Access control method and device based on semantic relation reasoning of users and resources
An access control and resource technology, applied in the access control field of semantic relational reasoning, can solve problems such as complex authorization management, achieve dynamic authorization, meet access control requirements, and solve the effect of complex authorization management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
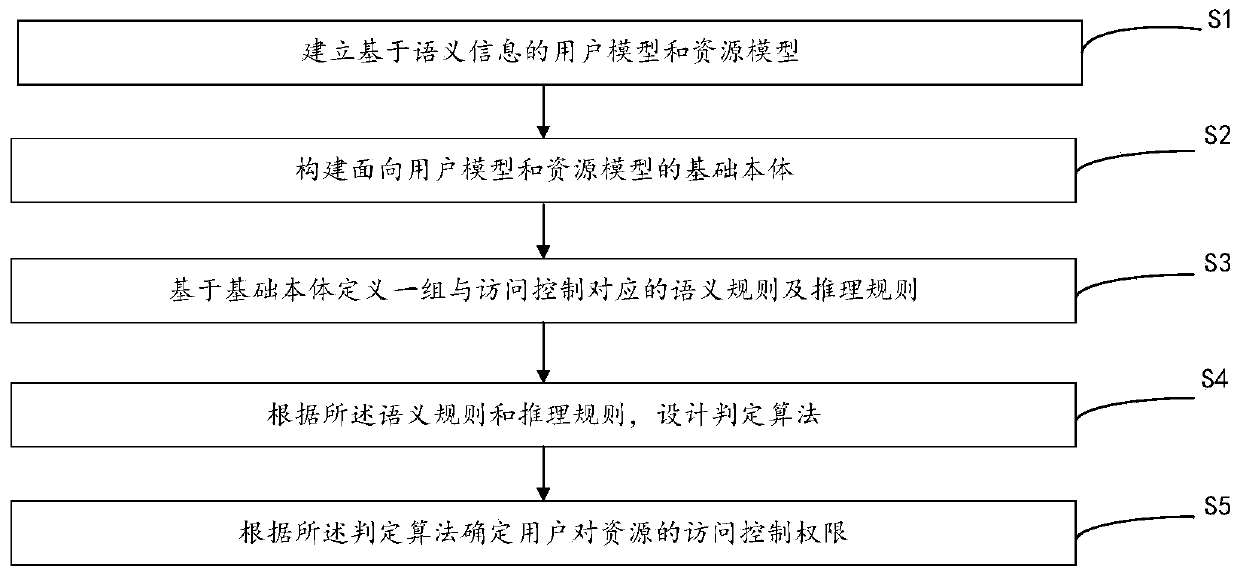
[0053] This embodiment provides an access control method based on semantic relationship reasoning between users and resources, please refer to figure 1 , the method includes:
[0054] Step S1: Establish a user model and a resource model based on semantic information.
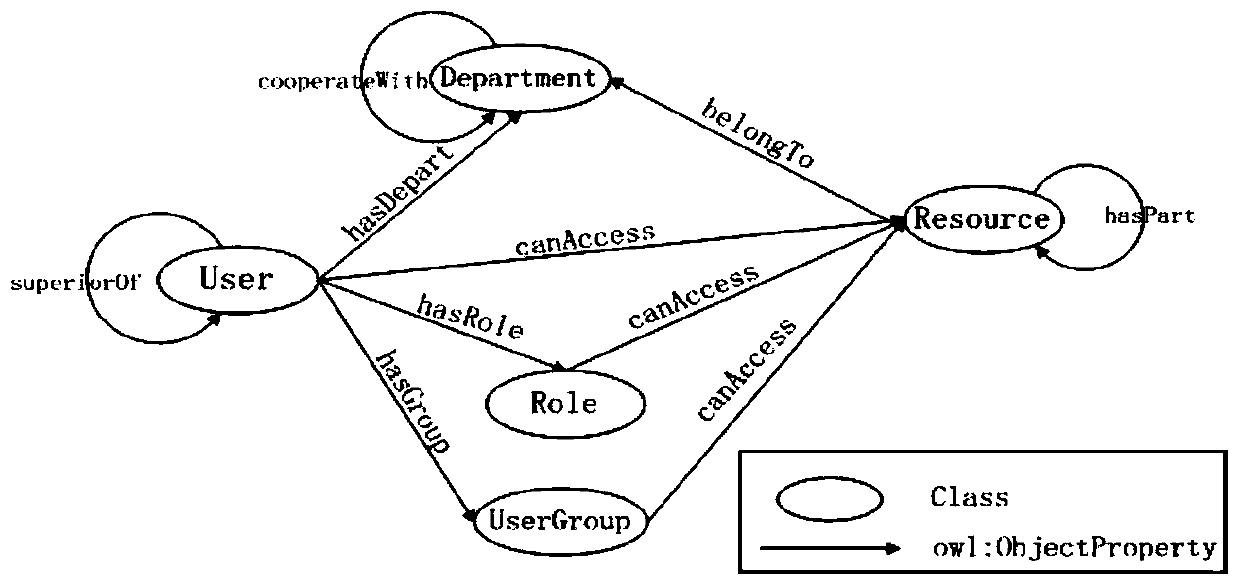
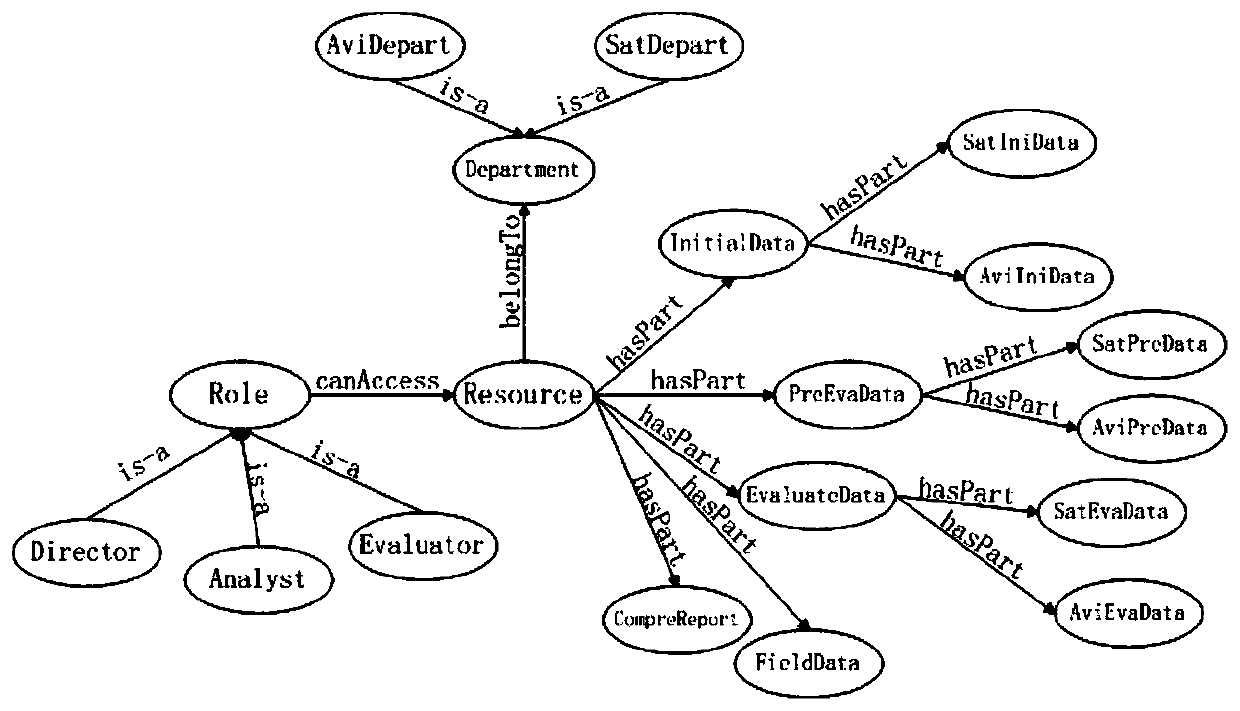
[0055] Specifically, the Internet is currently developing towards Web3.0. Semantic technology is an important technology of Web3.0, which helps to define information with more complete meanings and makes information easier to process and use in the Web, so it is applied to in various fields. The applicant of the present invention has found through a large amount of research and practice that although the methods in the prior art can adapt to the characteristics of collaborative work and cross-domain access in the network environment to a certain extent, the authorization process is relatively complicated, and has advantages in authorization management. To a certain degree of difficulty, an access control metho...
Embodiment 2
[0260] This embodiment provides an access control device based on semantic relationship reasoning between users and resources, please refer to Figure 5 , the device consists of:
[0261] A model building module 201, configured to create a user model and a resource model based on semantic information;
[0262] The basic ontology construction module 202 is used to construct the basic ontology oriented to user model and resource model;
[0263] A rule definition module 203, configured to define a set of semantic rules and reasoning rules corresponding to access control based on the basic ontology;
[0264] A decision algorithm design module 204, configured to design a decision algorithm according to the semantic rules and inference rules;
[0265] The access control module 205 is configured to determine the user's access control authority to the resource according to the determination algorithm.
[0266] In one embodiment, the model building module 201 of the device provided ...
Embodiment 3
[0285] See Image 6, based on the same inventive concept, the present application also provides a computer-readable storage medium 300, on which a computer program 311 is stored. When the program is executed, the method as described in the first embodiment is implemented.
[0286] Since the computer-readable storage medium introduced in the third embodiment of the present invention is a computer device used to implement the access control method based on reasoning of the semantic relationship between users and resources in the first embodiment of the present invention, based on the introduction in the first embodiment of the present invention method, those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details are not repeated here. All computer-readable storage media used in the method in Embodiment 1 of the present invention fall within the scope of protection intended by the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com