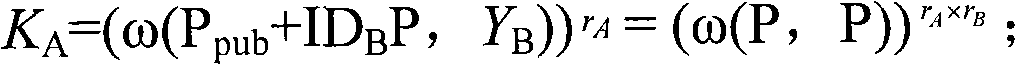Method for ciphering wireless mobile terminal communication
A mobile terminal and communication encryption technology, applied in the field of communication, can solve problems such as being unsuitable for the general needs of mobile communication users, not providing a key update and management mechanism, use, deployment, operation, maintenance and operational complexity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
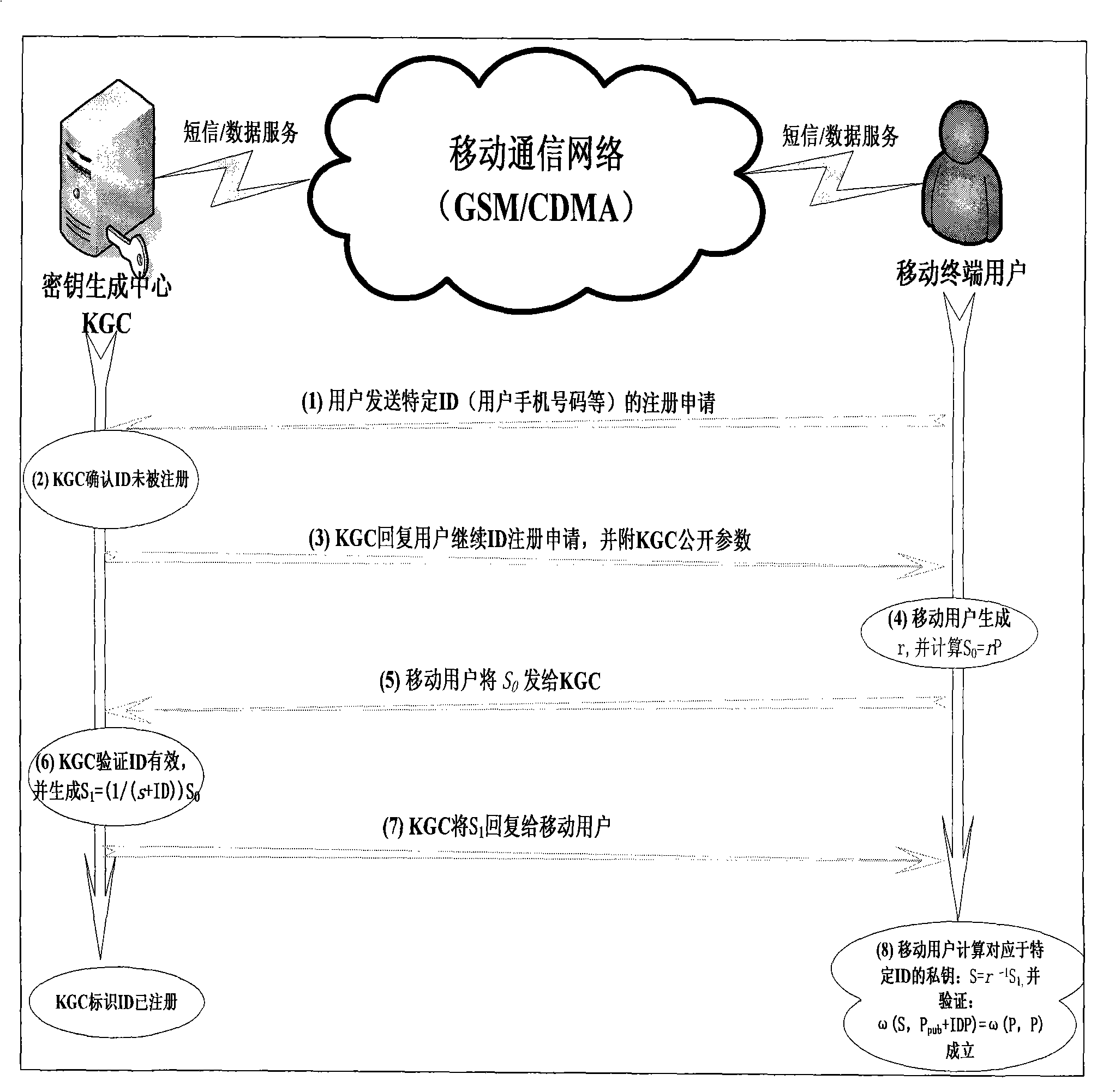
[0063] A specific embodiment of the method is given here, and the specific implementation steps are as follows.
[0064] 1. KGC announces the service number on the website, and selects two additive cyclic groups G1 and multiplicative cyclic group G2 whose order is a prime number p, selects the generator P of G1, hash function Hash, and bilinear map ω: G1×G1→ G2, master key s (KGC should keep s secret), and calculate P pub = sP. Here G1 can be taken as a subgroup on the finite field elliptic curve, and ω is taken as Weil pairing (for Weil pairing, please refer to the literature Shortsignature from the weil paring, Volume 2248 of Lecture Notes in Computer Science, Springer-Verlag, 2001, pp514-532 ).
[0065] KGC publishes public parameters through the website: p, G1, G2, P, hash function Hash, ω, P pub .
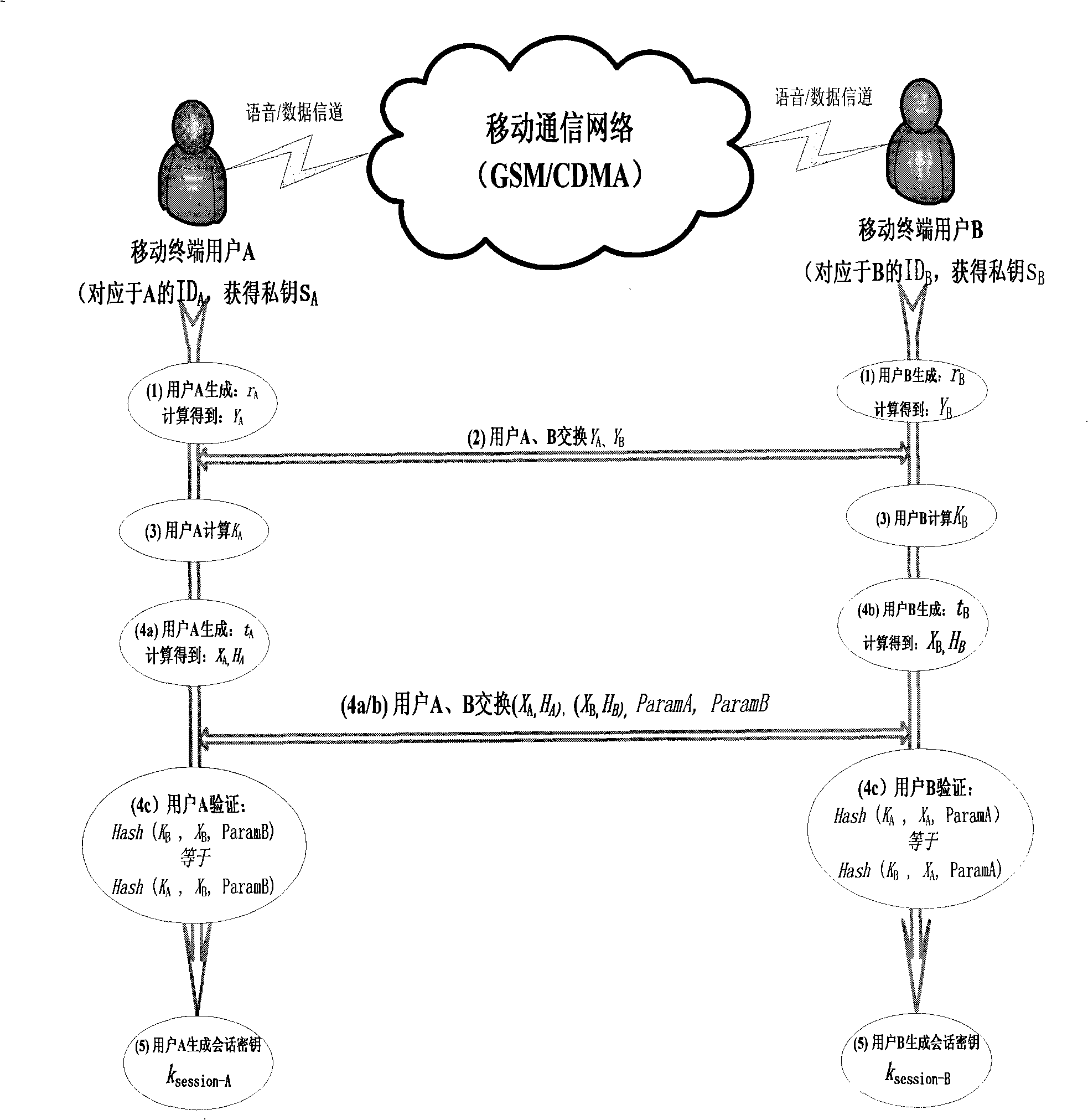
[0066] 2. Mobile user registration and private key acquisition: see figure 1 , the process of user registration and key acquisition is as follows, among which, the intera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com