Secure chip burning method and system
A programming method and technology for a programming system, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as increasing management and operation costs, avoid open network transmission, solve leakage problems, and achieve high security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
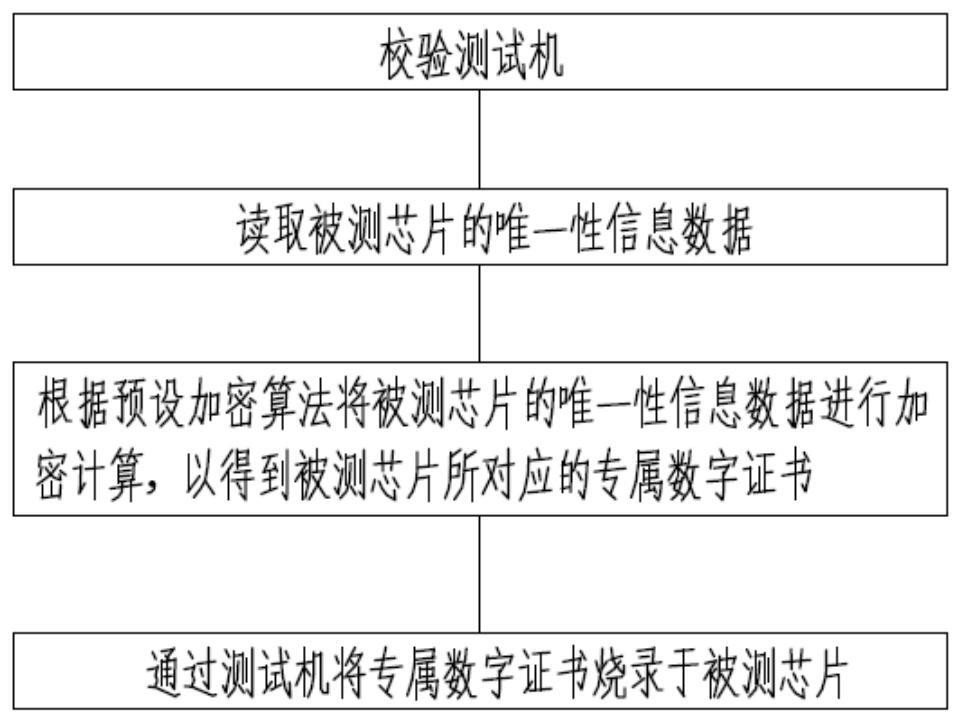
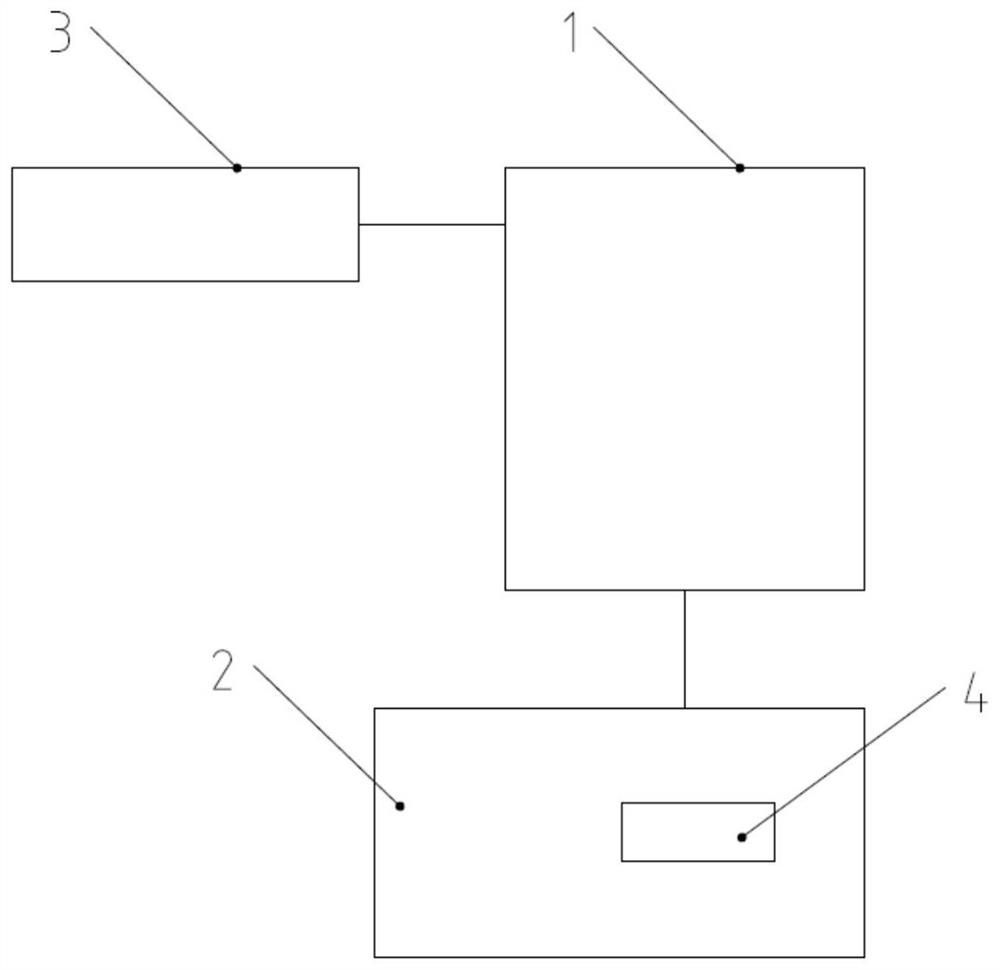
[0035] Such as figure 1 A safe chip programming method is shown, the method specifically includes the following steps: verifying the testing machine; reading the unique information data of the tested chip; performing the unique information data of the tested chip according to a preset encryption algorithm Encrypt calculation to obtain the exclusive digital certificate corresponding to the tested chip; burn the exclusive digital certificate to the tested chip through the testing machine.
[0036] Through the above method, the programming content is obtained by reading the unique information data of the chip under test and then calculated with an encryption algorithm, which shortens the transmission link of the programming content of the chip under test, and the entire data transmission is completely carried out in the hardware security environment, avoiding cross The open network transmission of the hardware solves the leaking problem caused by the separate distribution of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com