Dual-code symmetric anti-faking method
A symmetric and anti-counterfeiting identification technology, applied in the field of data identification, can solve the problems such as the inability to continue to sell goods, consumers unable to verify the authenticity of goods, and affecting the normal sales of products.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The dual-code symmetric anti-counterfeiting method includes the following operating procedures:
[0030] 1. Coding of symmetrical anti-counterfeiting digital
[0031] The code of symmetrical anti-counterfeiting digital is two groups of 16-21 digits. Now take the 16-bit coding method as an example to illustrate the following:
[0032]
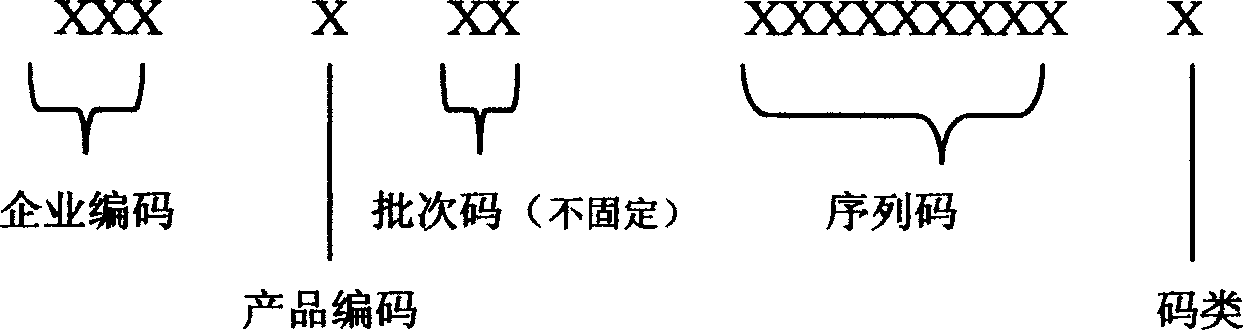
[0033] The coding structure is explained as follows:
[0034] No. 1-3: Company code, which can compile the codes of 1000 companies;
[0035] No. 4: Product code, 10 kinds of product codes can be compiled;
[0036] Digits 5-6: Lot code, not fixed, it can be two digits or three digits. Identify the batch number of each batch of anti-counterfeiting codes;
[0037] Digits 7-15: Serial code, which indicates the serial number of each set of anti-counterfeiting numbers for each product;
[0038] The 16th digit: Code type, which indicates the type of each group of anti-counterfeiting numbers. When the code type is 1, the group of anti-counterfeitin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com