Big data security and privacy computing control method in supercomputing and cloud computing environment
A cloud computing environment and control method technology, applied in computer security devices, computing, digital data protection, etc., can solve the problem of original data leakage, difficulty in meeting computing needs, and inability to know whether the data is real or tampered, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be described in further detail below in conjunction with the accompanying drawings.
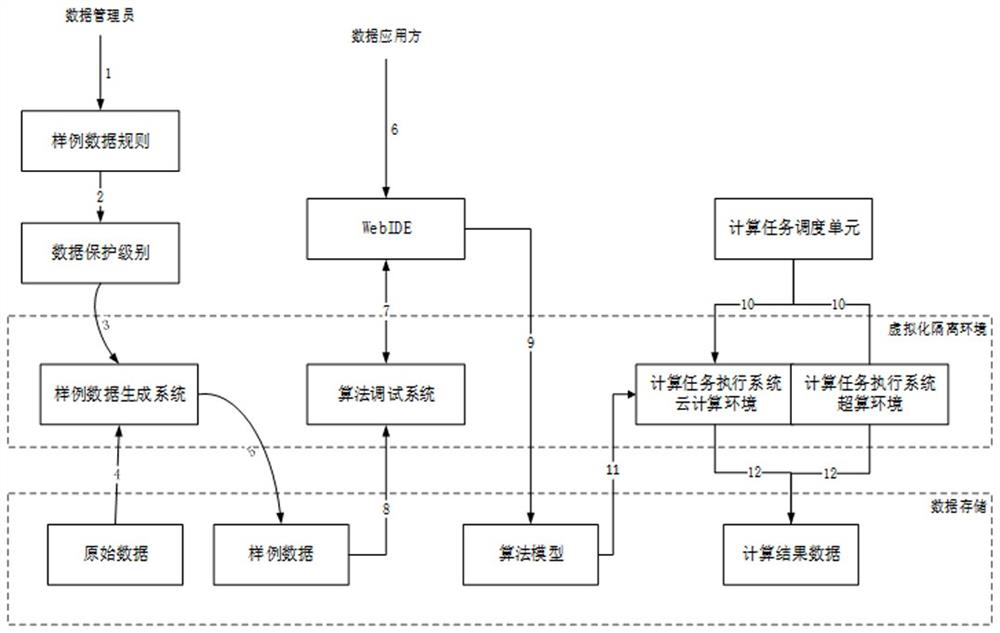
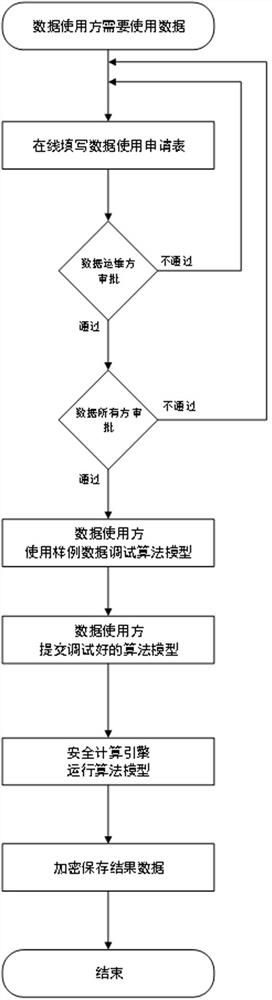
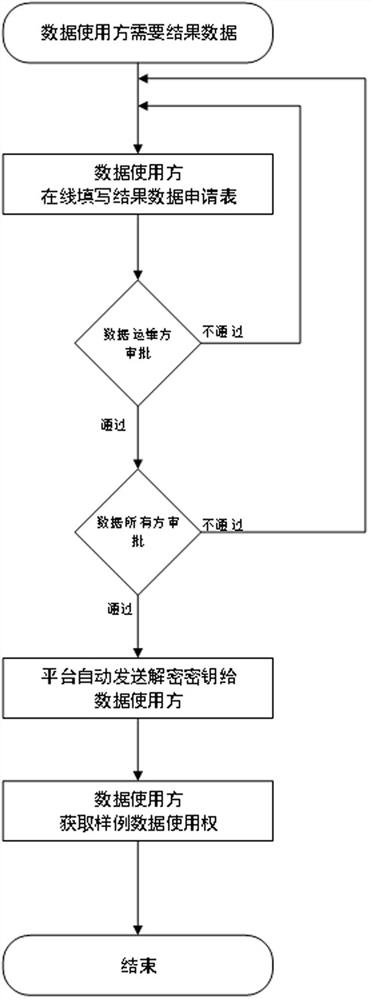
[0046] Big data security and privacy computing control methods in supercomputing and cloud computing environments, such as figure 1 shown, including the following steps:
[0047] Step 1. The original data provider sets the sample data rules, and the data administrator enters the sample data rules.
[0048] Step 2. The data administrator judges the data protection level of the original data according to the sample data rules.
[0049] Among them, different protection levels are set for the sensitivity of sensitive information in the original data.
[0050]Step 3. According to the data protection level determined in step 1 and according to the sample data generation system, the original data is desensitized and collected, and sample data is generated. Among them, the data protection level can choose a default desensitization method for certain sensitive info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com