Internet safety protocol high-speed processing IP burst method
A security protocol, IP fragmentation technology, applied in secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as reducing network throughput performance, occupying large memory, unable to process IP fragmentation at high speed, etc., to improve business support The effect of range, high forwarding performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
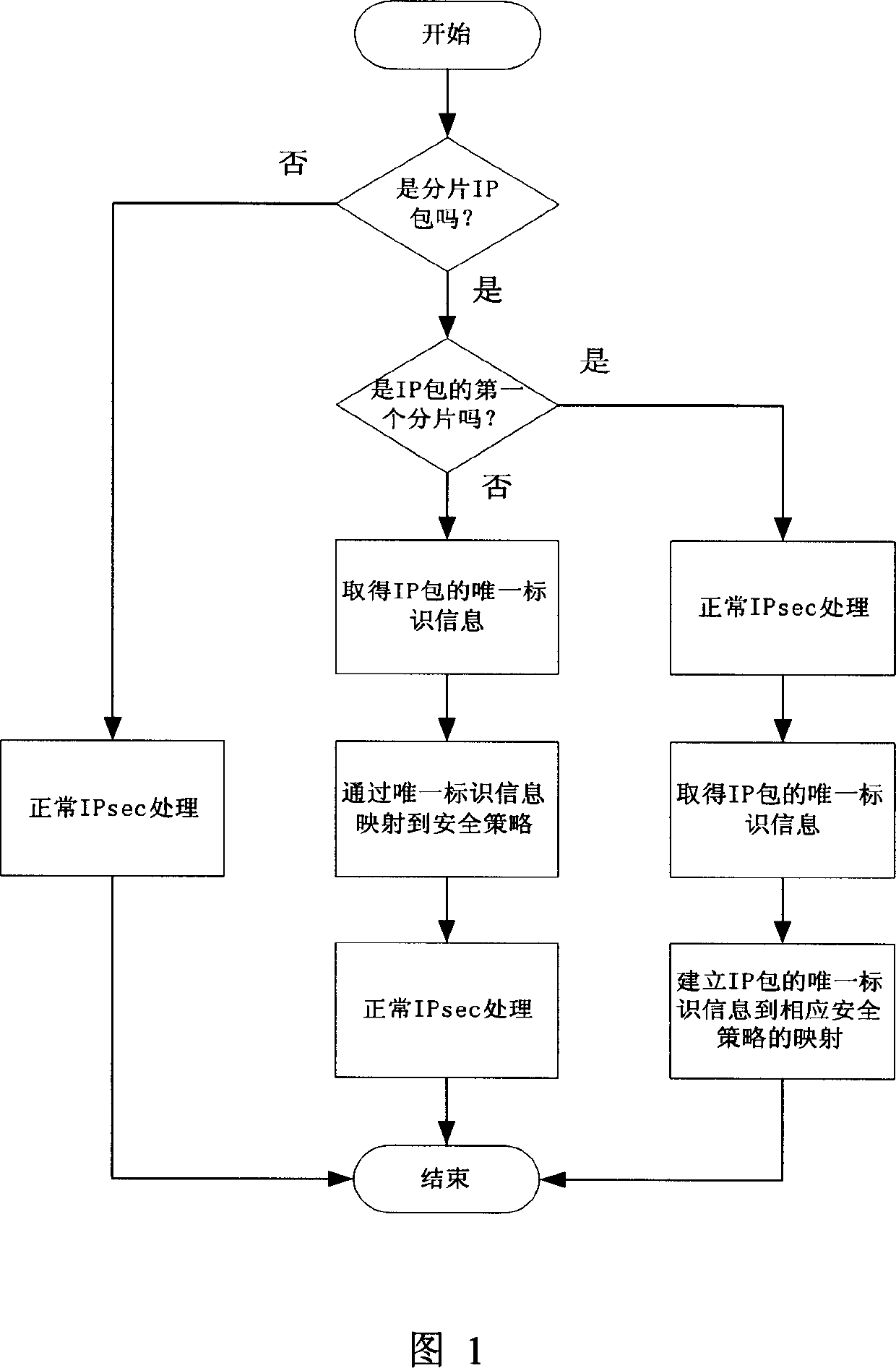
[0025] The method of the present invention will be further described below in combination with specific embodiments.
[0026] The invention mainly proposes a method for IPsec to process IP fragmentation at high speed through mapping.
[0027] In the typical IPsec VPN network environment shown in Figure 3, the VPN gateway is a high-speed network device enabling IPsec, and the communication between the left subnet and the right subnet passes through the IPsec tunnel between the VPN gateways. Communication between host A and server B uses UDP port x, and communication between host A and server C uses UDP port y. The VPN gateway provides different levels of IPsec security protection for different services. Assume that the security policy configuration on the IPsec VPN gateway requires AH tunnel protection for communication on UDP port x, and ESP tunnel protection for communication on UDP port y. The security policy on the left IPsec VPN gateway is as follows:
[0028] s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com