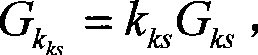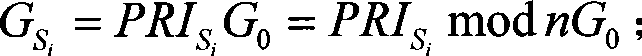Large cluster safe real-time communication method executed by using elliptical curve
An elliptic curve, secure technology, applied in the direction of calculation using residual algorithm, public key for secure communication, calculation using non-number system representation, etc., can solve high signature/verification costs, multiple CPU cycles, CA paralysis, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
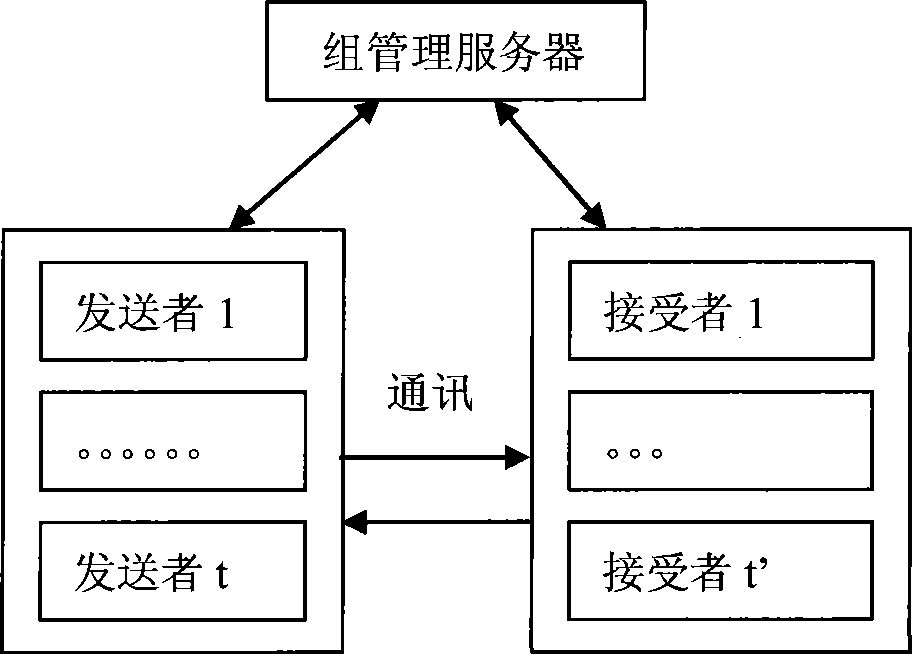
[0036] Such as figure 1 As shown in the schematic diagram of multicast group communication, the group management server is the security center of the entire system and a network entity trusted by both senders and receivers, responsible for the management and distribution of security materials.
[0037] A large cluster security real-time communication method using elliptic curves, the specific steps are as follows:
[0038] Step 1: Initialize the distribution group
[0039] (1) The group management server GCKS creates an elliptic curve T in the finite field P;
[0040] (2) Define two sets of prime numbers as the first set of prime numbers SINIT and the second set of prime numbers RINIT, and create the first set of prime numbers SEN init And put it into the first prime number set SINIT to create the second prime number REG init And put into the second prime number set RINIT;
[0041] (3) Take the first base point G from the elliptic curve T ks and the first private key k k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com