Platform independent distributed system and method that constructs a security management infrastructure
a distributed system and security management technology, applied in the field of security management systems, can solve the problems of security information overload, negative impact on business operations, and high cost of protecting vital business data, and achieve the effects of reducing costs, reducing downtime, and increasing productivity and regulatory complian
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
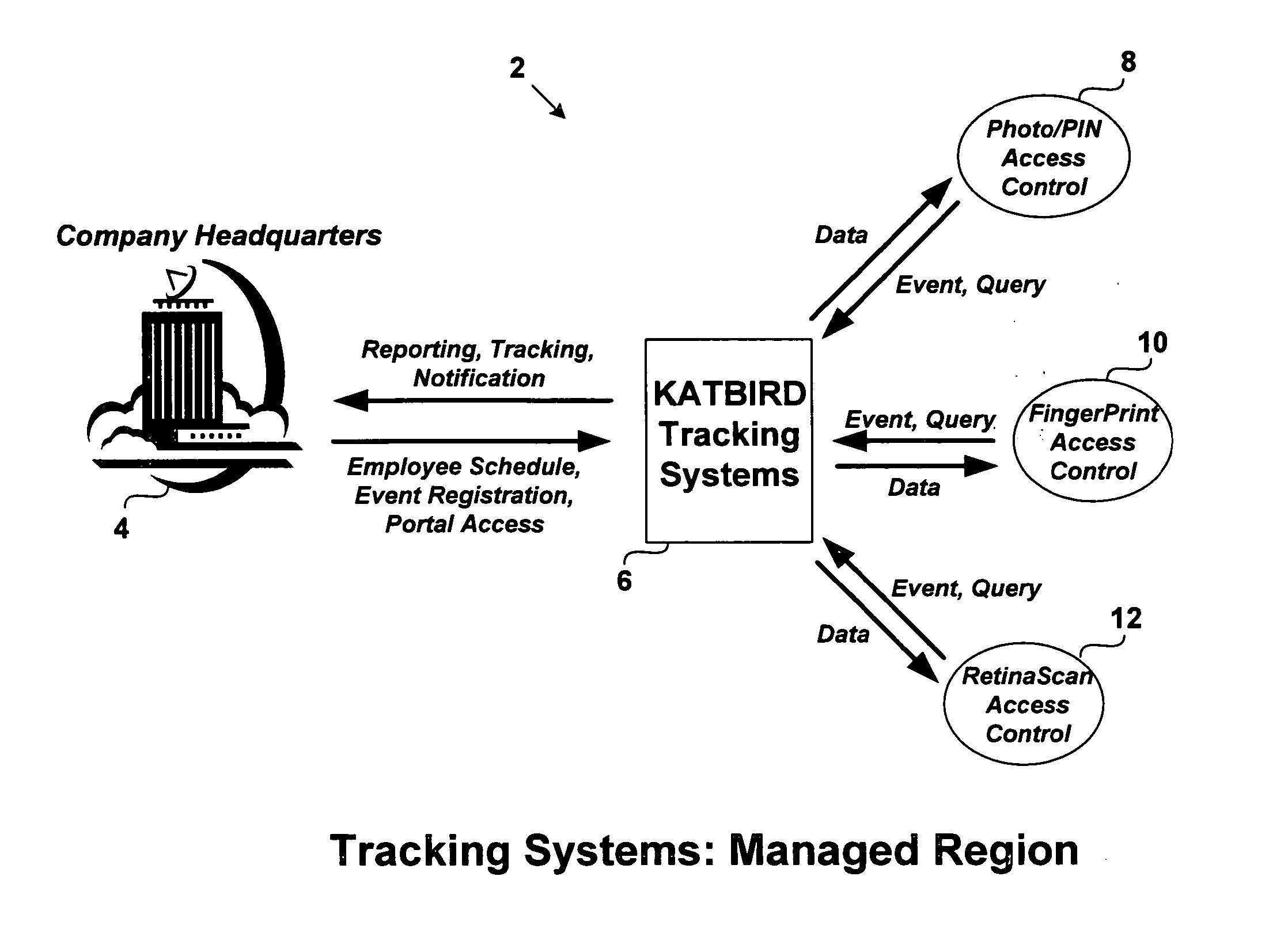
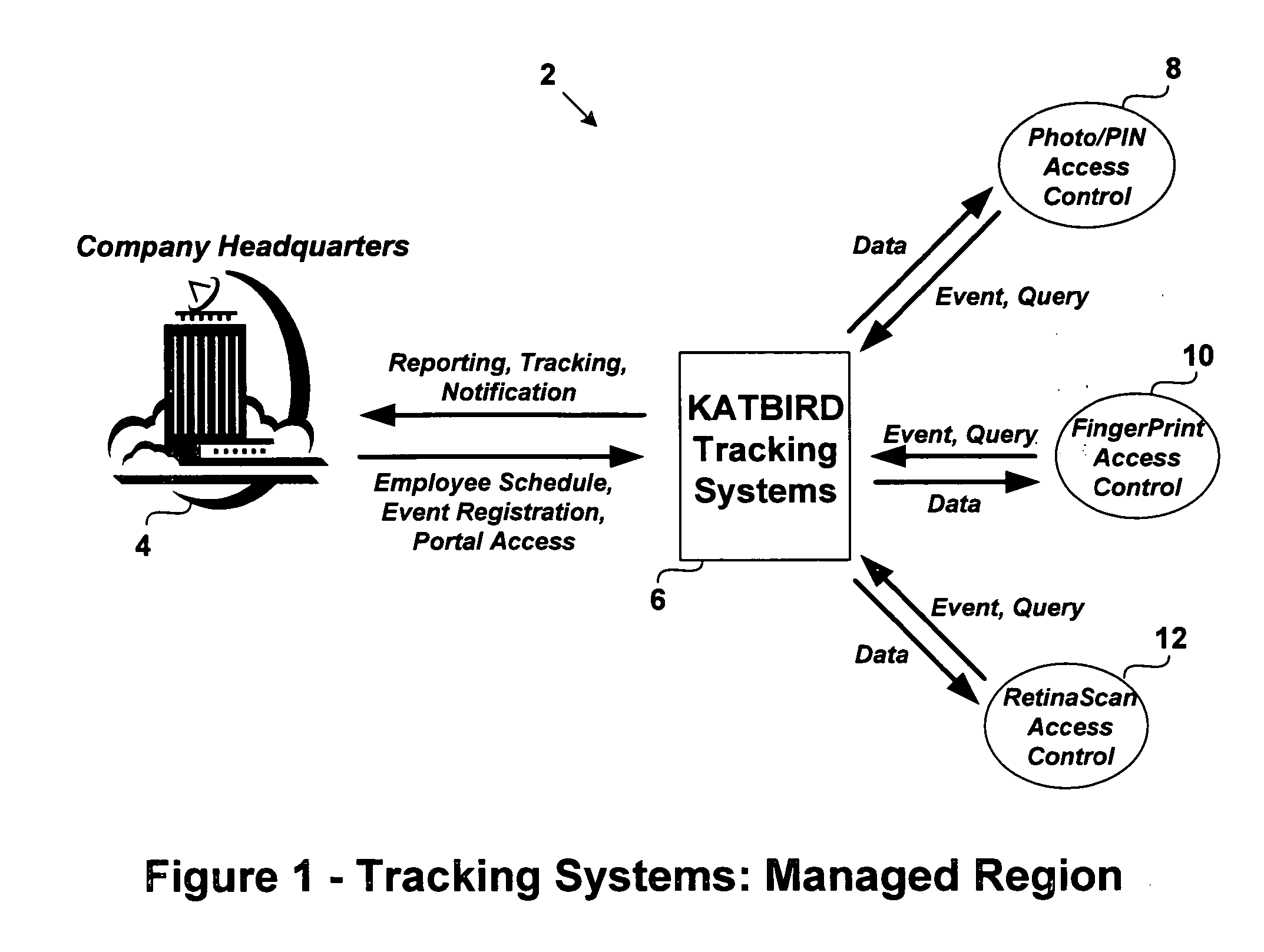
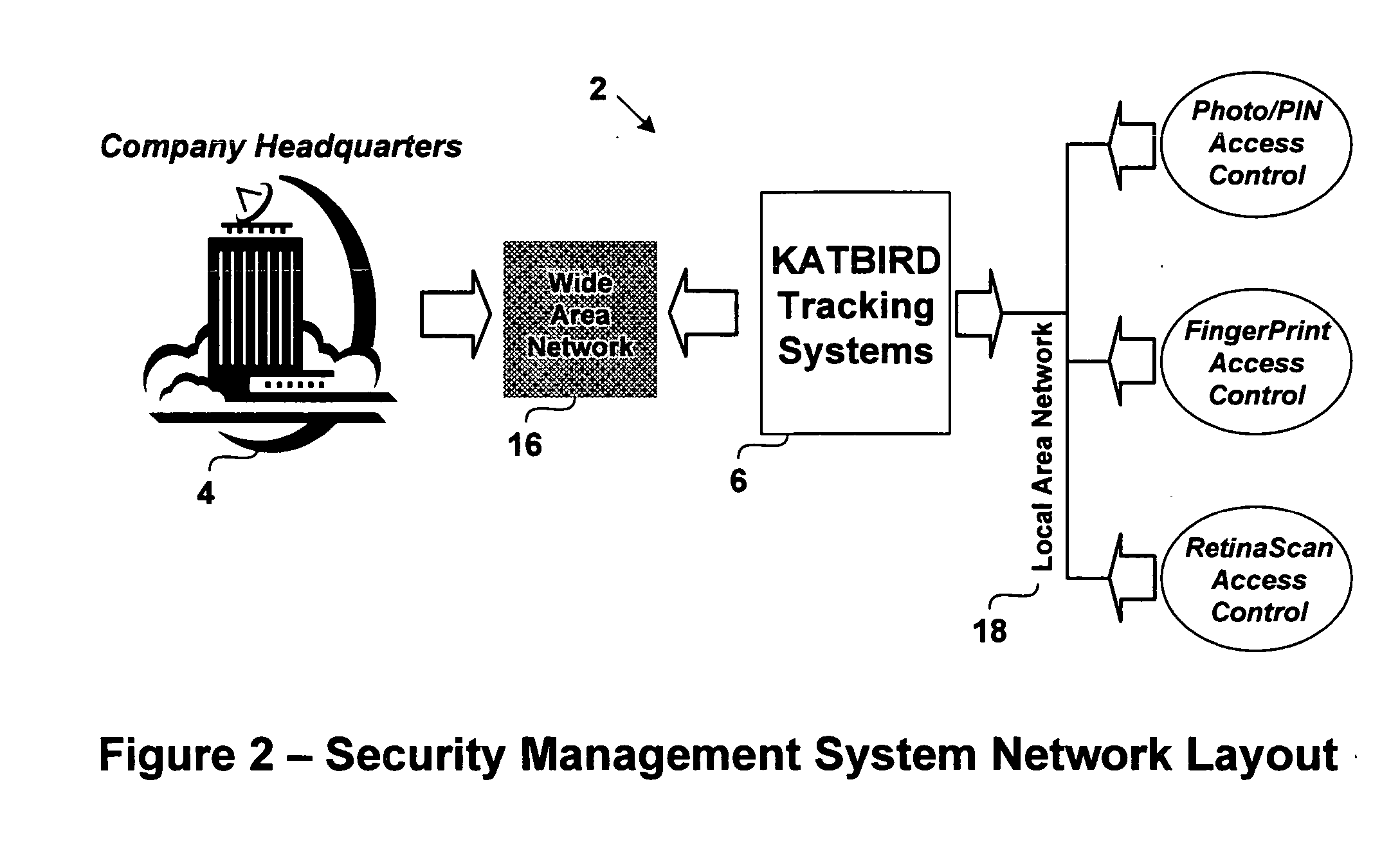
[0036] The present invention provides a security management system (SMS) for regulating access control, tracking the people / assets / events, facilitating reporting and event notification services for users. With reference to FIG. 1, the system's security management region in accordance with the embodiment of the invention is shown. In the most preferred embodiment, the system includes a .NET Framework based enterprise computer system capable of reliably (and asynchronously) communicating with any number of associated partners regardless of their respective protocols, document schemas, etc.
[0037] In the described embodiment, the SMS is coupled to an e-user which can, and usually does, have its own standards and practices for conducting a security management policy. It should be noted that the tracking systems can be in any technology other than .NET. In the most preferred embodiment, the system 2 is implemented using the “C#” (C-Sharp) programming language which provides a managed and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com