Quantum identity authentication method and system based on continuous variable quantum key distribution
A technology of quantum key distribution and identity authentication, applied in the field of quantum identity authentication based on continuous variable quantum key distribution, it can solve the problems that continuous variable quantum identity authentication is rarely researched, and achieve the advantages of reduced application cost and good application flexibility. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
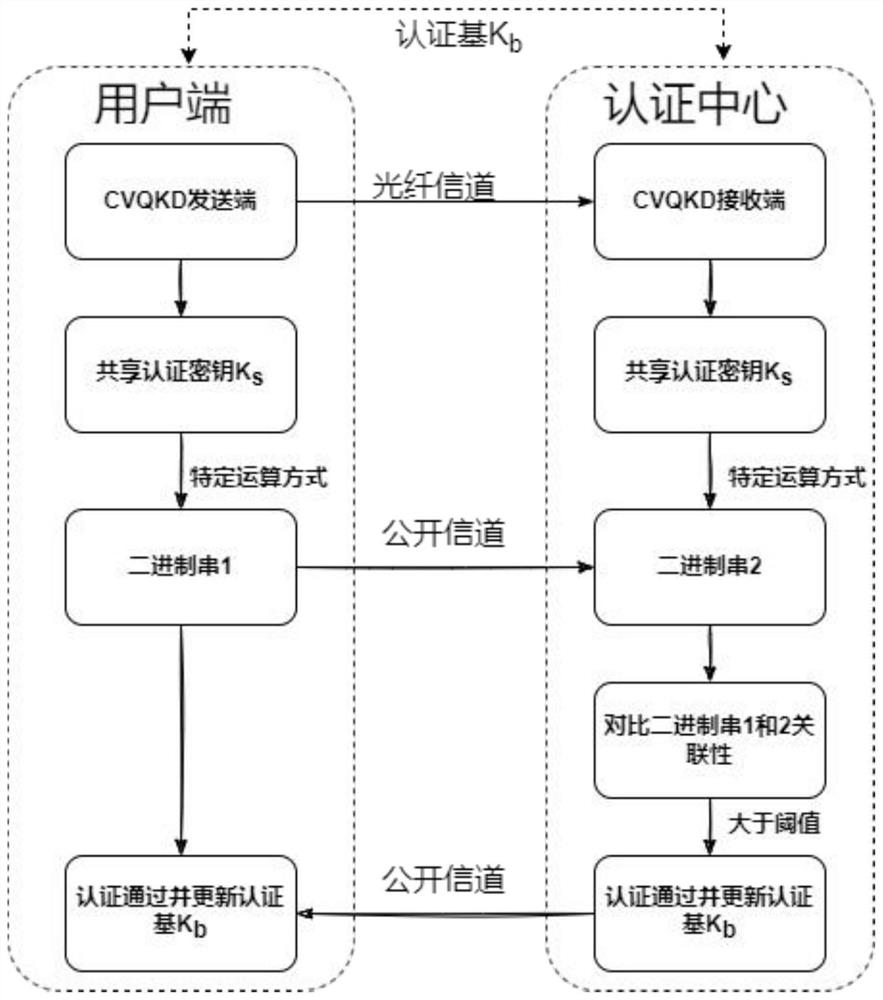
[0039] A quantum identity authentication method based on continuous variable quantum key distribution provided according to the present invention, comprising:
[0040] Step S1: The client and the authentication center share the authentication key K through the continuous variable quantum key distribution system s , K s is a binary bit string with a length greater than or equal to 2N; wherein, the first N lengths are used for calculation, and the length of N+1 to 2N is selected for updating the authentication base K b , the remaining length can be ignored;
[0041] Specifically, the step S1 adopts: in the user terminal and the authentication center, use any Gaussian modulation coherent state continuous variable quantum key distribution protocol with unconditional security to perform identity authentication.
[0042] Step S2: Obtain the authentication key K s The first N binary bits in the middle, get the binary bit string K of length N a ; the client uses the binary bit str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com