Cooperative intrusion detection based large-scale network security defense system
A technology of intrusion detection and network security, which is applied in the field of computer security, can solve the problems of small scale of cooperation, high attack hazard, and unobvious attack behavior, and achieve the effect of preventing coordinated intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in further detail below in conjunction with the accompanying drawings.
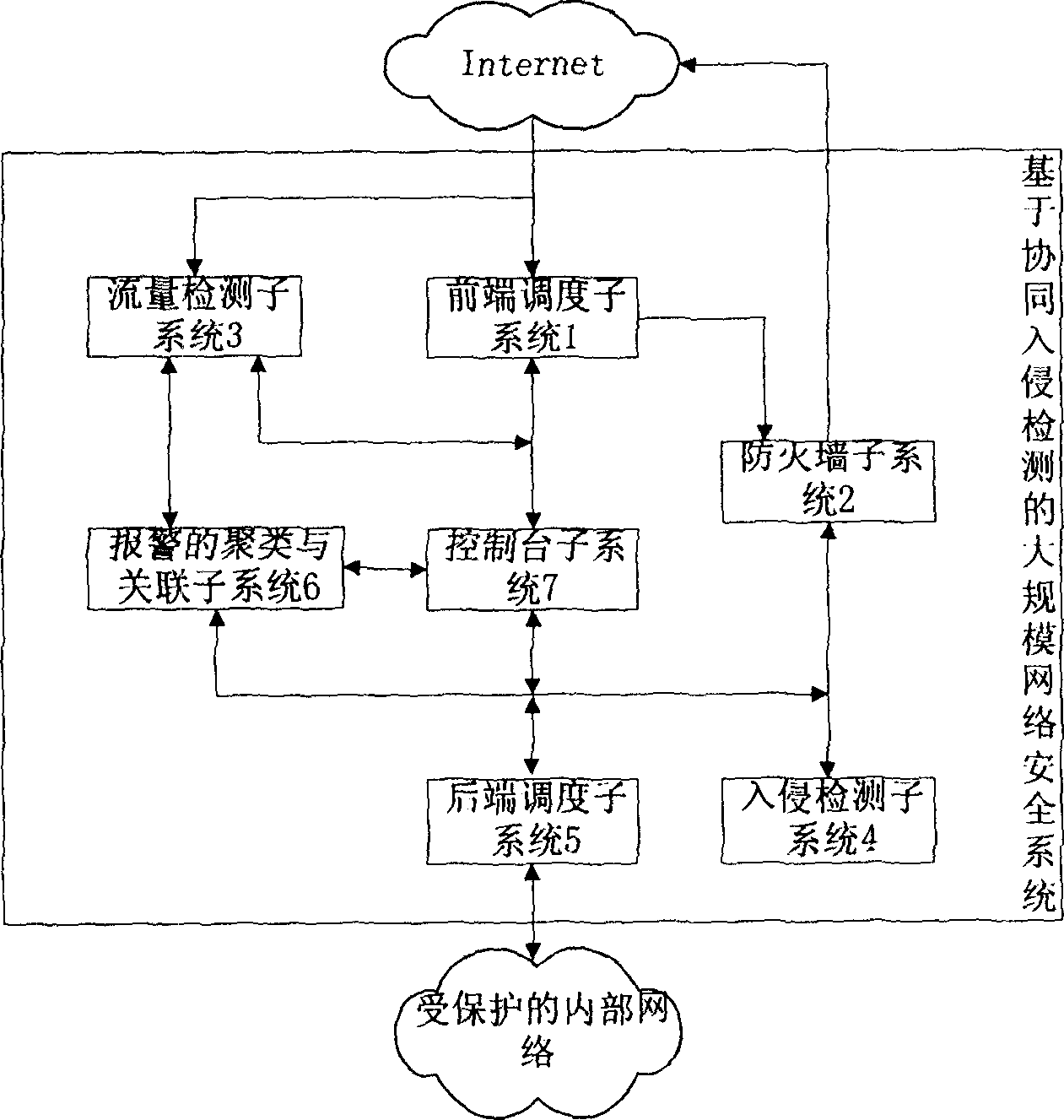
[0047] like figure 1 As shown, the present invention uses a front-end scheduling subsystem 1, a firewall subsystem 2, a traffic detection subsystem 3, an intrusion detection subsystem 4, a back-end scheduling subsystem 5, an alarm clustering and association subsystem 6, and a console subsystem 7 Inherent tight cooperation to achieve the detection and defense of coordinated intrusion.
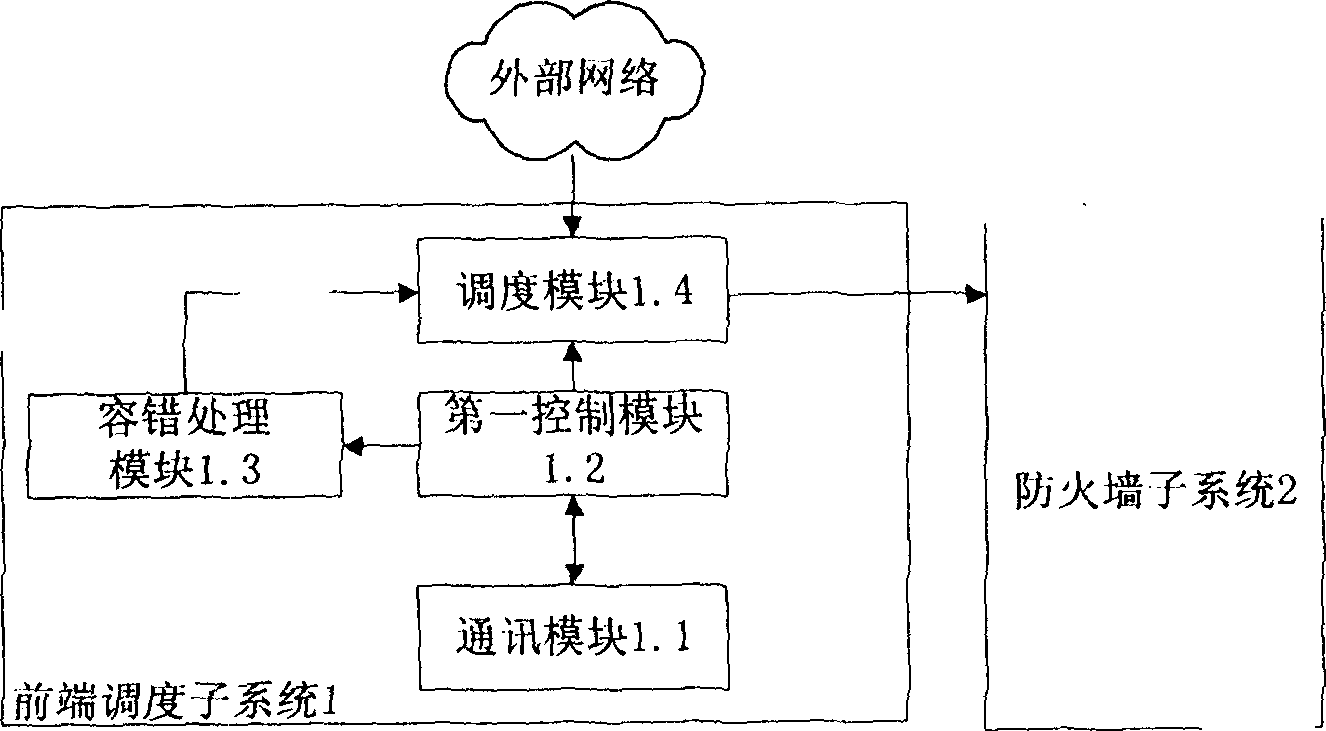
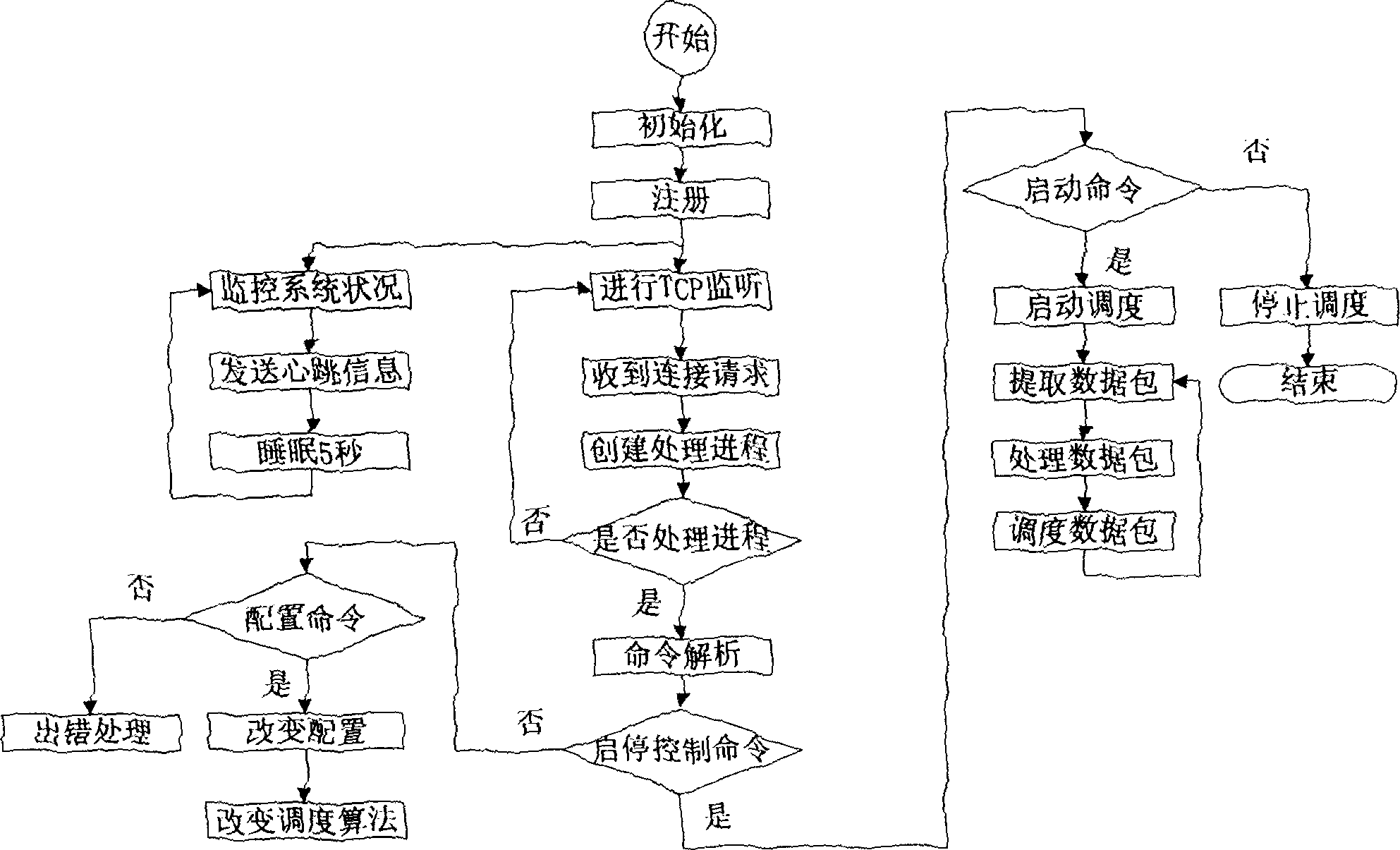
[0048] The front-end scheduling subsystem 1 is used to communicate with the console subsystem 7. According to the obtained status information about the firewall subsystem 2, it performs load scheduling based on the fault-tolerant hash scheduling algorithm for data packets entering from the external network, and adopts a dual-machine The fault-tolerant processing is carried out in the way of hot backup to ensure that when the main scheduler fails, the backup scheduler can succe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com