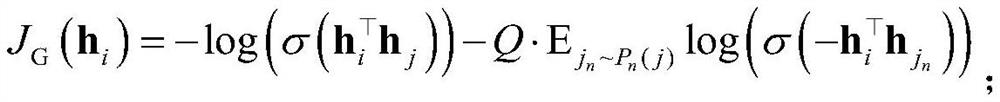VoIP malicious behavior detection method and system based on heterogeneous neural network technology
A neural network and detection method technology, applied in the field of VoIP malicious behavior detection, can solve the problems of lack of association analysis of multiple data sets, single data source, inability to mine implicit and explicit relationships of VoIP behavior, etc., so as to facilitate multi-dimensional information. Fusion and correlation network construction, the effect of improving detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the above-mentioned features and advantages of the present invention more obvious and easy to understand, the following embodiments are given and described in detail with the accompanying drawings as follows.
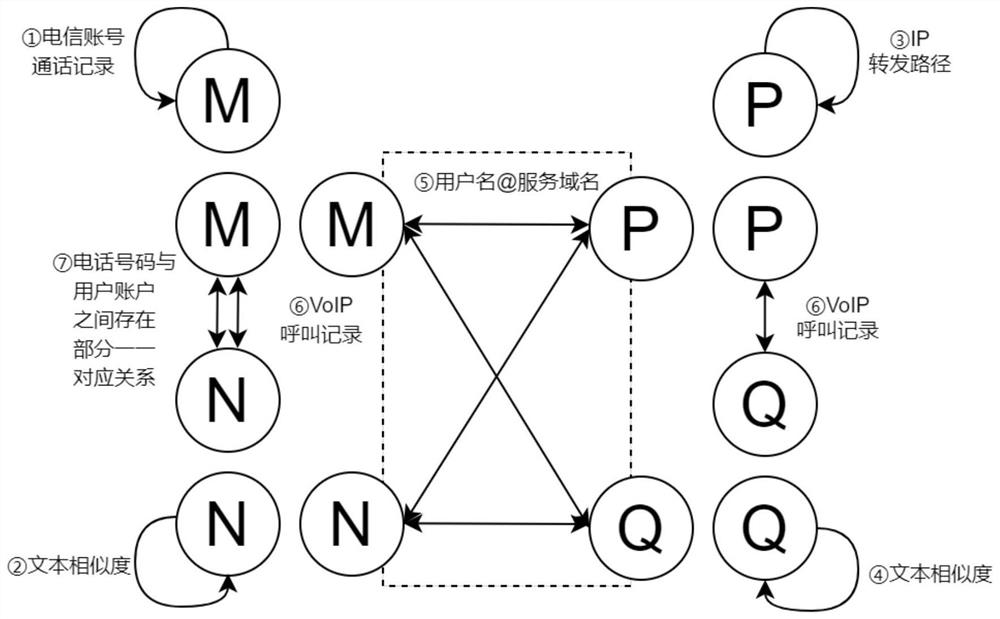
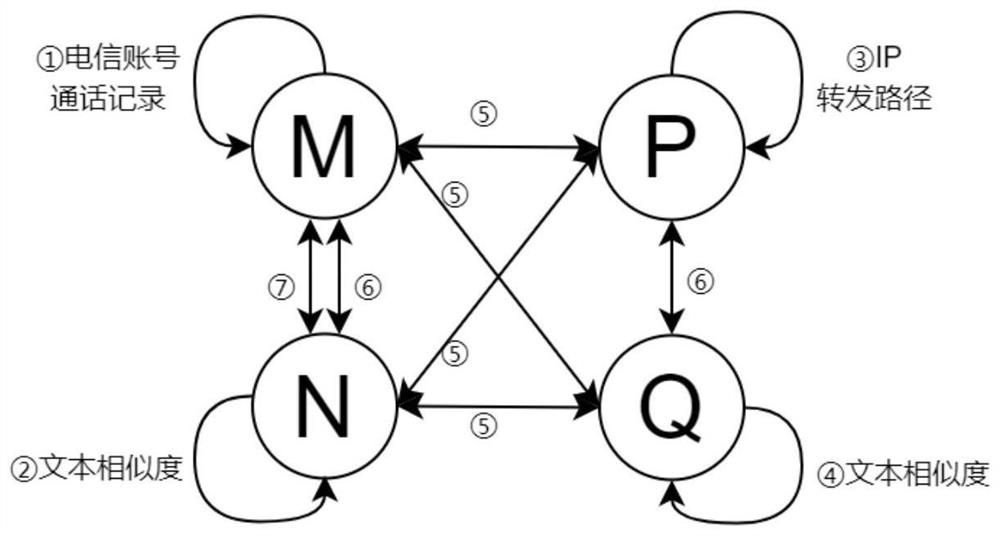
[0025] This embodiment discloses a method for detecting malicious VoIP behaviors based on heterogeneous neural network technology, which uses heterogeneous information networks to detect malicious VoIP behaviors under multiple VoIP data sources. This embodiment uses heterogeneous information formed by VoIP multiple data sources network instance such as figure 1 Specifically, the following processing steps are included:
[0026] Step 1: Extract information objects from multiple data sources.
[0027] The multi-data source information in this embodiment includes: m∈M is the set of phone numbers, n∈N is the set of VoIP user names in the form of non-telephone numbers, p∈P is the set of IP-type service domain names, and q∈Q is A collection of servic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com