Authorization method, system and apparatus
An authorization certificate and client-side technology, which is applied to user identity/authority verification and key distribution, can solve the problems that the client cannot use digital content, the client cannot obtain the key, and the user cannot use digital content, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
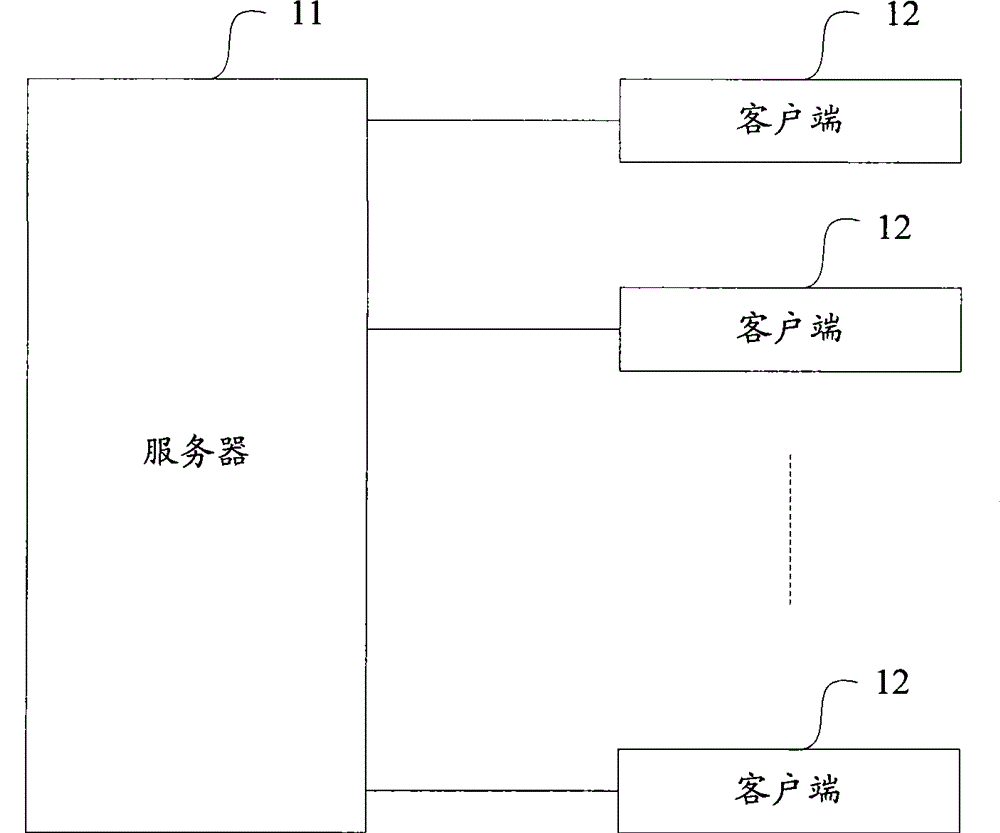
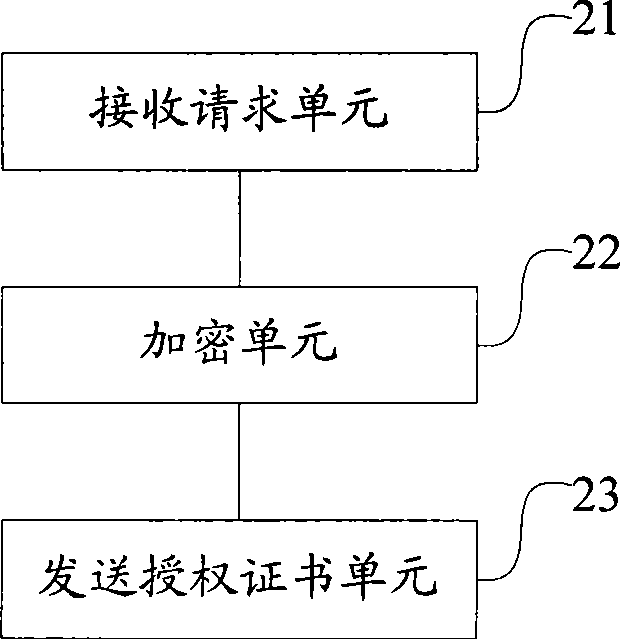
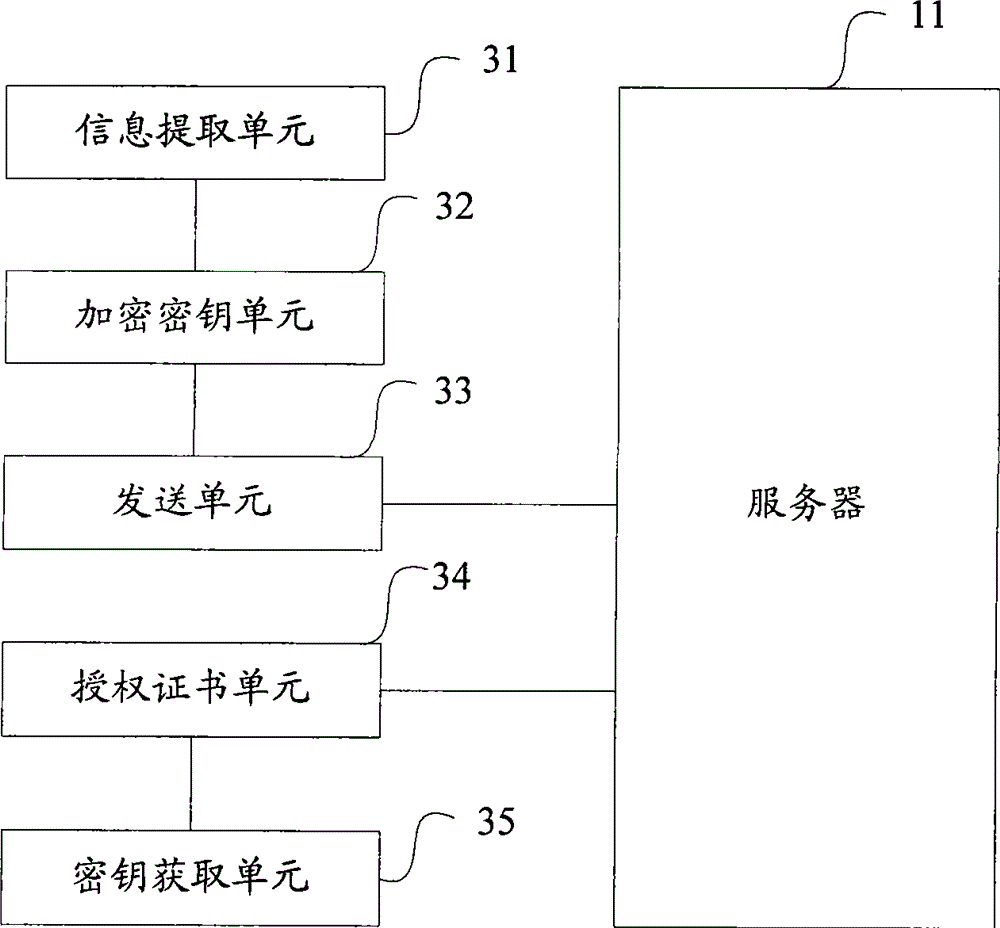
Image
Examples
Embodiment 1
[0064] An e-reader manufacturer needs to pre-install DRM-protected digital content in a batch of readers without expansion memory cards. First, multiple authorization schemes are preset in the universal reader client and the authorization server. The authorization scheme with higher priority is: bind the device number of the e-reader and the card number of the expandable memory card with the digital content at the same time, and the authorization scheme with lower priority is: bind the digital content with the device number only. The authorization server encrypts the protection key of the digital content according to the characteristic information of the batch of clients; and then describes the type of the characteristic information of the batch of clients and the encrypted content key in the authorization certificate. The authorization certificate can be used by the batch of e-readers.
Embodiment 2
[0066]Device feature information types with different priorities and corresponding device feature information are pre-set on an authorization server and multiple PC devices, so that a certain e-book DRM protection system can support these special PC devices. Because on a PC, the hardware usually used for binding, such as graphics card, network card and other devices, may not exist, and the serial number of the hard disk may not be detected, so it is necessary to preset multiple sets on the client software with priority for these characteristics. The feature information extraction scheme. For example, first extract the hard disk, network card, and graphics card, and then extract the motherboard, CPU, and memory, and then use the above-mentioned 6 kinds of device numbers that can be extracted, and use such as "hardware adaptability method" for binding. For example, when a user's PC does not have a network card, the user purchases an e-book through the PC. After obtaining the RO...
Embodiment 3
[0071] When an e-book DRM protection system supports mobile phones in addition to PC devices, after the client obtains the RO certificate issued by the server, it knows that its own device is a mobile phone by detecting the device type, and knows the corresponding IP address of the mobile phone according to the predetermined plan. The type of client feature information, and detect and obtain the corresponding client feature information (such as SIM card number, mobile phone device number, etc.), and send it to the RO authorization server together with the RO certificate. After the RO authorization server judges the validity of the RO credential, it will encrypt the protection key of the digital content according to the client’s characteristic information, add it together with the client’s characteristic information type to the generated authorization certificate, and The certificate is returned to the phone. After the mobile phone obtains the authorization certificate, save it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com