Method and protecting apparatus for defending denial of service attack
A denial of service attack and protection device technology, applied in the field of network communication, can solve the problems of difficult server protection, unrealistic scanning, and high processing cost, and achieve the effect of defending against denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
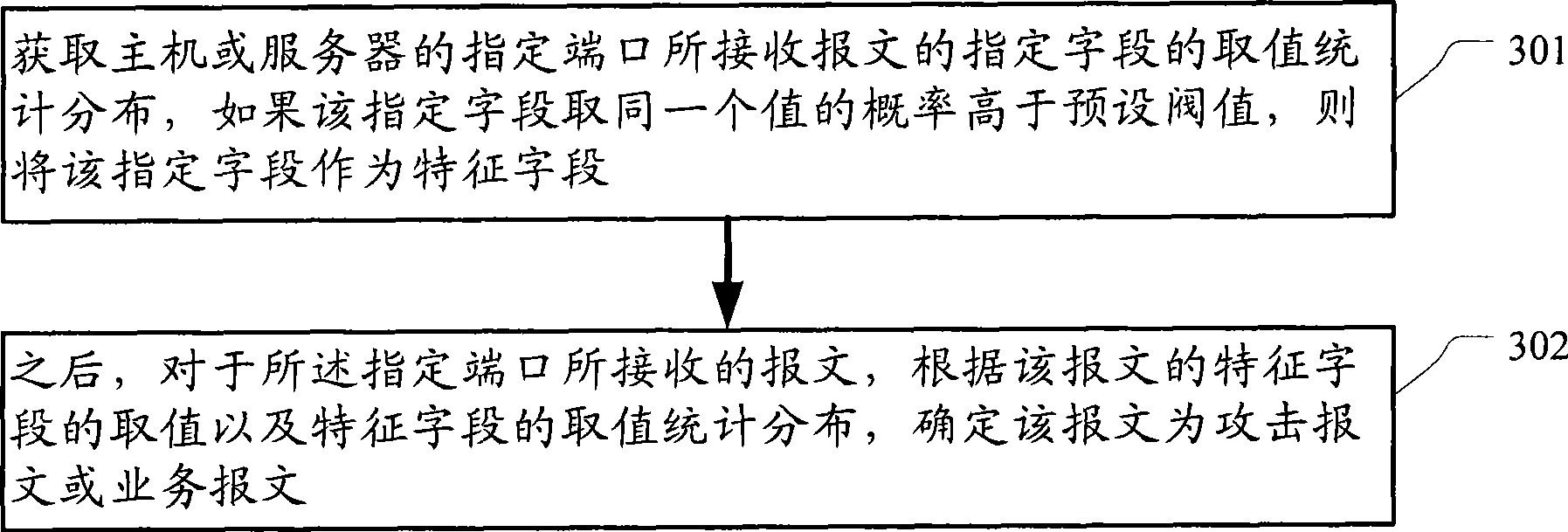
[0037] Embodiment one: count the service flow of a certain service port (herein referred to as port A) of the protected host or server (comprising five-tuple information including protocol number, source IP, source port, destination IP and destination port are the same The statistical distribution of the value of each byte in the first 16 bytes of the first message), if the probability of a certain byte in the 16 bytes taking the same value is greater than the preset value, such as 80 %, the byte is regarded as a feature word.
[0038] For example, the statistical distribution of the values of the first 16 bytes of the first packets of 1237 HTTP service flows on port A is counted. Here, the threshold is set to 90%, and the probability that the first 5 bytes take the same value is found. More than 90%, as follows:
[0039] Byte[i]--->>>
[0040] count / total:value
[0041] Byte[0]--->>>
[0042] 1173 / 1237:71 29 / 1237:80 18 / 1237:60 2 / 1237:0 2 / 1237:112 2 / 1237:115
[0043] 2 / ...
Embodiment 2
[0066] Embodiment two: count each byte of the first 16 bytes of all messages of the service flow of a service port (comprising protocol number, destination IP address and destination port identical message collection) of a protected host or server Statistical distribution of the value of , if the probability of a certain byte in the 16 bytes taking the same value is greater than the preset value, the byte is regarded as a feature word.
[0067] For example, statistical distribution of the values of the first 16 bytes of packets whose destination port is server port 8000 is found to be relatively concentrated in the values of the first 4 bytes, as shown below:
[0068] FlowNum=329, PacketNum=1502 Explanation: 329 service flows are counted, and the total number of packets is 1502.
[0069] Byte[i]--->>>
[0070] count / total:value
[0071] Byte[0]--->>>
[0072] 1202 / 1502:2 169 / 1502:3 49 / 1502:56 36 / 1502:254 21 / 1502:0 21 / 1502:4 4 / 1502:1
[0073] Byte[3]--->>>
[0074] 118...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com