Weblogic deserialization vulnerability scanning detection method and tool
A vulnerability scanning and vulnerability detection technology, applied in the field of network information security, can solve problems affecting the efficiency of server vulnerability scanning and detection, troubles, etc., and achieve the effect of increasing the efficiency of vulnerability detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
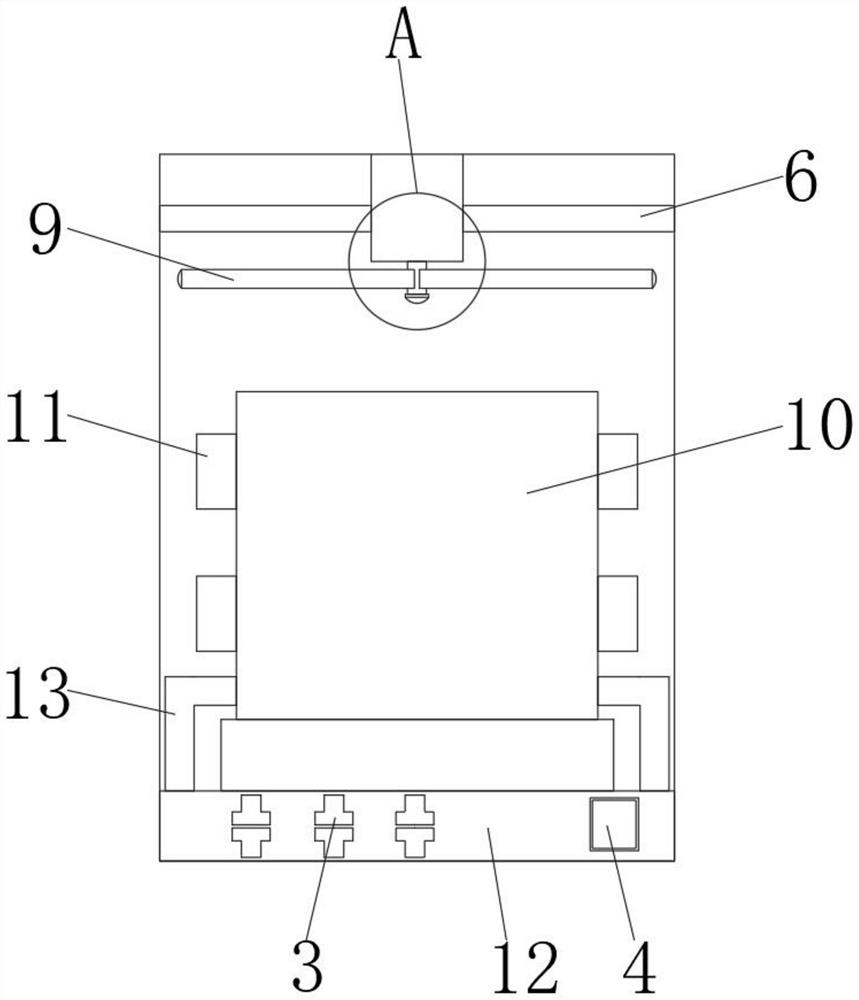
[0047] A Weblogic deserialization vulnerability scanning detection method and tool, comprising a vulnerability detection tool ontology 1, a vulnerability scanning host 10, a vulnerability detection module 15 and a deserialization processing module 19, the vulnerability detection tool ontology 1 is provided with a vulnerability scanning host 10, The vulnerability scanning host 10, the input end of the vulnerability scanning host 10 and the input end of the vulnerability detection server 14 are connected to each other, the vulnerability scanning host 10 is provided with a vulnerability detection module 15, the output end of the vulnerability detection module 15 and the input end of the vulnerability verification module 16 Connected to each other, the output end of the vulnerability verification module 16 and the input end of the data transmission module 17 are connected to each other, the output end of the data transmission module 17 and the input end of the vulnerability detectio...
Embodiment 2
[0057] A Weblogic deserialization vulnerability scanning detection method includes the following steps:
[0058] Step 1: Connect multiple Weblogic servers to the vulnerability detection tool ontology 1;
[0059] Step 2: The vulnerability scanning interface 18 is initialized by the deserialization processing module 19, so that the detection interface, domain name address, detection result, and user instruction are restored to the initial operating state at the same time;
[0060] Step 3: Perform vulnerability scanning on the host, port and database of the Weblogic server respectively through the host scanning detection module 26, port scanning detection module 27, and database scanning detection module 28 to which the vulnerability detection module 15 belongs, and pass the OS scanning and identification module 29 Protocol identification for Weblogic server;
[0061] Step 4: After the vulnerability scanning and detection of the Weblogic server, the vulnerability verification mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com