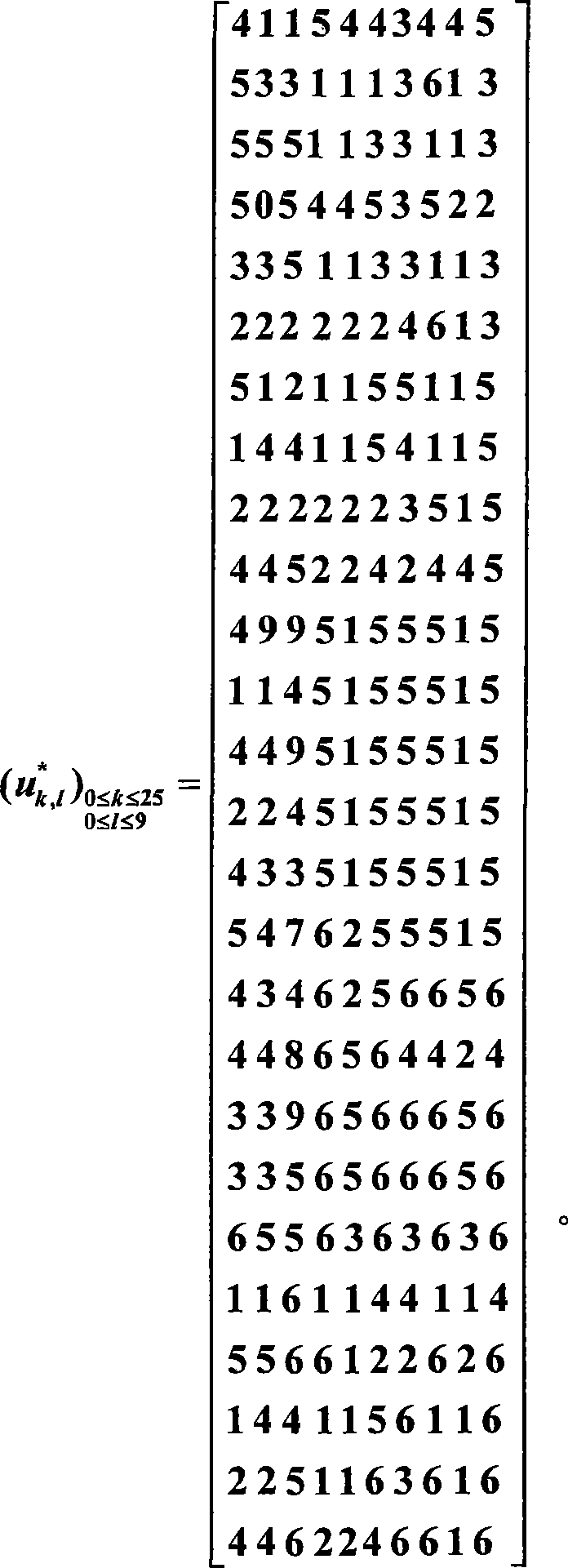Bypass operator based elliptical curve anti-bypass attack method
An elliptic curve and side-channel attack technology, applied in the field of information security, can solve the problems of disturbing the middle execution sequence of elliptic curve cryptographic scalar point multiplication operations, wrong multiplying point-point addition operator module matrix, and the influence cannot be finally eliminated, etc. The effect of achieving, improving overall performance, and improving the ability to resist bypass supply
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The embodiments of the present invention are described in detail below: the present embodiment is implemented under the premise of the technical solution of the present invention, and detailed implementation and specific operation process are provided, but the protection scope of the present invention is not limited to the following implementation example.
[0024] Assume that the embodiment intends to perform elliptic curve encryption on the plaintext M using the key d. According to the elliptic curve cryptosystem, first convert the plaintext M to the elliptic curve E / F p :y 2 =x 3 The point P on +ax+b, and then by implementing the scalar multiplication operation Q=dP of points on the elliptic curve, the representation Q of the point of the ciphertext on the same elliptic curve is obtained. In the specific implementation, choose the prime number field F pThe parameters of the elliptic curve on can be fixed. For example, take the elliptic curve equation y 2 =x 3 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com