Novel network safe transaction system and method
A secure transaction, a new type of technology, applied in the field of information security, can solve the problem of user's key attacker interception, cannot prevent repeated attacks, etc., to achieve the effect of security guarantee, prevention of malicious reading, and online transaction security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
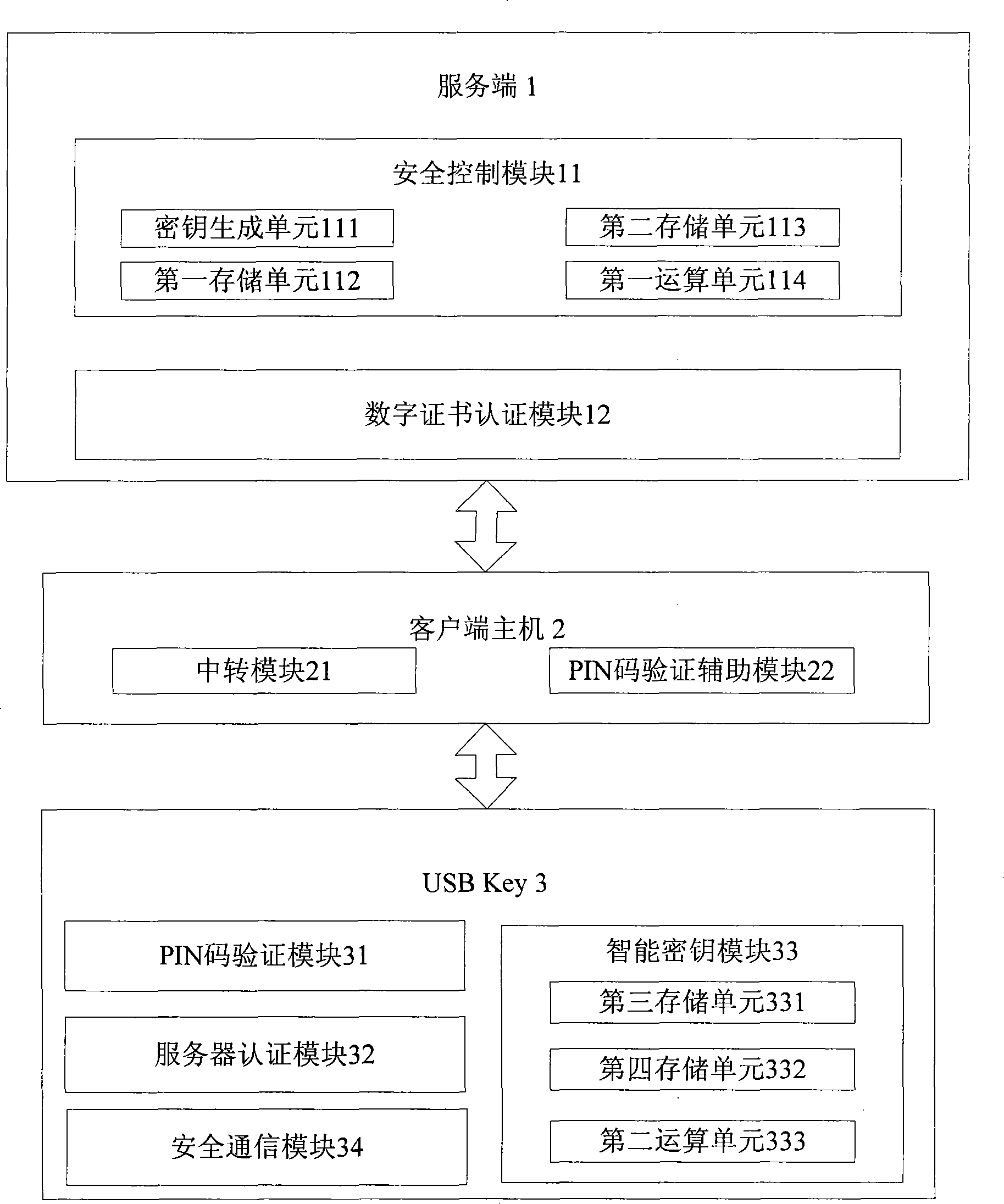
[0066] This embodiment provides a new type of online security transaction system, including: server 1, client host 2, USB Key3, server 1 includes a security control module 11, a digital certificate authentication module 12, and the security control module 11 includes a key Generation unit 111, first storage unit 112, second storage unit 113, first computing unit 114, client host 2 includes transfer module 21, PIN code auxiliary verification module 22, USB Key3 includes PIN code verification module 31, server authentication Module 32, smart key module 33, secure communication module 34, smart key module 33 includes a third storage unit 331, a fourth storage unit 332, and a second computing unit 333, see figure 1 .
[0067] in server 1
[0068] The security control module 11 is used to encrypt the session between the server 1 and the USB Key3;
[0069] The digital certificate authentication module 12 is used to verify whether the digital certificate stored in the fourth storag...
Embodiment 2
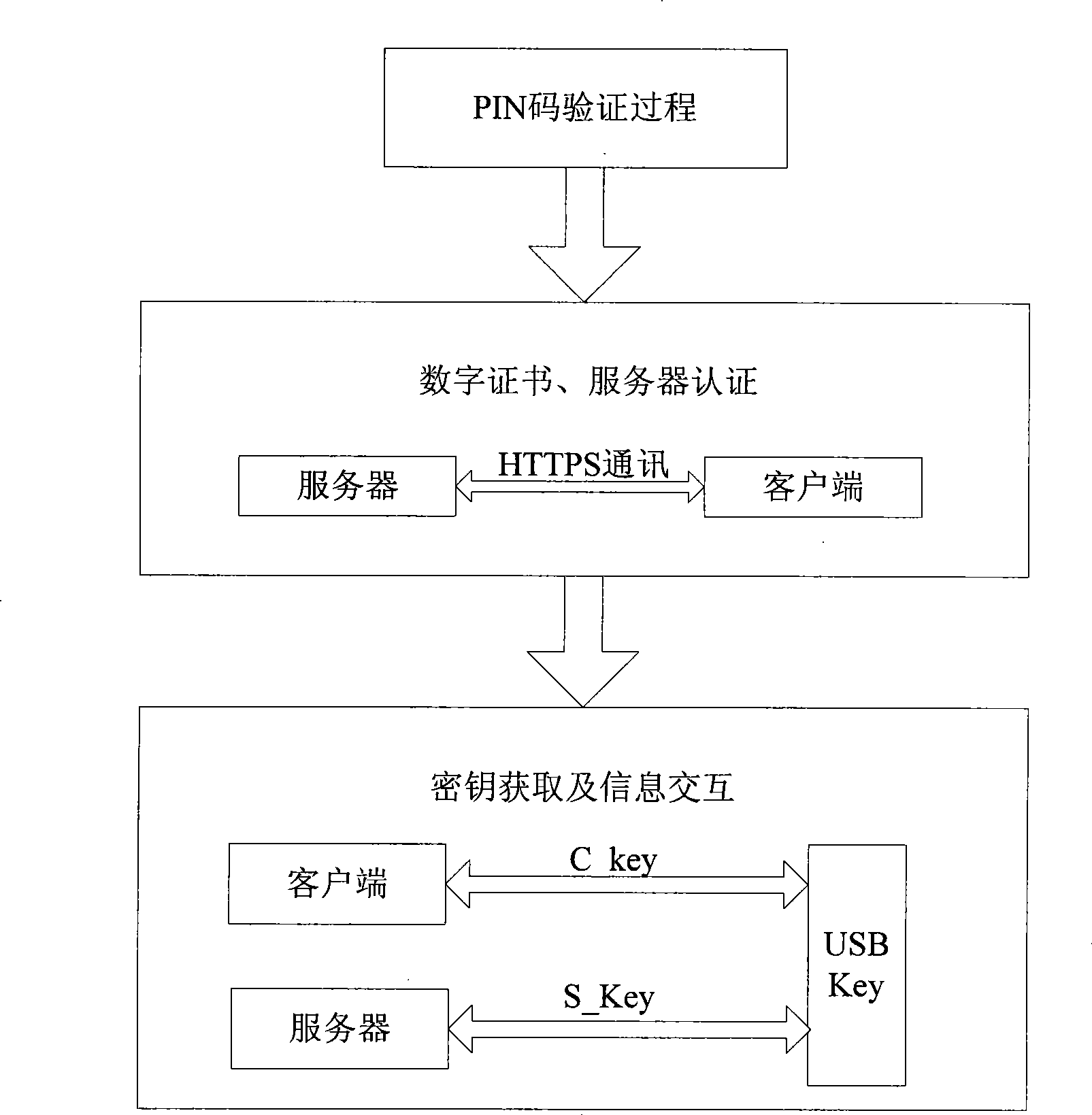
[0086] The following embodiments provide a method for secure online transactions. In this embodiment, the used USB Key is equipped with a liquid crystal display. The entire online banking transaction process includes three steps: PIN code verification, certificate and server verification, key acquisition and information interaction. In the entire online banking transaction process, PIN code verification, certificate and server verification, and key acquisition and information interaction are realized one by one in chronological order, see figure 2 ,Specific steps are as follows:
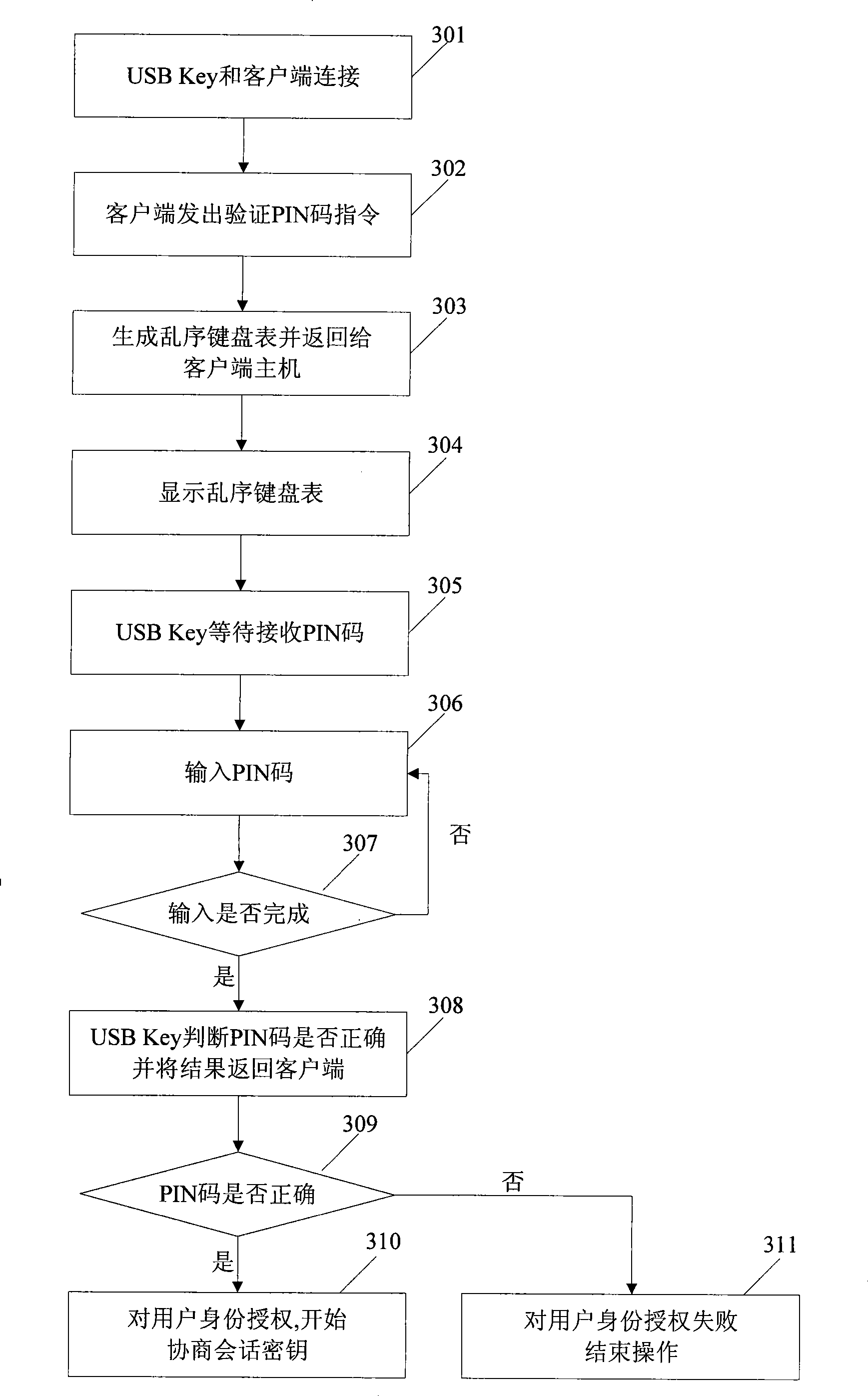
[0087] PIN code verification process, see image 3 :
[0088] Step 301, the USB Key establishes a connection with the client host;
[0089] Step 302, the client host sends an instruction to the USB Key to verify the PIN code;
[0090] Step 303, the USB Key generates a disordered keyboard list, and returns to the client host;
[0091] In step 303 of this embodiment, the disordered keyboard tabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com