PKG bait file generation method and system
A file generation and file technology, applied in the field of red-blue confrontation exercises, to achieve the effect of achieving consistency and simple production
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
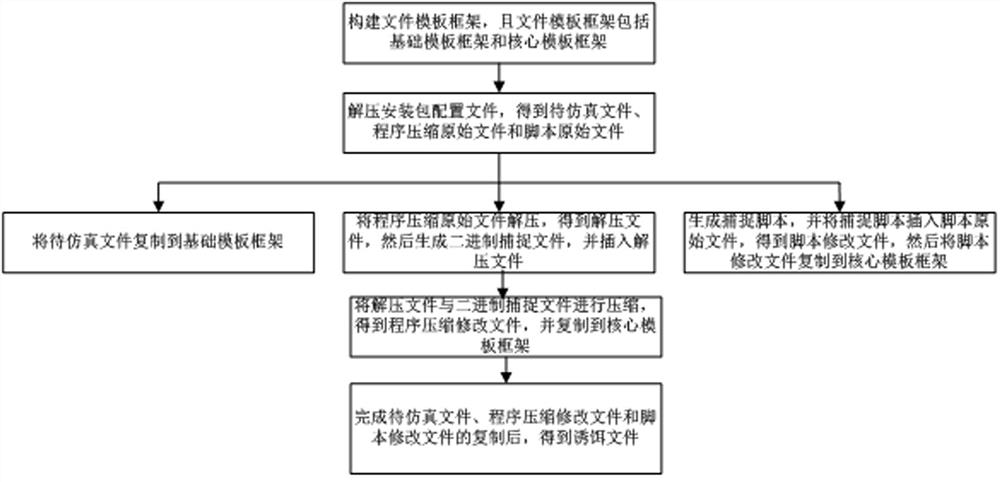
[0040] Such as figure 1 As shown, a method for generating a PKG decoy file includes the following steps: decompressing the configuration file of the installation package to obtain the file to be emulated, the original compressed program file and the original script file. When making the decoy file, it is necessary to make the decoy file have both the The high similarity of the real installation package configuration file is used to confuse the attacker, and it is necessary to make the decoy file capture the attacker when it is attacked by the attacker, so as to inform the staff through the captured information that there is an attacker intrusion, and make a Intrusion alert prompt.
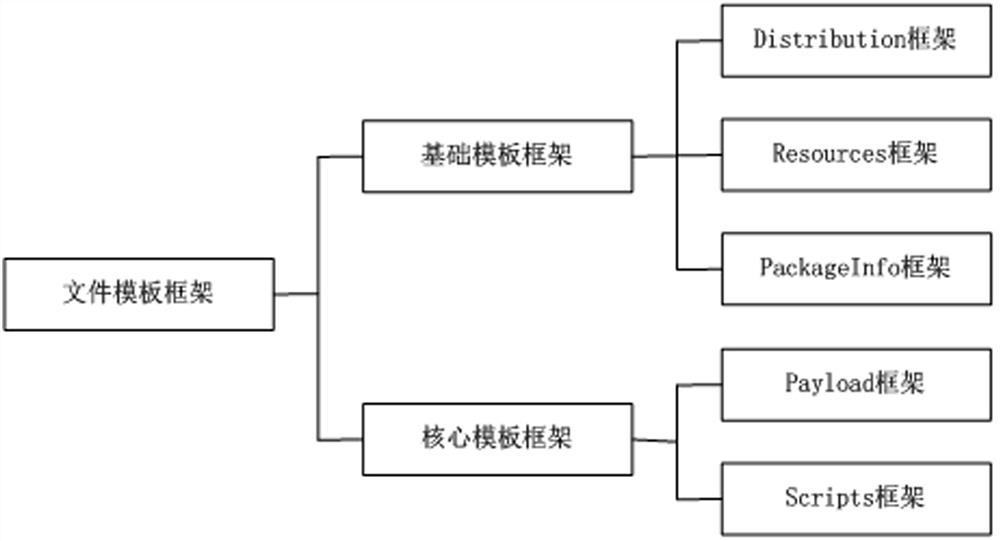
[0041] Among them, to improve the high similarity between the decoy file and the installation package configuration file, it is necessary to construct the file template framework of the decoy file. Specifically, it includes the following steps: obtain several installation package configuration file...
Embodiment 2
[0057] A PKG decoy file generation system, including: a first acquisition module, used to decompress the configuration file of the installation package to obtain the file to be simulated, the original file of the program compression and the original file of the script, and also used to decompress the original file of the program compression , to get the decompressed file, when making the decoy file, it is necessary to make the decoy file not only have a high similarity with the real installation package configuration file to confuse the attacker, but also need to make the decoy file be attacked by the attacker. Capture, so as to inform the staff through the capture information that there is an attacker intrusion, and make an intrusion alarm prompt.
[0058] Among them, to improve the high similarity between the decoy file and the configuration file of the installation package, it is necessary to construct the file template framework of the decoy file. Therefore, the constructio...
Embodiment 3
[0069] A computer-readable storage medium stores a computer program, and when the computer program is executed by a processor, the method for generating a PKG decoy file described in Embodiment 1 is realized.
[0070] More specific examples of computer-readable storage media may include, but are not limited to, electrical connections with one or more wire segments, portable computer diskettes, hard disks, random access memory (RAM), read-only memory (ROM), erasable Programmable read-only memory (EPROM or flash memory), optical fiber, portable compact disk read-only memory (CD-ROM), optical storage device, magnetic storage device, or any suitable combination of the above.
[0071] In the present application, a computer-readable storage medium may be any tangible medium that contains or stores a program that can be used by or in conjunction with an instruction execution system, apparatus, or device. In this application, however, a computer-readable signal medium may include a da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com