A method to respond to TOCTOU attacks against TPM trusted computing in the environment of multiple virtual domains
A trusted computing and virtual domain technology, applied in computing, computer security devices, instruments, etc., to achieve strong scalability, maintain effective utilization, and defend against TOCTOU attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
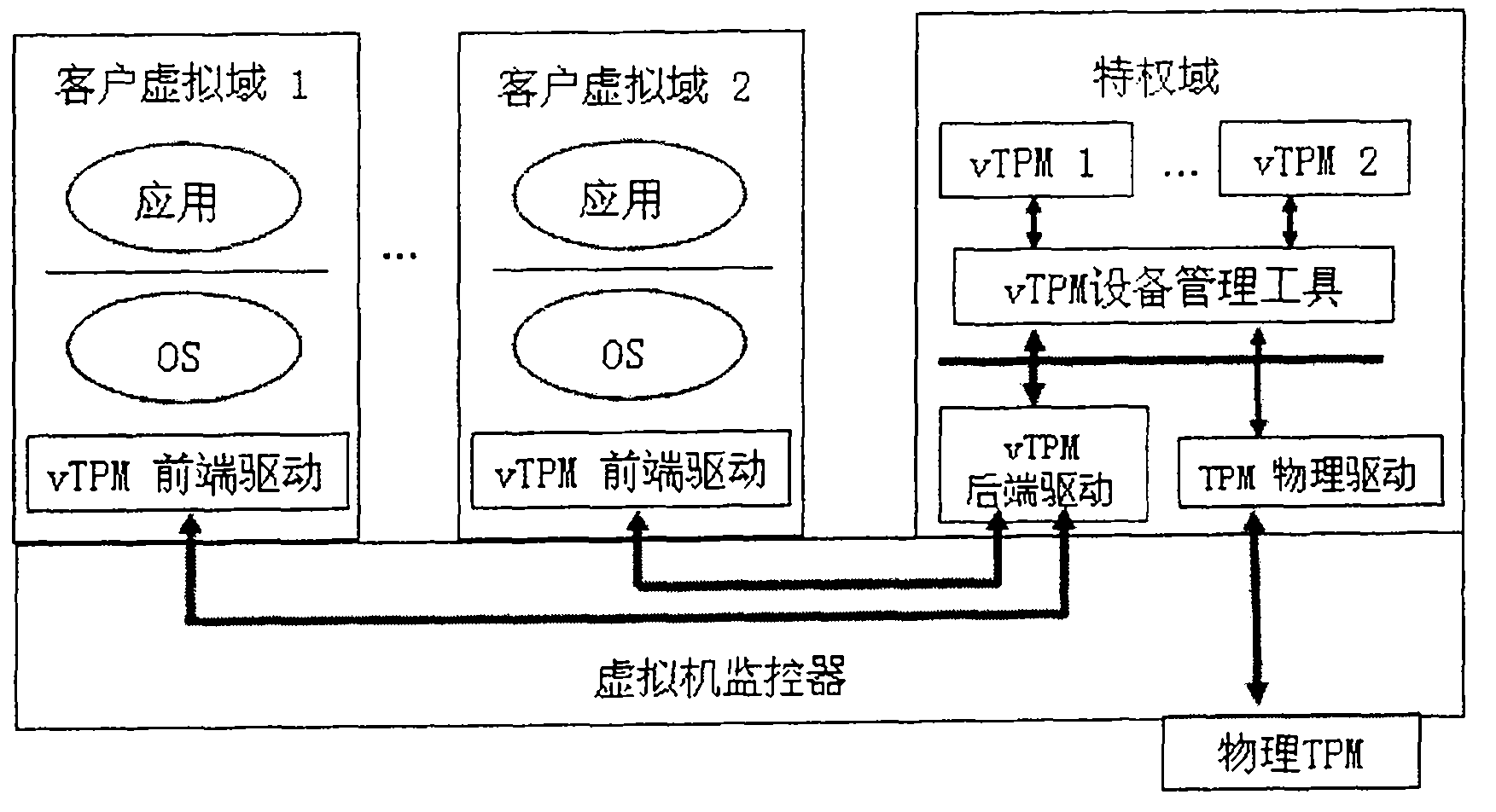
[0023] The invention assumes figure 1 The system has been deployed, and the deployment steps of the response method of the present invention are provided below:
[0024] Step 1, integrate the memory monitoring module into the virtual machine monitor, then increase T_hypercall and T_vIRQ in the virtual machine monitor and the privileged domain kernel, and finally restart the computer.
[0025] Step 2, replace the virtual domain management tool with enhanced functions figure 1 Method provides virtual domain management tools.
[0026] Step 3, replace the vTPM device program with enhanced functions figure 1 method provided by the vTPM device program.
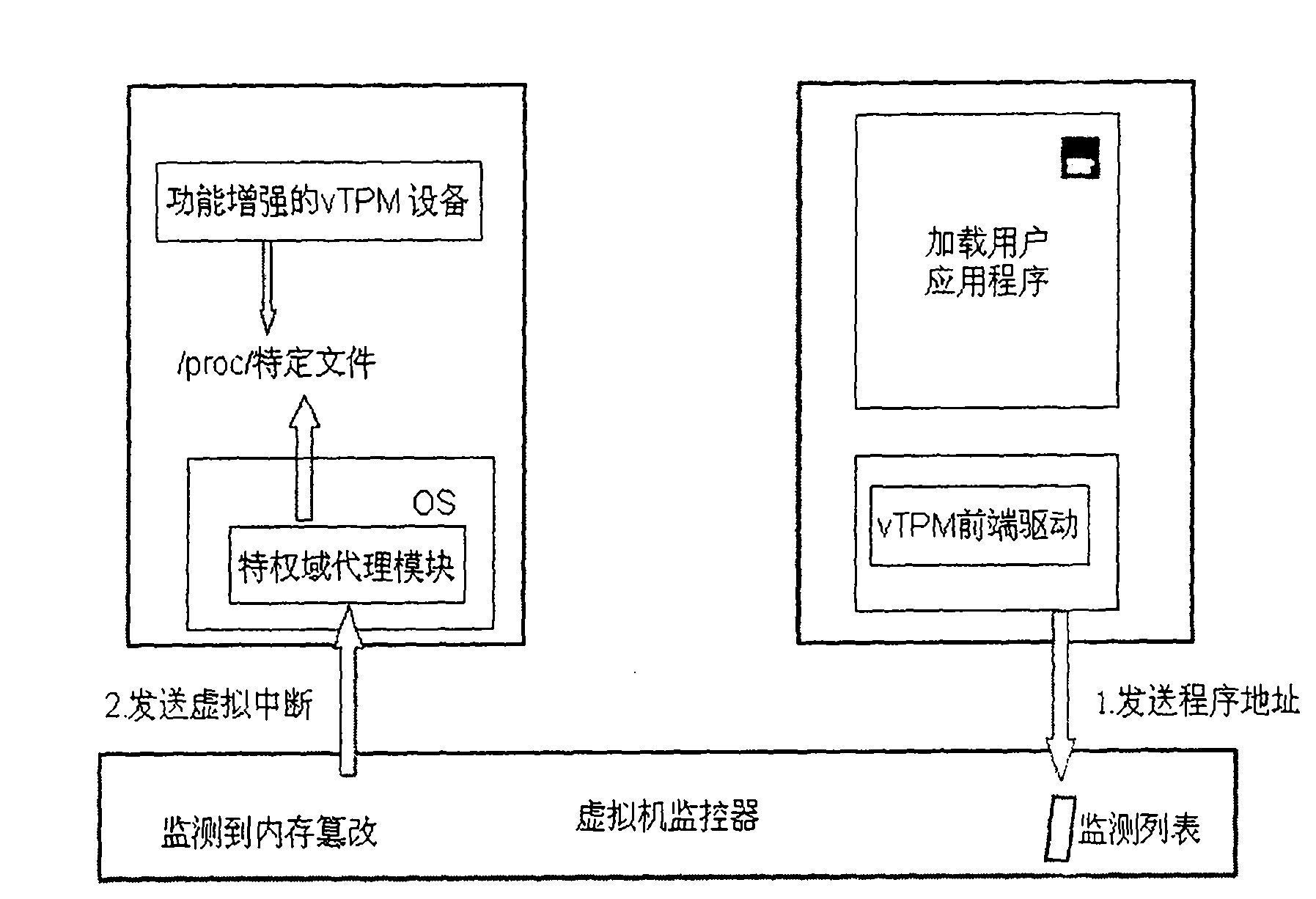
[0027] Step 4, loading the privileged domain agent module in the privileged domain.
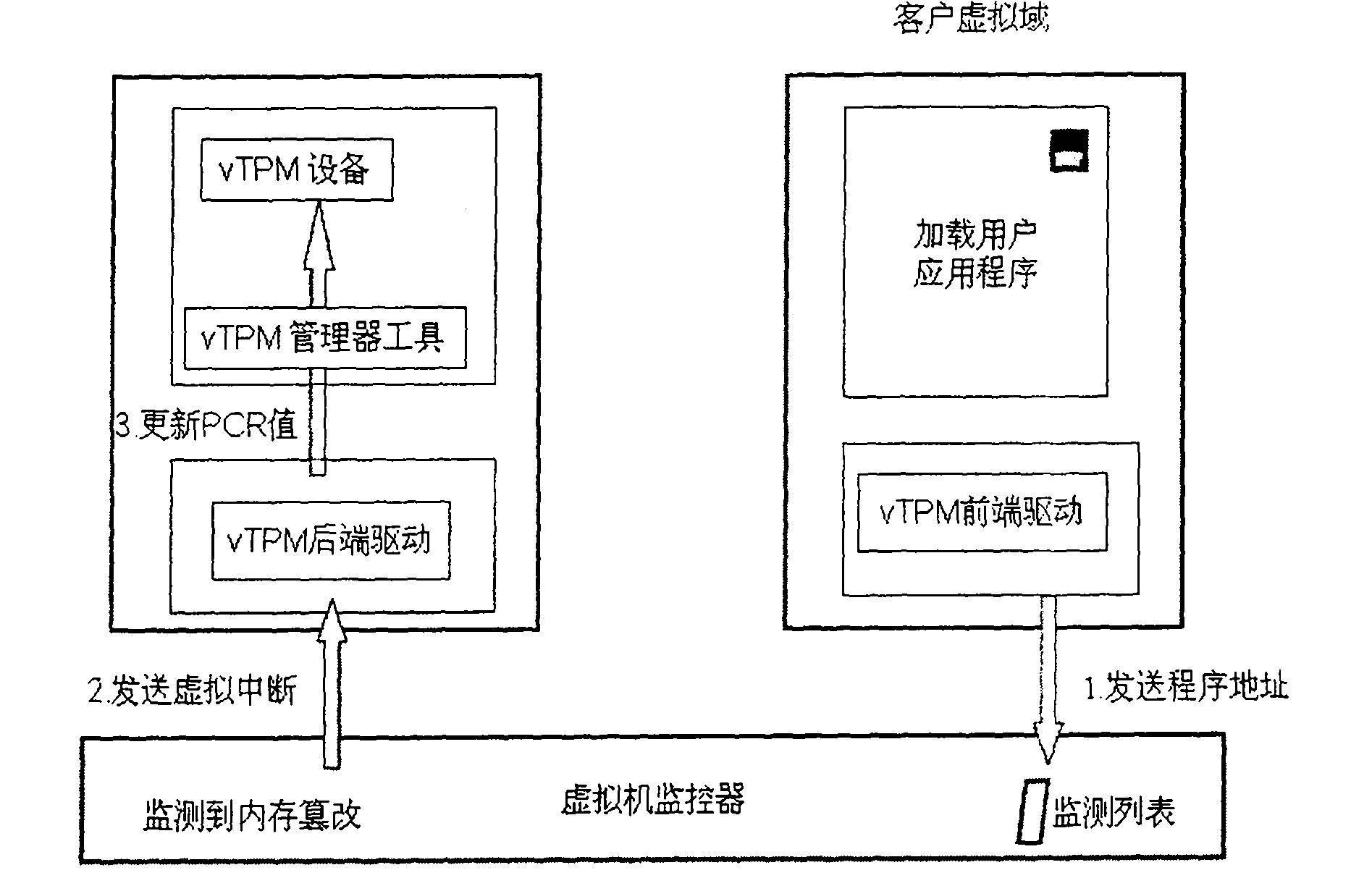
[0028] Combine below Figure 5 with Image 6 The workflow of the present invention's design TOCTOU attack response method is described in detail:
[0029] (1). In the privileged domain, start the virtual domain through the enhanced virtual d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com