Procedure for the preparation and performing of a post issuance process on a secure element
a post-issuance process and secure element technology, applied in the field of post-issuance process preparation and performance of secure element, can solve the problems of card capacity, affecting the service provider, application and user experience, and causing the use of certain storage parts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
[0055]In this embodiment of the procedure according to the invention the goal was to create a security domain 22 in a secure element 20 of a communication device 20 in order to receive information content (e.g. a ticketing application). The steps of the procedure are schematically illustrated in FIG. 3.
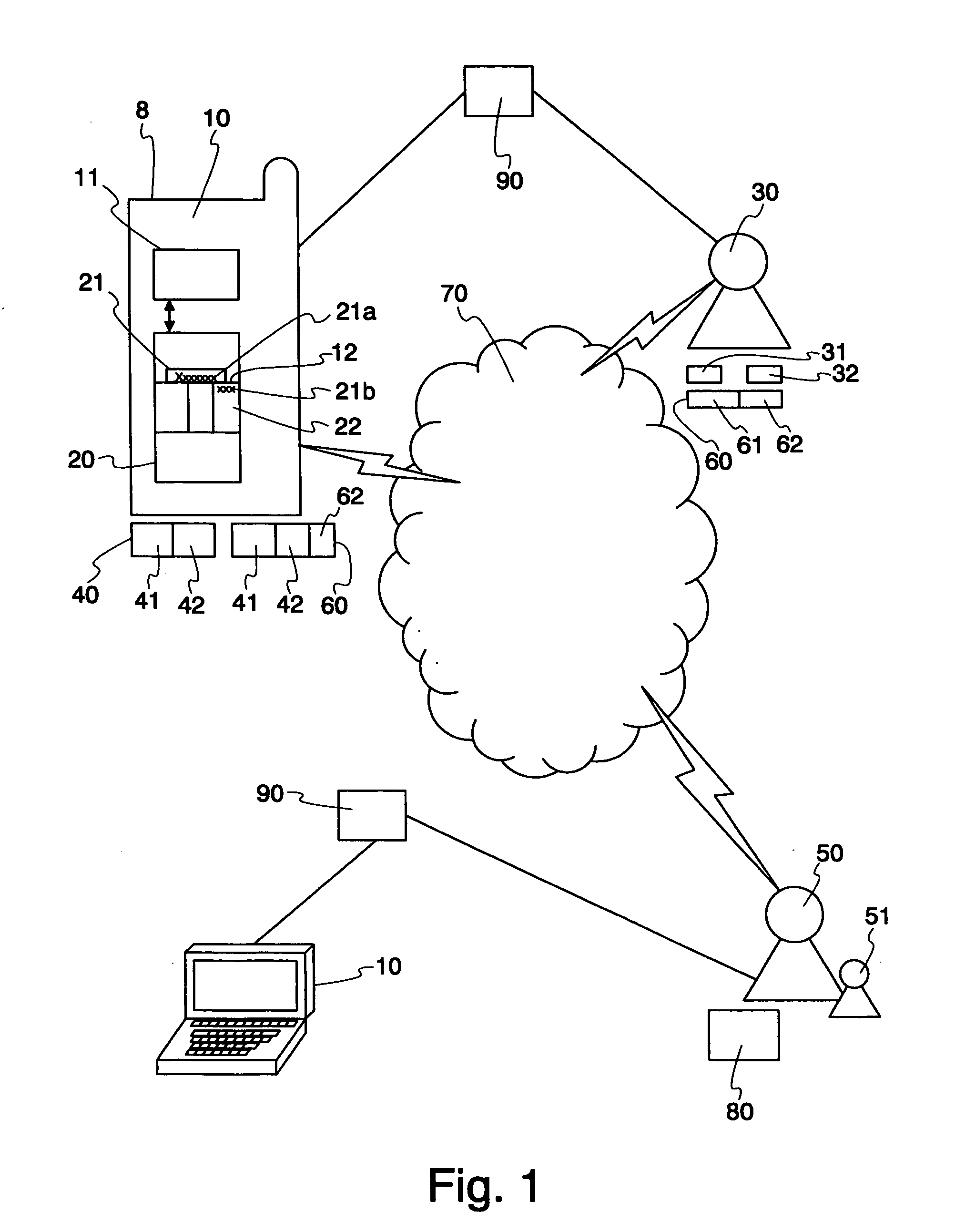
[0056]An initial data packet 40 was created in Step 131 (FIG. 3) by the data collecting application installed on the communication device 10. The data packet 40 included the SE data 41 which contained information suitable for the identification of the secure element 20 (e.g. the serial number of the secure element 20) and direct contact information of the SE controlling party 50 (e.g. the secure element issuer). The supplementary data 42 of the data packet 40 contained identification data of the communication device 10 (e.g. type of the device) for identifying the technical capacity of the device 10. The supplementary data 42 preferably includes information identifying the request of ...
example 2
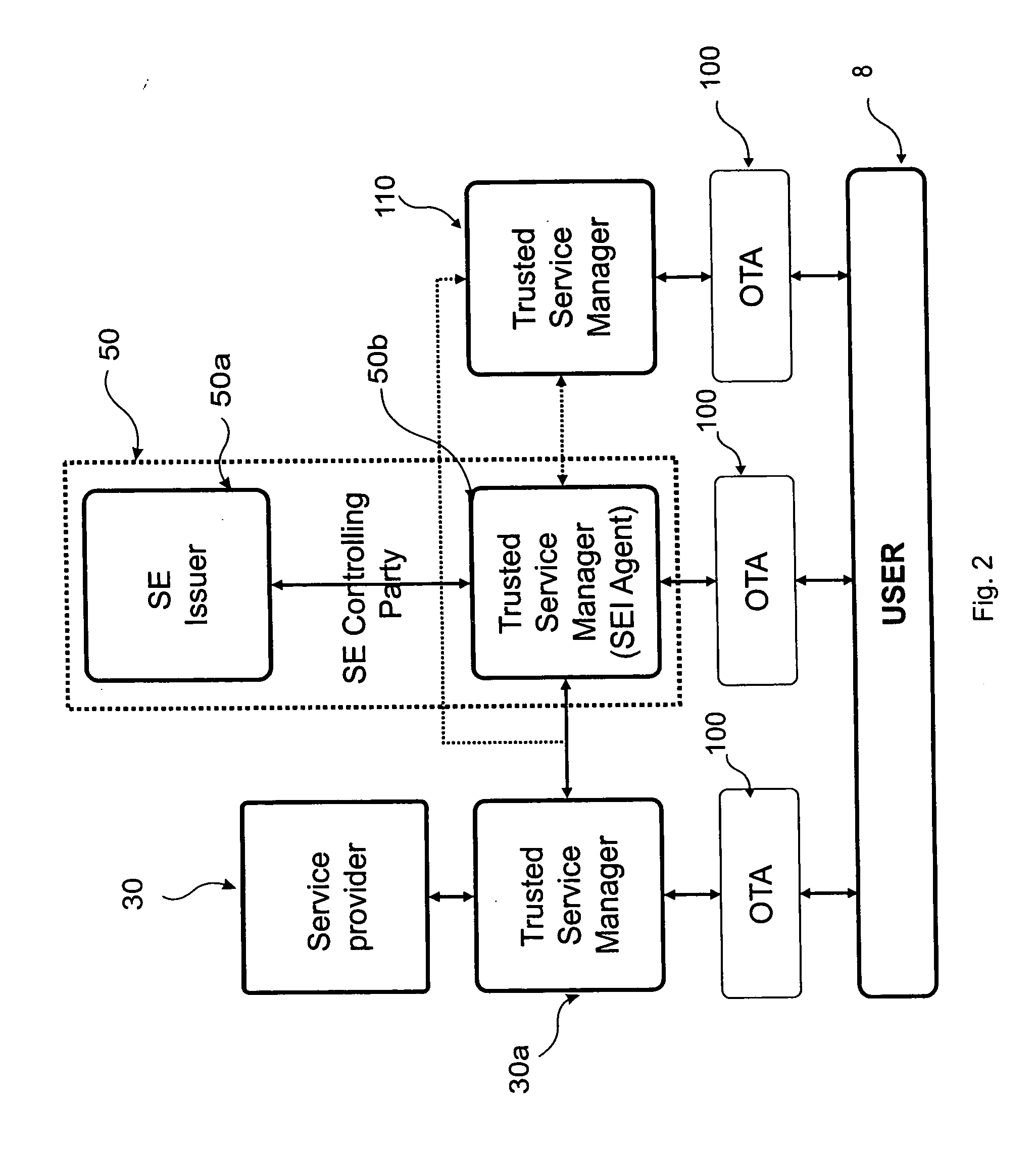
[0062]In this embodiment of the procedure according to the invention, as opposed to that presented in the previous example, the contact details of the SE controlling party 50 was determined first by the service provider 30 in Step 133 on the basis of the indirect contact data stored in the secure storage part unit 20 located in the user 8 mobile handset communication device 10.
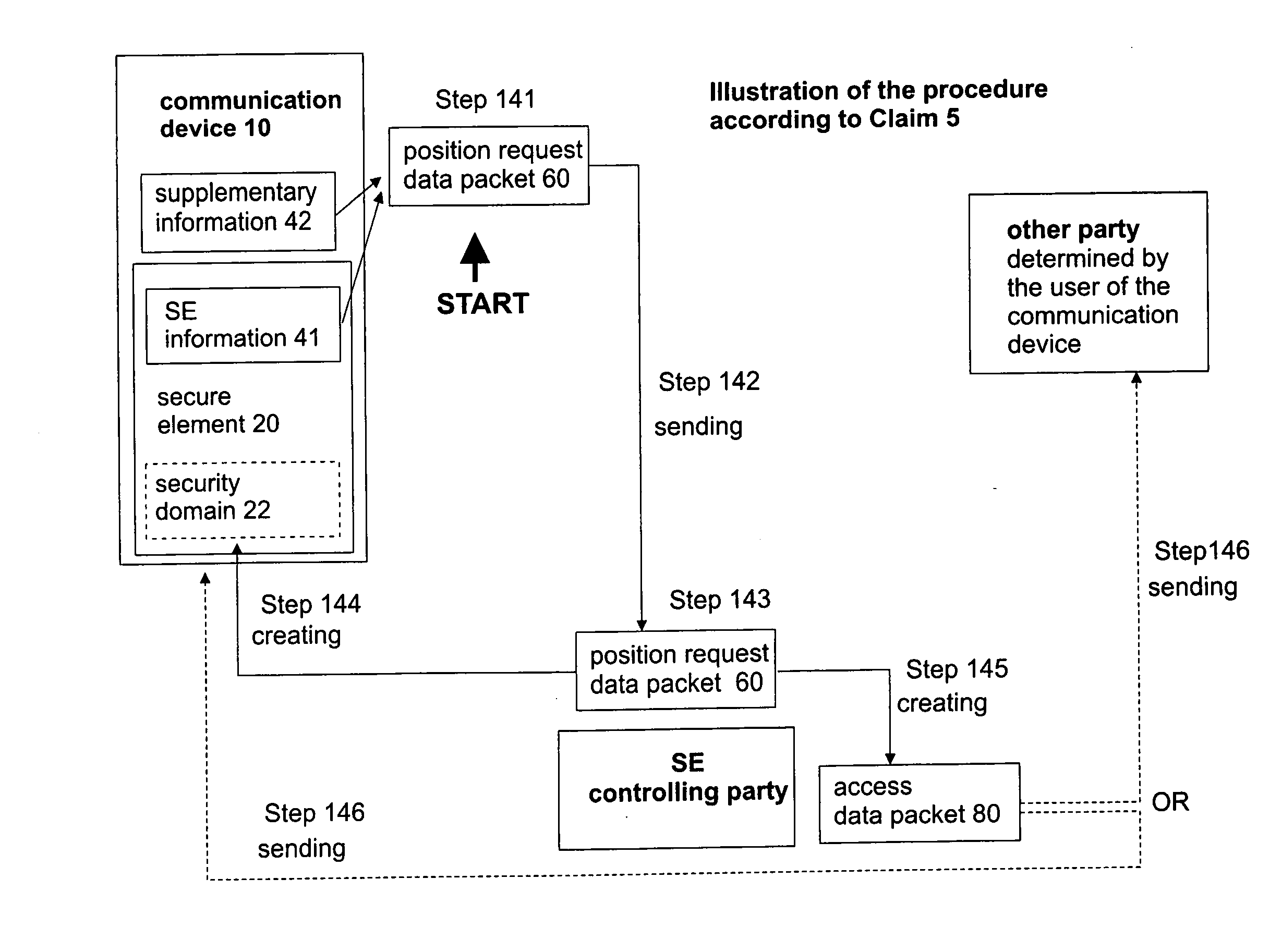
[0063]In order to acquire this data, from the indirect contact information placed in the secure element 20 a determined section of a database was reached from which the direct contact details of the SE issuer appearing as the SE controlling party 50 of the given secure element 20 were acquired. In the possession of this information a position request data packet 60 was created from the SE data 41 suitable for identifying the secure element 20 and from the supplementary data 42 identifying technical properties of the communication device 10, furthermore, from the details of the service provider 30 wishing to in...
example 3
[0065]The present embodiment of the inventive procedure (illustrated in FIG. 3 as well) differs from the embodiment described in Example 1 in that the post issuance process involves loading uniquely accessible data content (application) onto the secure element 20, instead of creating a uniquely accessible security domain 22.
[0066]The procedure is very similar, in Step 131 an initial data packet 40 is created at the communication device, which is sent to the service provider 30 in Step 132. In Step 133 the service provider 30 processes the initial data packet 40, determines the SE controlling party 50 (either from direct or indirect contact information included in the initial data packet) and creates a position request data packet 60, which comprises certain required data obtained from the initial data packet 40 and information relating to the data content to be loaded on the secure element 20.
[0067]The service provider 30 sends the position request data packet 60 to the SE controlli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com