Authentication for a commercial transaction using a mobile module
a mobile module and commercial transaction technology, applied in the field of networked transaction systems, can solve the problems of one side of the bargain not being upheld, conventional online transaction models are awkward for the purchaser, and lose personal, financial and/or other confidential information, so as to achieve simple and more secure online commercial transaction framework, relieve some of the burden of transfer, and enhance security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
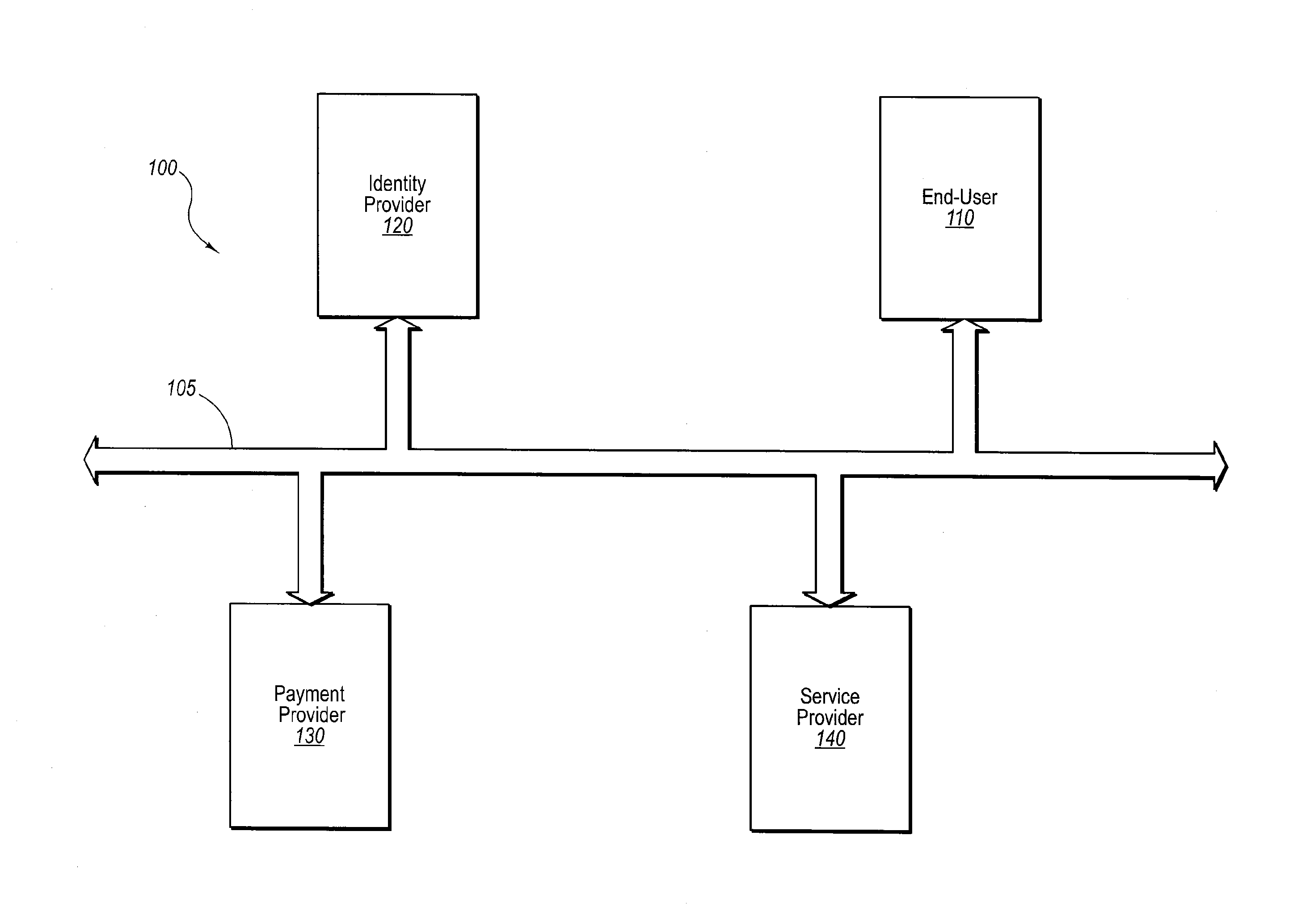
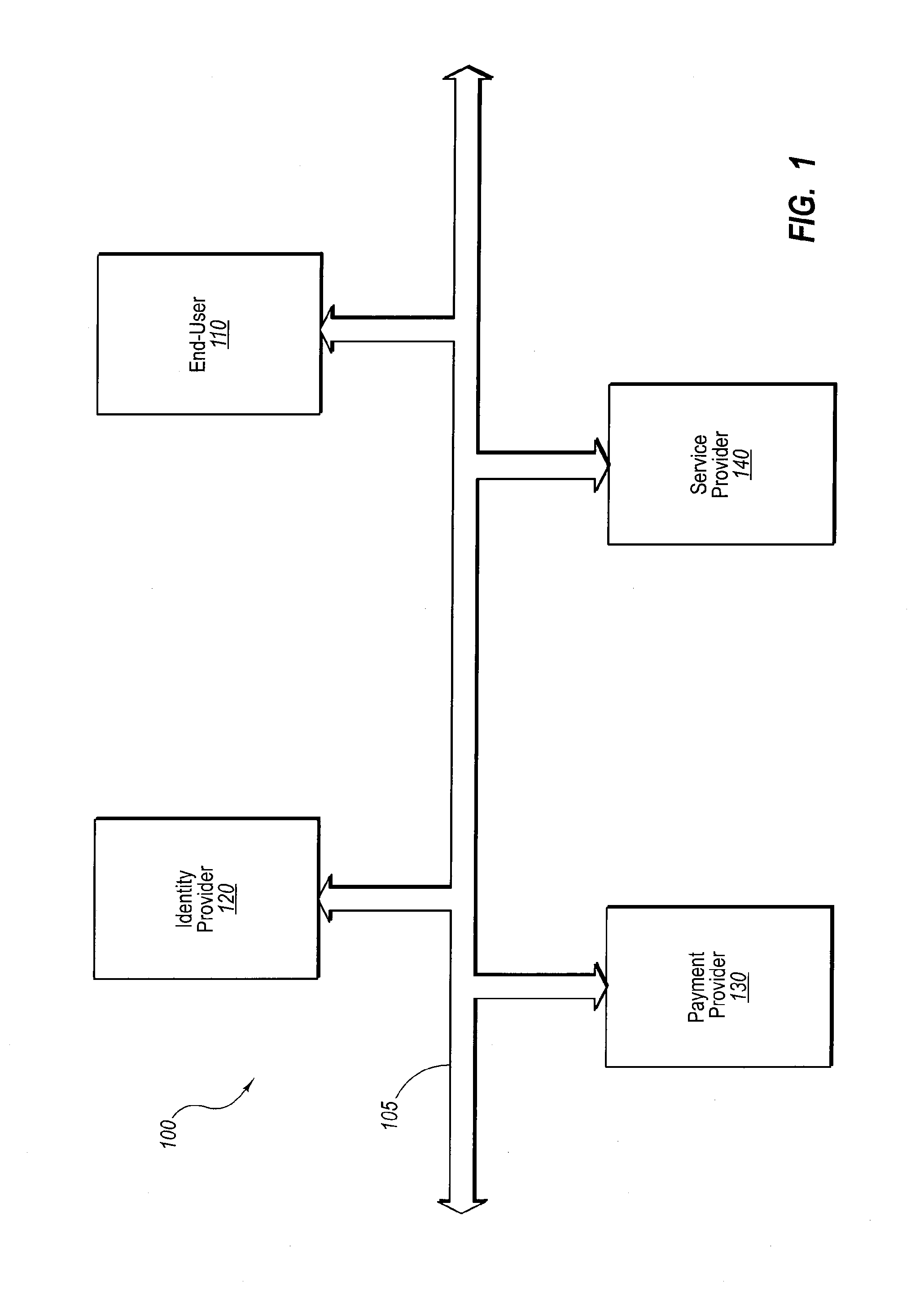
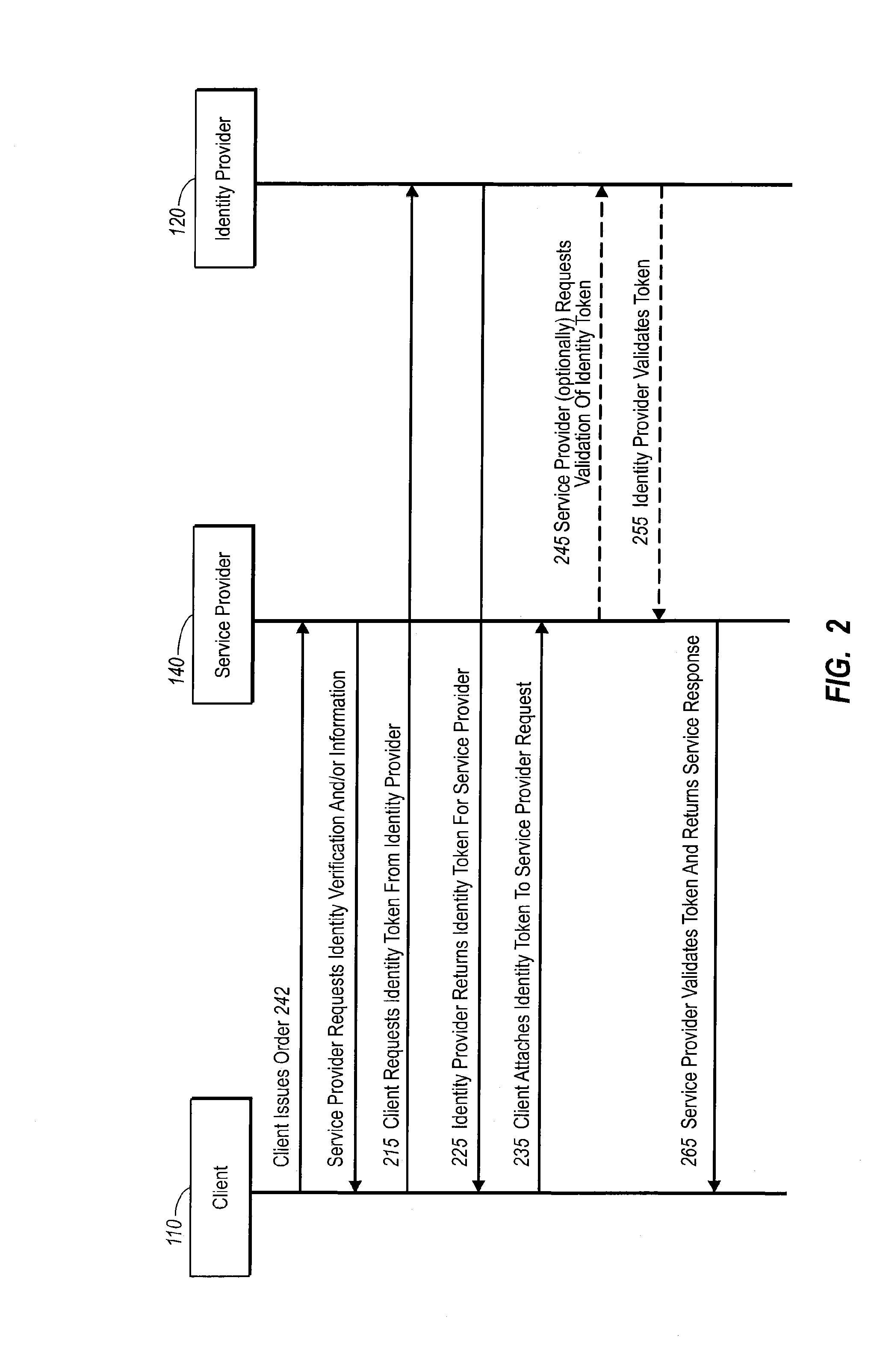
[0034]Conventional models for networked commercial transactions focus on the browser as the interface for requesting and submitting personal and financial information between an end-user purchaser and a merchant or service provider, whether it be directly through the merchant or via a third party transaction provider. In the first instance, the merchant is burdened with creating and maintaining an infrastructure capable of querying, obtaining, handling and processing personal and financial information, typically with some minimum level of security. Moreover, the merchant may be responsible for maintaining accounts and account information for each of its customers (which typically includes both confidential personal and financial information).
[0035]A purchaser must relinquish personal information (e.g., name, address, phone number, etc.) and financial information (e.g., debit and credit card numbers and expiration dates, banking account numbers, etc.) to complete a transaction. At so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com