Application method of IC card in gate inhibition system based on financial criterion
The technology of an access control system and application method is applied in the direction of instruments, time registers, and individual input/output registers, etc., which can solve the problems of easy copying of access control cards, inconvenience for users, and low security level, so as to avoid The inconvenience of carrying a special access control card, reducing the link of card issuance, and the effect of preventing monitoring and camouflage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
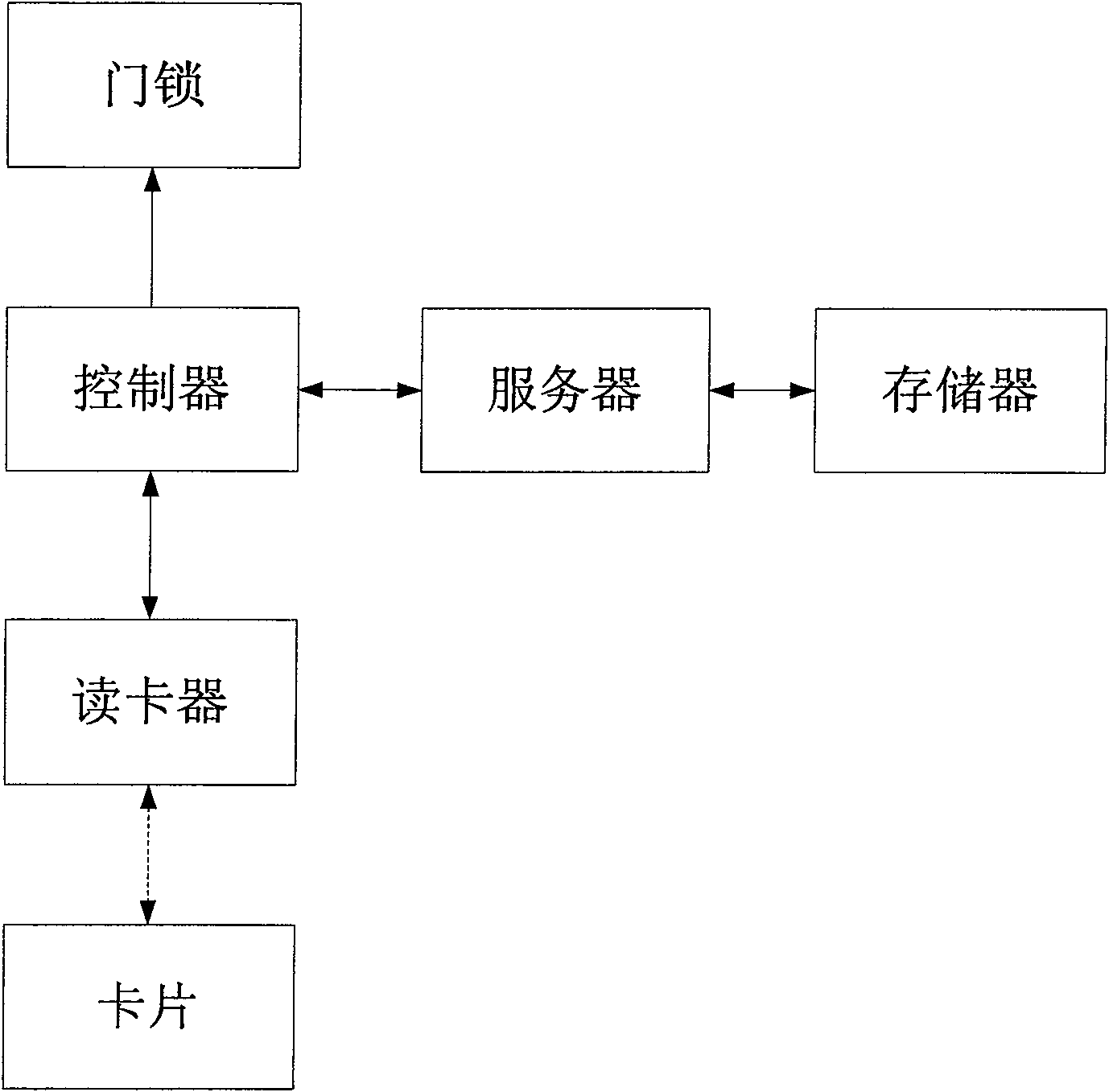
Image
Examples
Embodiment 1
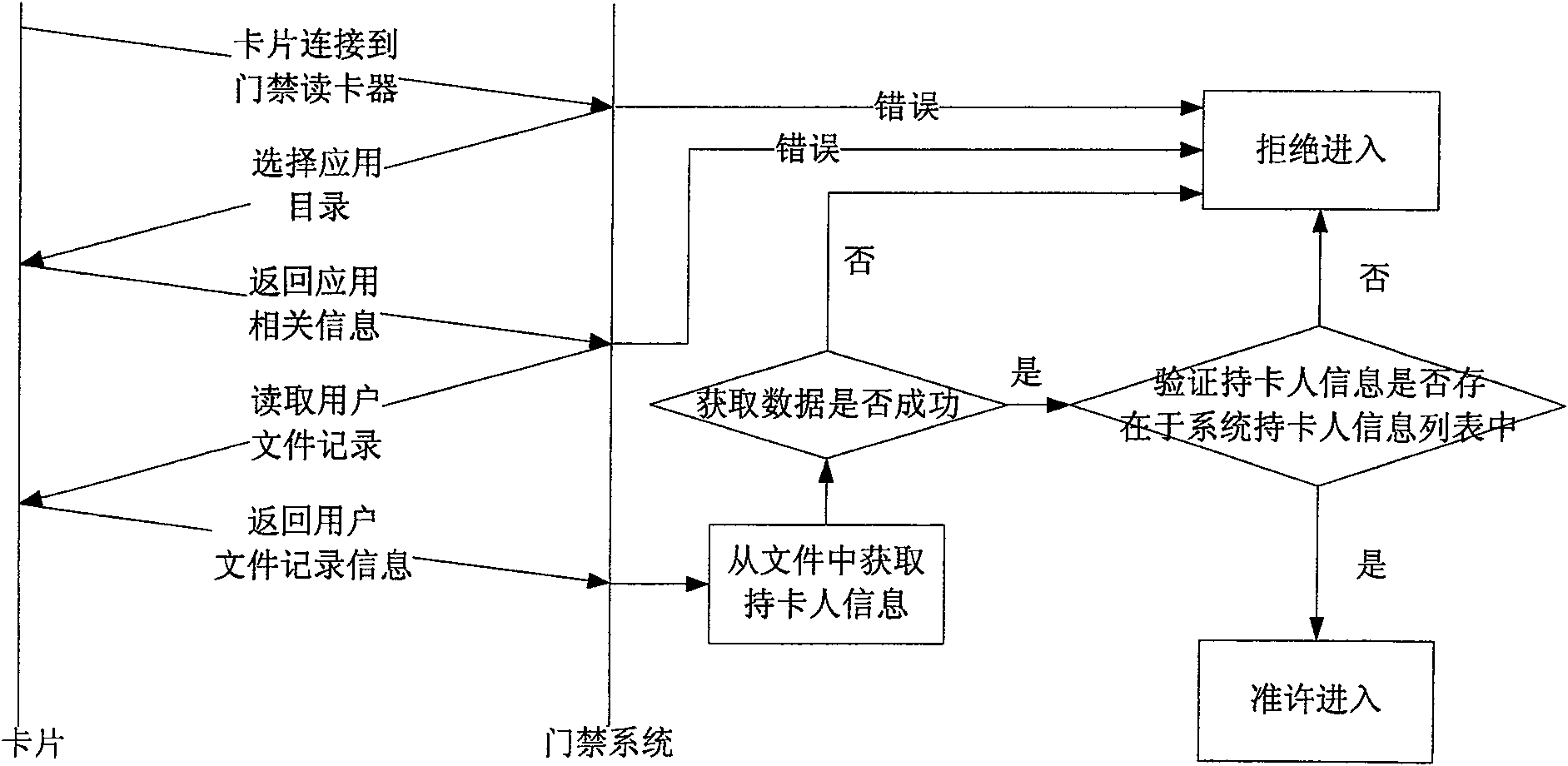
[0032] By comparing the cardholder information in the IC card with the corresponding information in the memory cardholder information list, the identity recognition method is realized.
[0033] The processing flow is attached figure 2 Shown:
[0034] A. Connect the IC card based on financial norms to the card reader, so as to establish the communication between the controller and the IC card based on financial norms;
[0035] B. The controller sends a selection application command to the IC card based on financial regulations to select the application directory. If an error occurs, the cardholder is refused to enter;
[0036] C. If the command is sent successfully, the IC card based on the financial specification returns application-related information to the controller;
[0037] D. According to the above application-related information, the controller sends a read record command to the IC card based on financial regulations to read the user file record, and if an error occ...
Embodiment 2
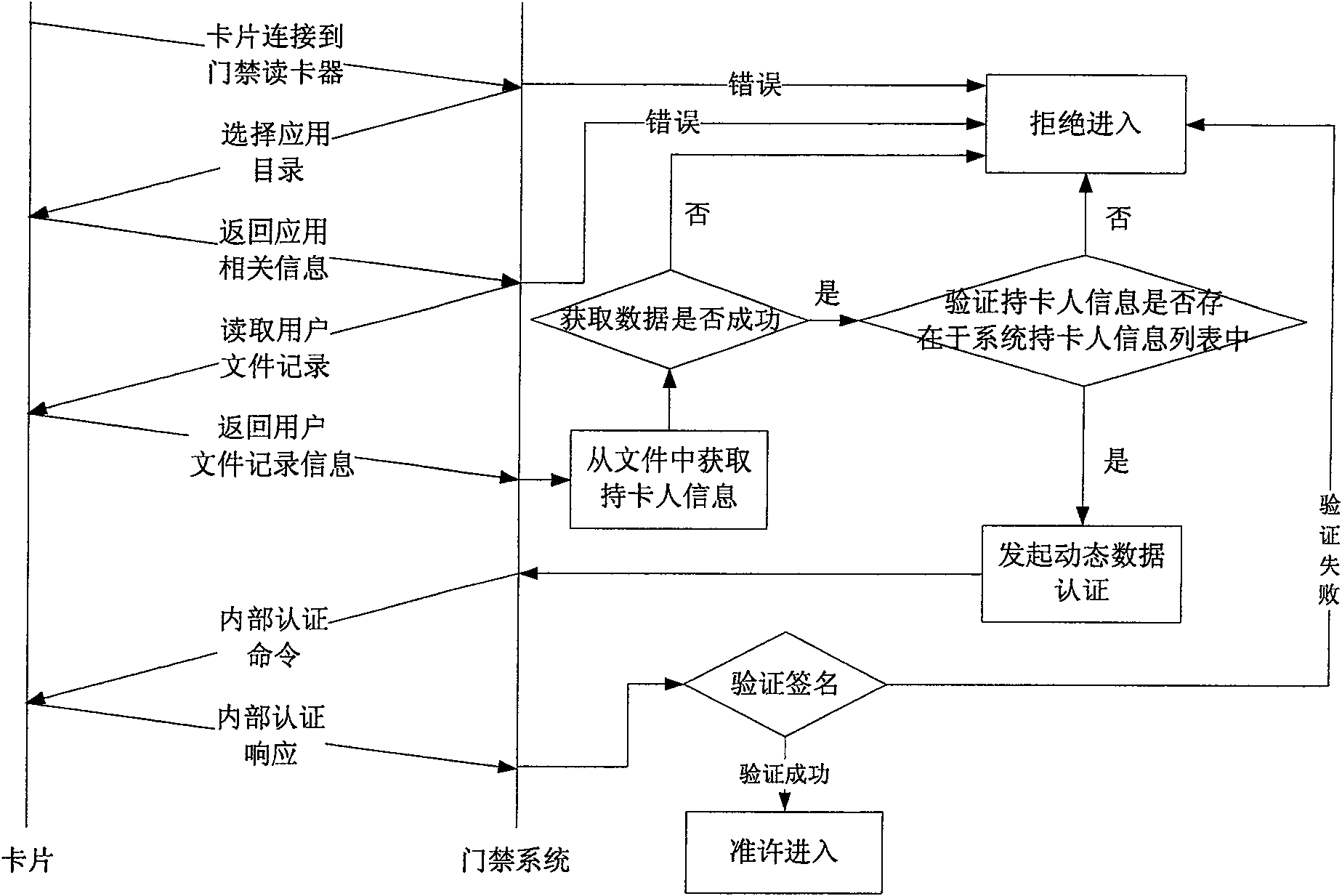
[0044] By comparing the cardholder information in the IC card with the corresponding information in the memory cardholder information list and combining dynamic data authentication, the identity recognition method is realized.
[0045] The processing flow is attached image 3 Shown:
[0046] A. Connect the IC card based on financial norms to the card reader, so as to establish the communication between the controller and the IC card based on financial norms;
[0047] B. The controller sends a selection application command to the IC card based on financial regulations through the card reader to select the application directory. If an error occurs, the cardholder is refused to enter;
[0048] C. If the command is sent successfully, the IC card based on the financial specification returns application-related information to the controller;
[0049] D. According to the above application-related information, the controller sends a read record command to the IC card based on financ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com