Method for effective tamper resistance
a tamper resistance and effective technology, applied in the field of software security, can solve the problems of weakening the overall strength of tamper resistance, limiting the usefulness, and common limitations, and achieve the effect of preventing malicious users from analyzing and modifying software conten
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
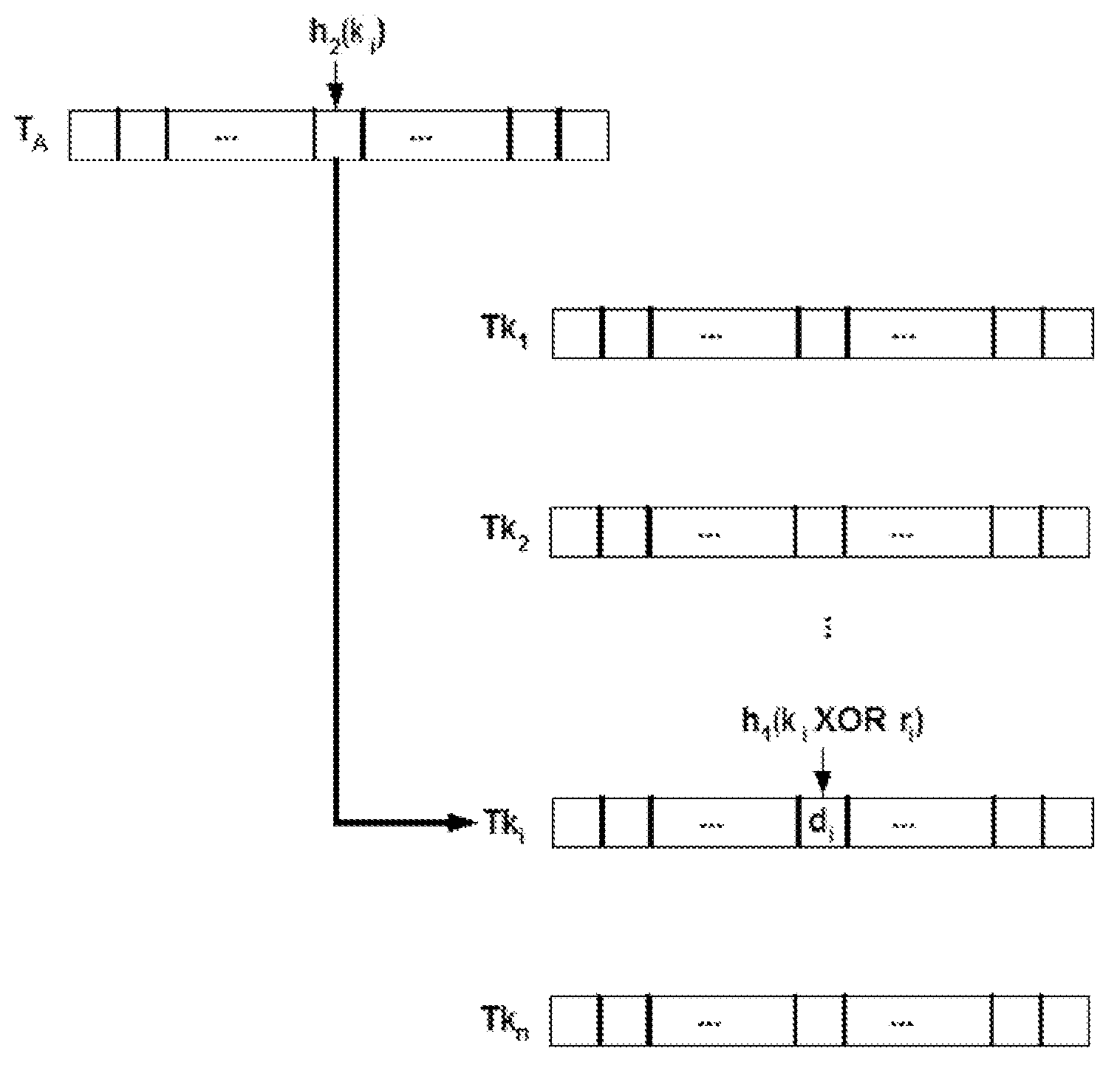
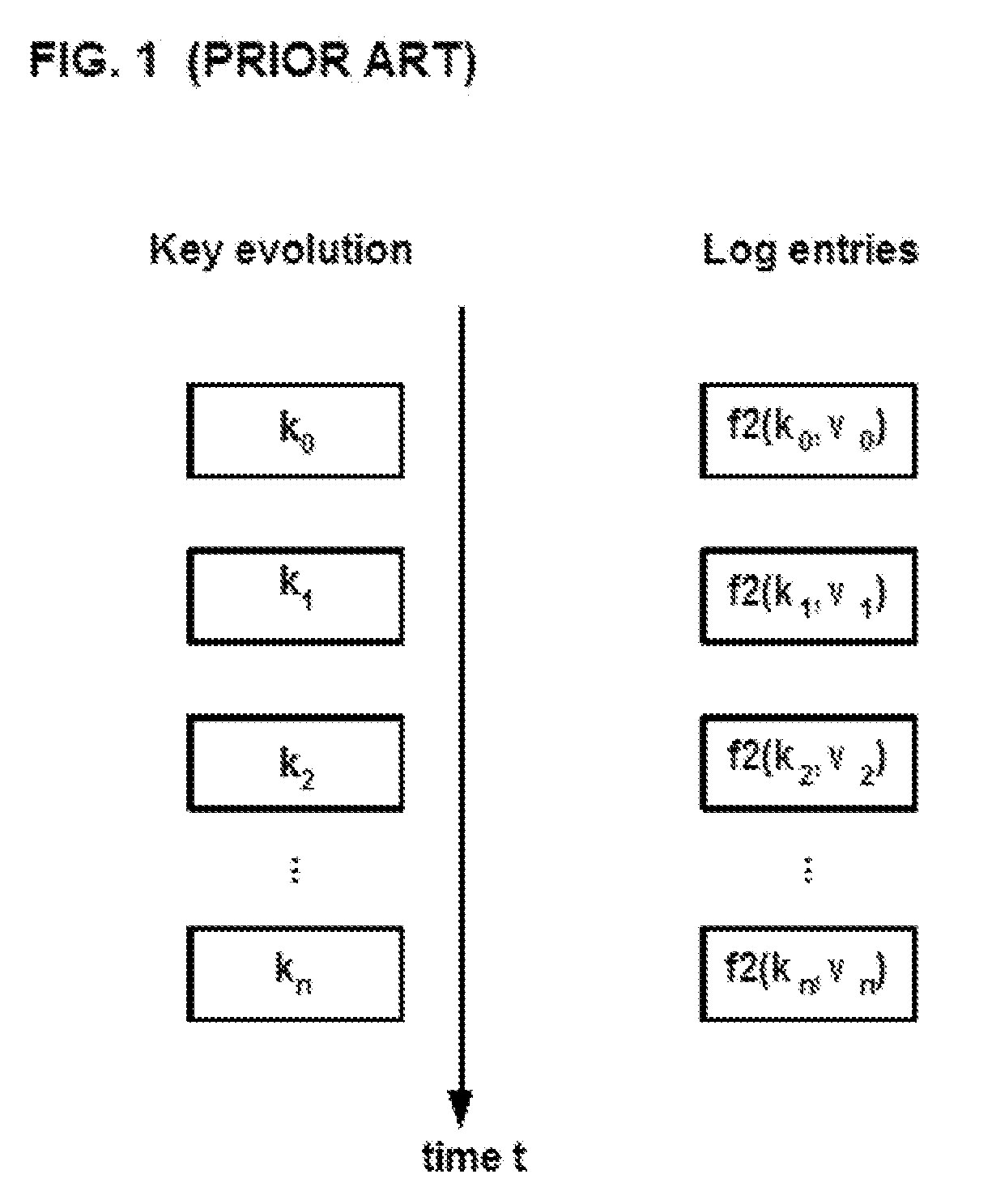
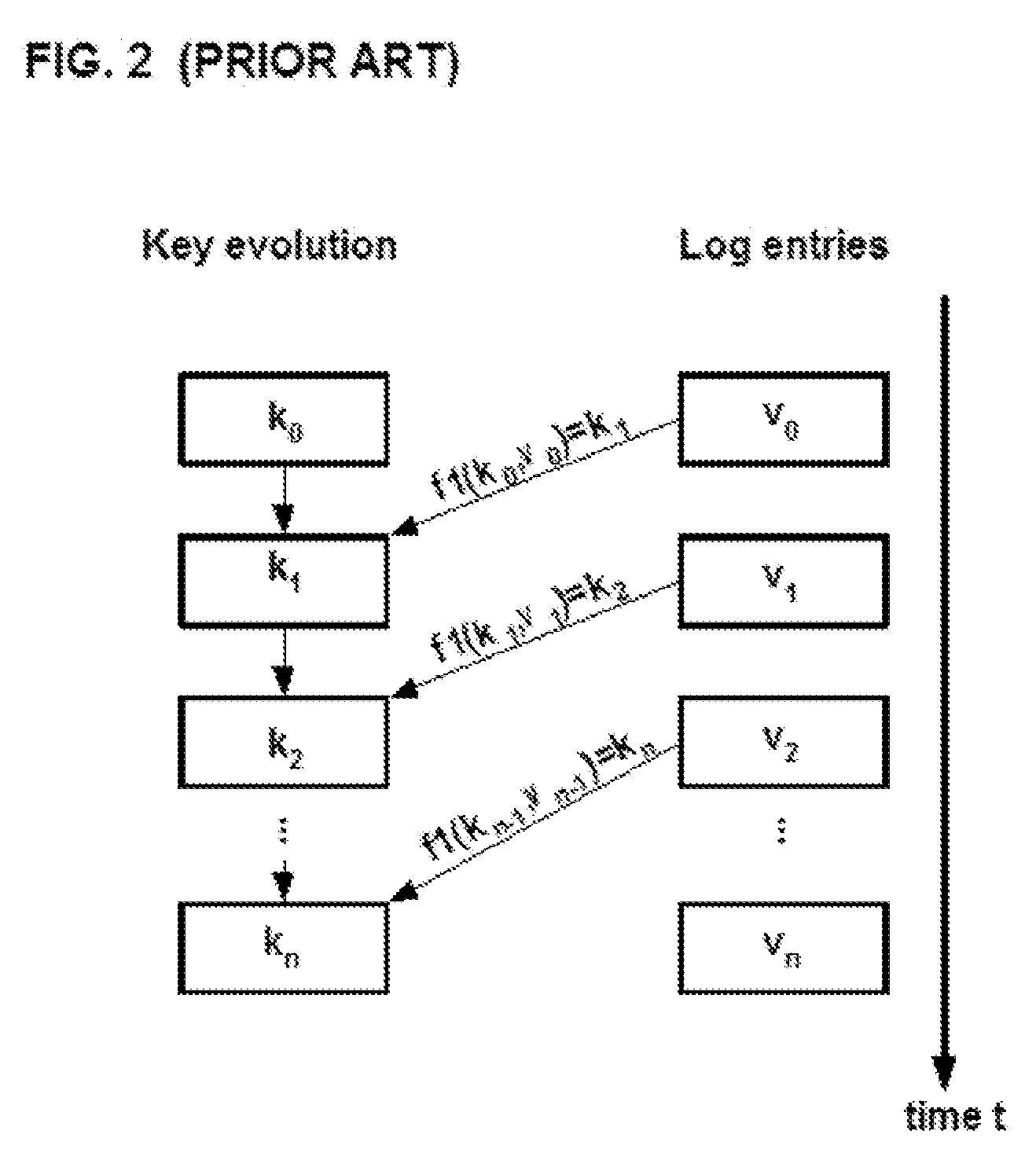
[0143]In a first embodiment, the correct, key value can be transformed into an invariant in the program. If the key evolves incorrectly, the transformation will yield an incorrect constant value which will adversely affect program behavior.
second embodiment
[0144]In a second embodiment, the program can use the key value to encrypt some crucial code, so only the correctly calculated key can decrypt the code correctly for proper program execution.
third embodiment
[0145]In a third embodiment, a more obfuscation-oriented approach uses the key value in a branch function to determine the correct target address. If the key value is wrong, the program will jump to an incorrect target address and the program will ultimately execute incorrectly.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com