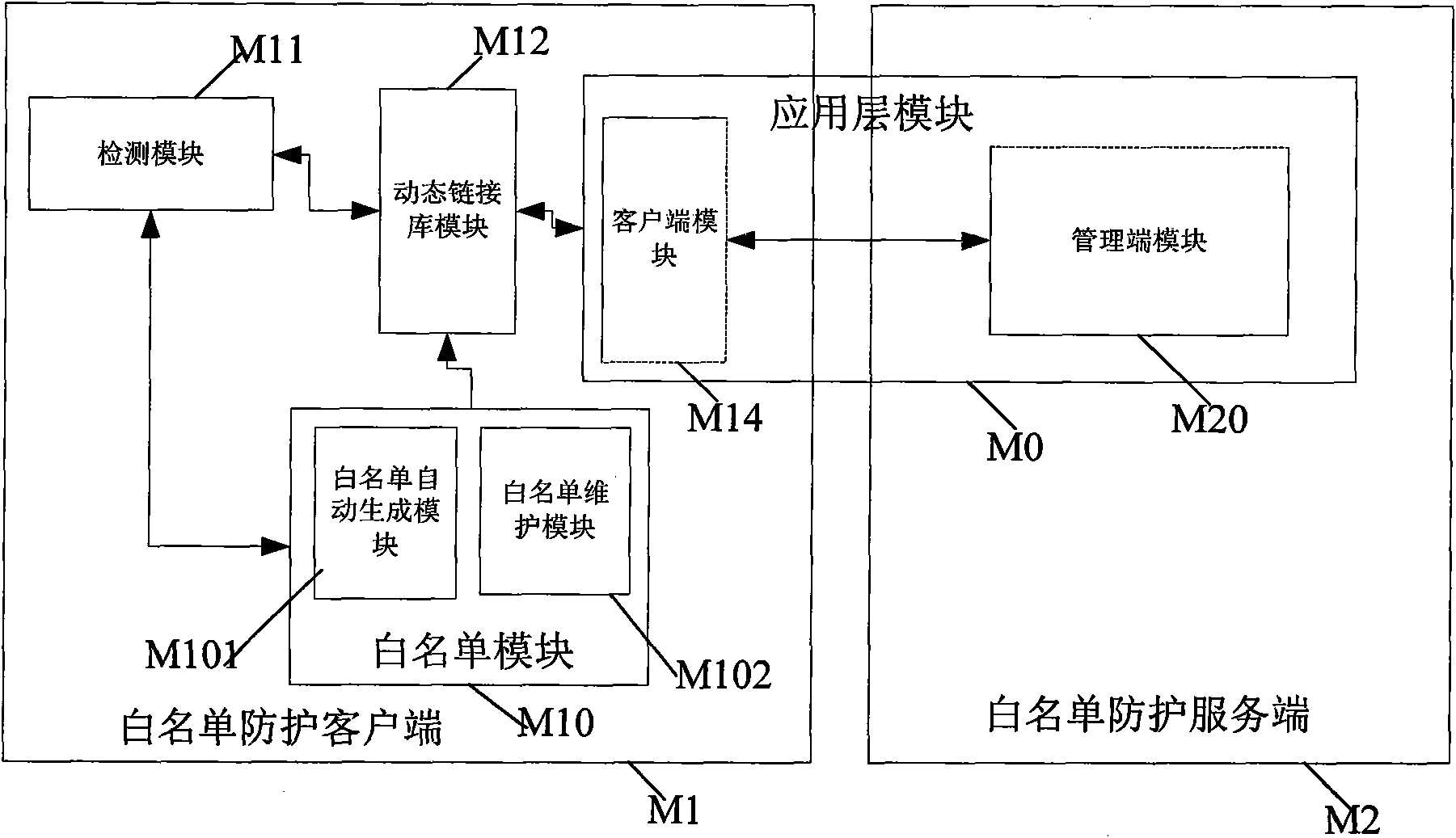
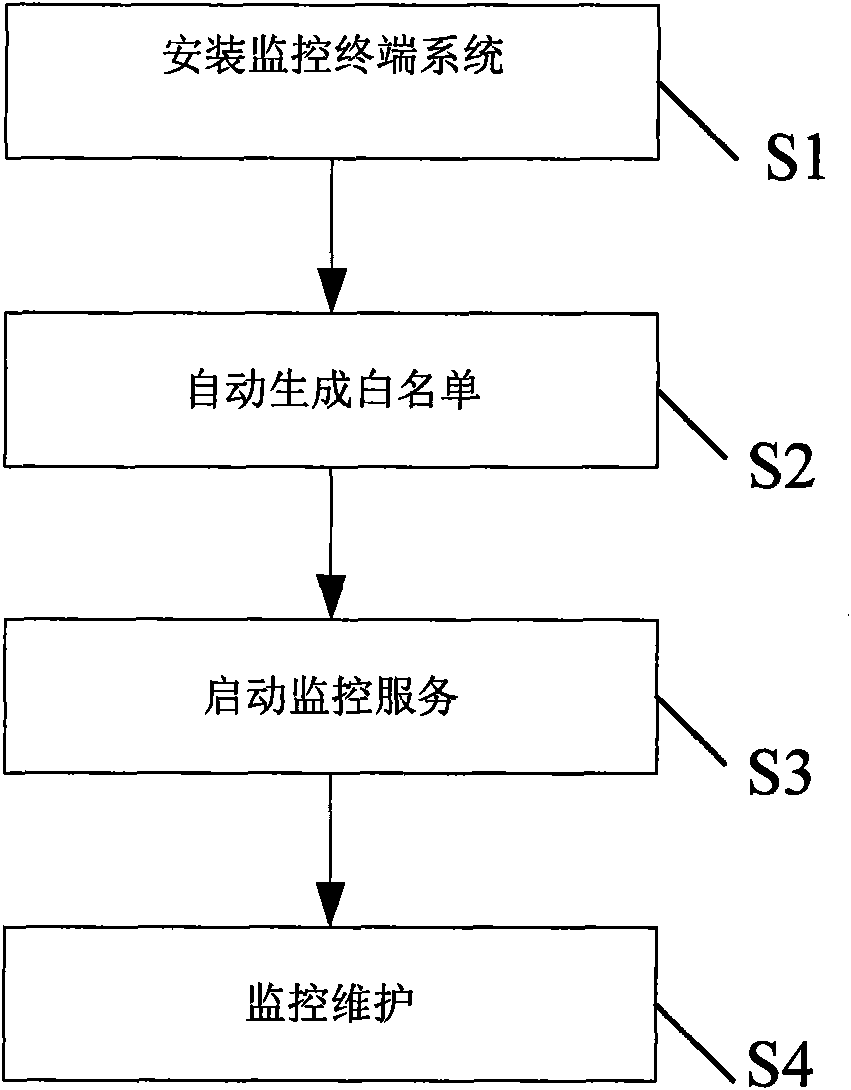
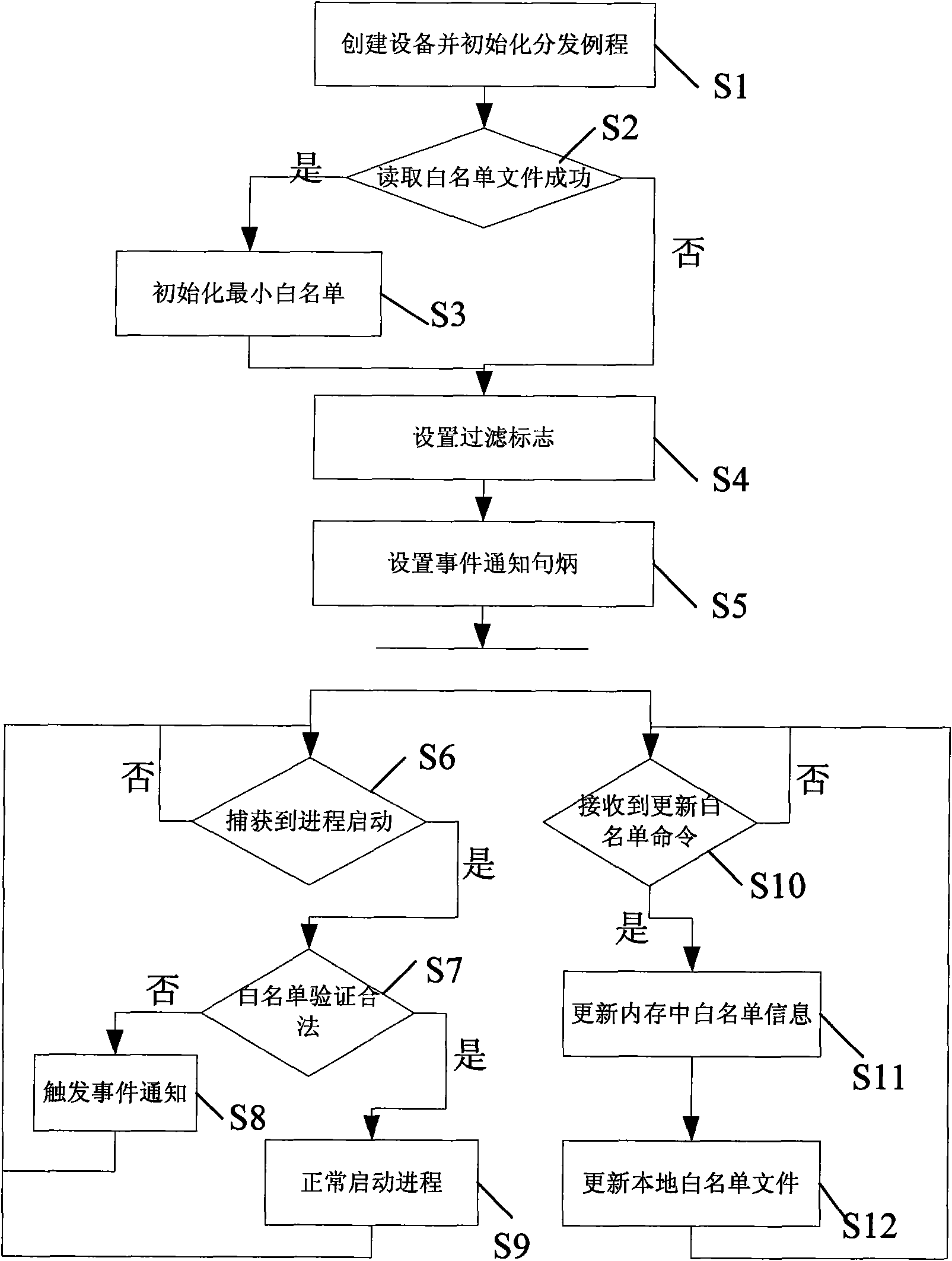
[0028] The core idea of the present invention is to construct a Widows terminal security guarantee system based on an automatic whitelist, and the whitelist that the system relies on is automatically generated by the system by scanning the local hard disk during installation. After the system is successfully started, it captures the operation of the startup process of the kernel, and verifies whether the executable program that the process to be started depends on is completely consistent with the whitelist record, otherwise the startup operation is terminated; the privileged user can modify the whitelist through the remote or local management module. list information, but cannot directly modify or delete the whitelist file; in addition, the end user cannot force stop the system, and can only uninstall the system in safe mode after entering the correct PIN code (ie system ID number); new installation The system can continue to process the security alarm information left by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com