Encryption method for sip message and encrypted sip communication system
An encrypted communication system and communication system technology, which is applied in the field of encrypted communication system, to achieve the effect of shortening time and rapid implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0038] The system of Embodiment 1 is constituted by connecting the following devices through the network 0, that is, the user terminal device 10 used by the user 1, the application server device 20 providing the service 2, and establishing and controlling the user terminal device 10 and the application server device 20 through SIP communication. communication between the session management device 30.
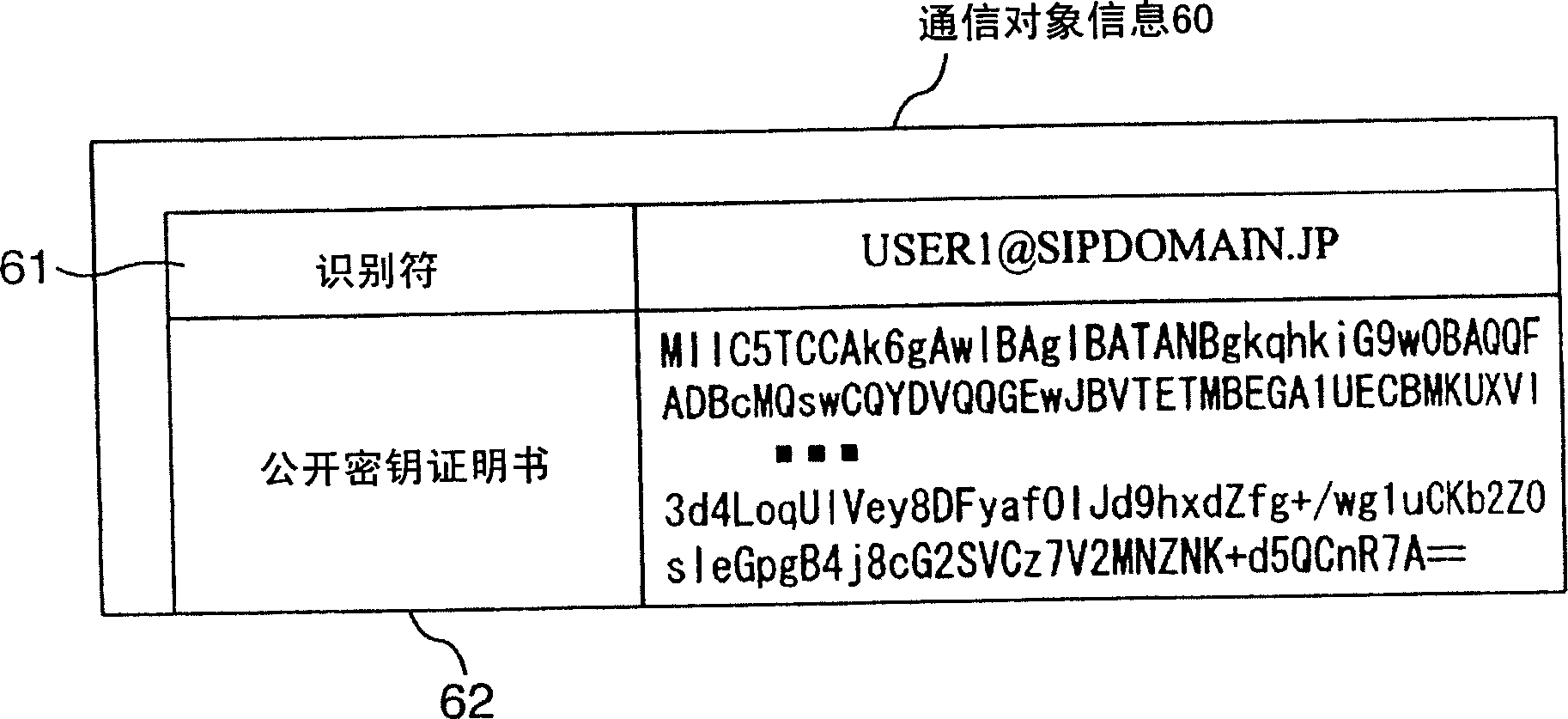
[0039] The user terminal device 10 , the application server device 20 , and the session management device 30 each have a SIP function unit 301 , an encryption function unit 302 , a communication function unit 303 , a public key certificate DB 304 , and a session DB 305 .
[0040] In addition, when specifically showing the SIP function part 301 operating in the user terminal device 10, it will be expressed as the SIP function part 301 hereinafter. 1 , when representing the SIP function unit 301 operating in the application server device 20, it is expressed as the SIP function uni...
Embodiment 2
[0294] The system structure of Embodiment 2 is similar to that of Embodiment 1.
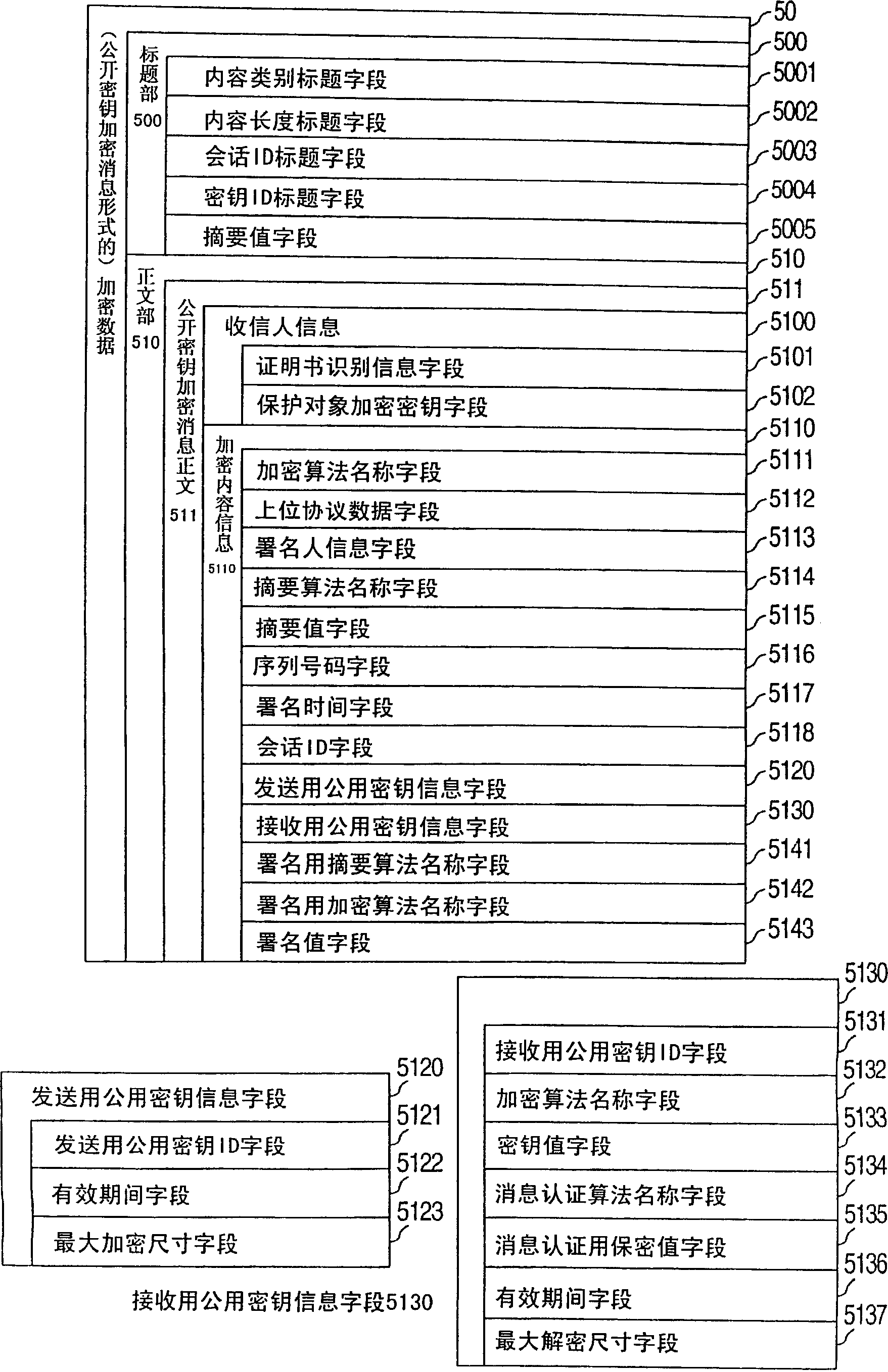
[0295] However, in Embodiment 2, when sending the REGISTER message 41, the SIP function unit 301 must generate the encrypted data 50 in the form of a public key encrypted message, and when sending a SIP message other than the REGISTER message 41 (such as the INVITE message 43), it must Encrypted data 50 in the form of a common key encrypted message is generated.
[0296] Therefore, the encryption function unit 302 also has a function of updating the session information 70 stored in the session DB 305 , and the SIP function unit 301 has a function of instructing the encryption function unit 302 to update the session information 70 .
[0297] Furthermore, the encryption function unit 302 of the session management device 30 3 It has a function of generating not only the common information for decryption 720 but also the common information for encryption 710 .
[0298] On the other hand, the encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com