Method for secret key configuration based on specified group
A group and key technology, which is applied in the field of communication, can solve the problems of increasing the amount of calculation, and achieve the effects of reducing the workload of calculation, simplifying the packaging process, and achieving obvious effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
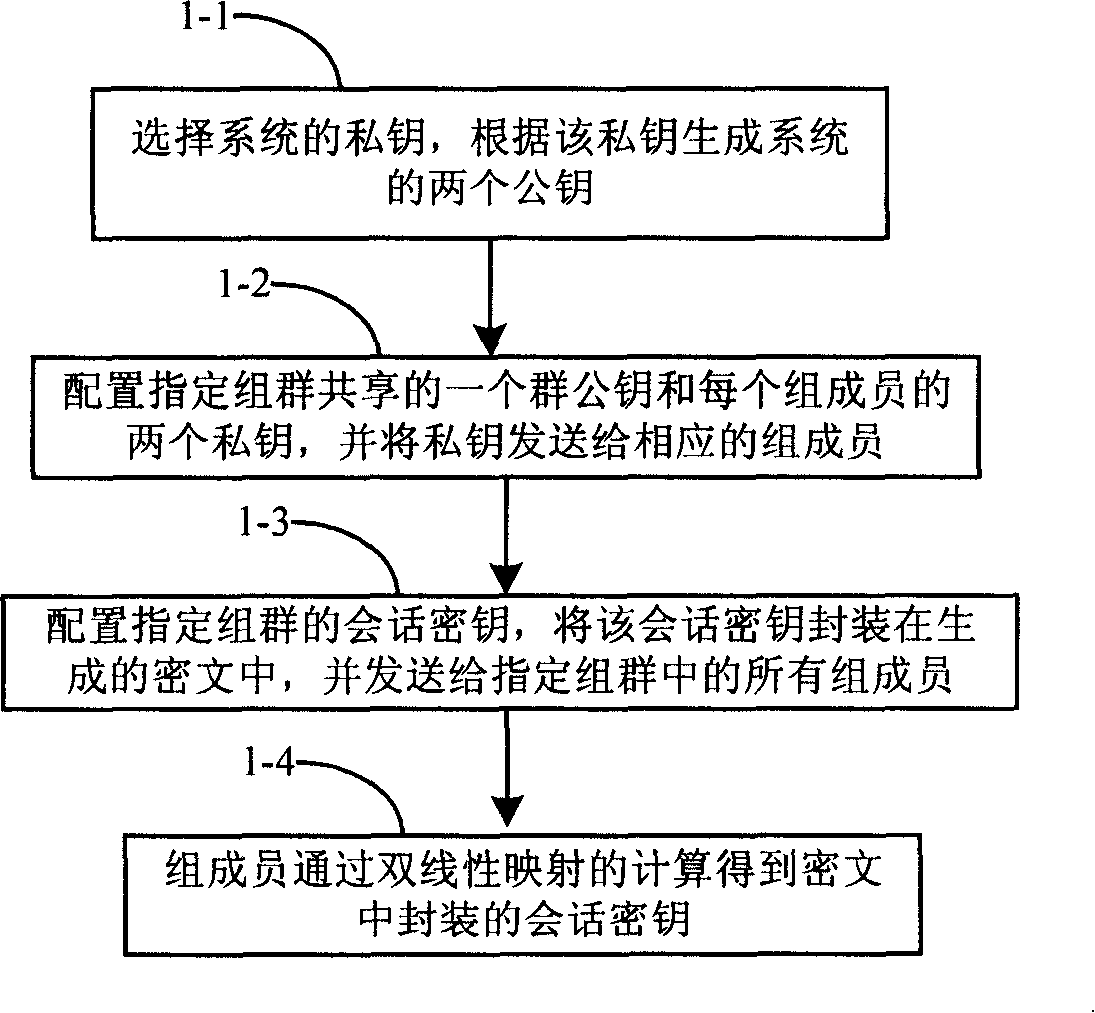
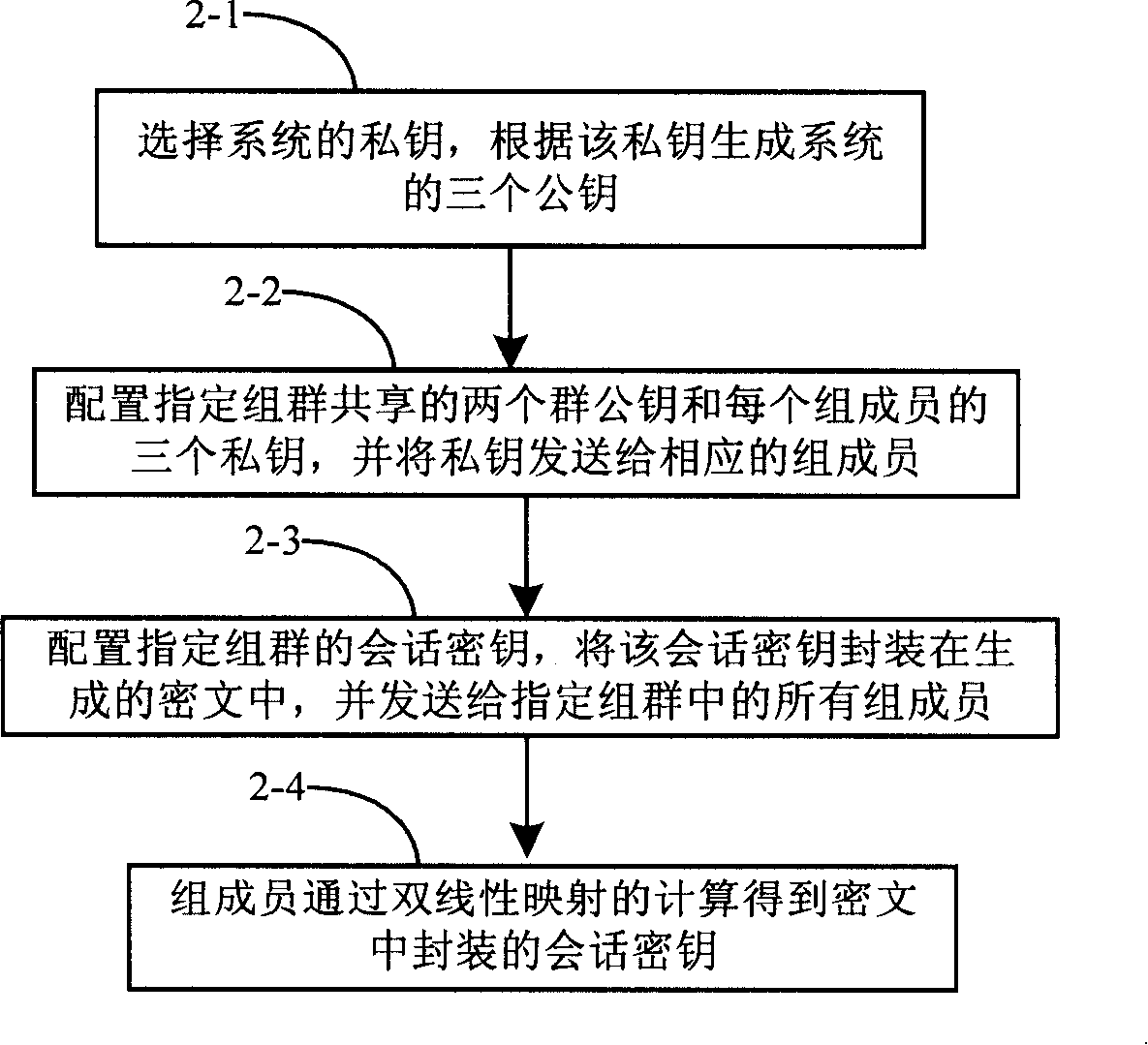
[0068] The present invention provides a method for configuring keys for designated groups. The main technical features of the present invention are as follows: a shared key is configured for designated groups, the sender generates two ciphertexts for designated groups, and the session encryption The key package is sent to group members in these two ciphertexts. The group members directly obtain the session key encapsulated in the ciphertext through bilinear operation.
[0069] Describe the present invention in detail below in conjunction with accompanying drawing, the present invention provides two embodiments of the method of the present invention, the processing flow of embodiment 1 is as follows figure 1 shown, including the following steps:
[0070] Step 1-1. Select the private key of the system, and generate two public keys of the system according to the private key.
[0071] Firstly, initialize the private key and public key of the system.
[0072] Select two suitable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com