External storage device encryption and decryption system and method based on Kylin mobile operating system
A mobile operating system and external storage technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as encryption and decryption of USBOTG devices without external memory cards, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
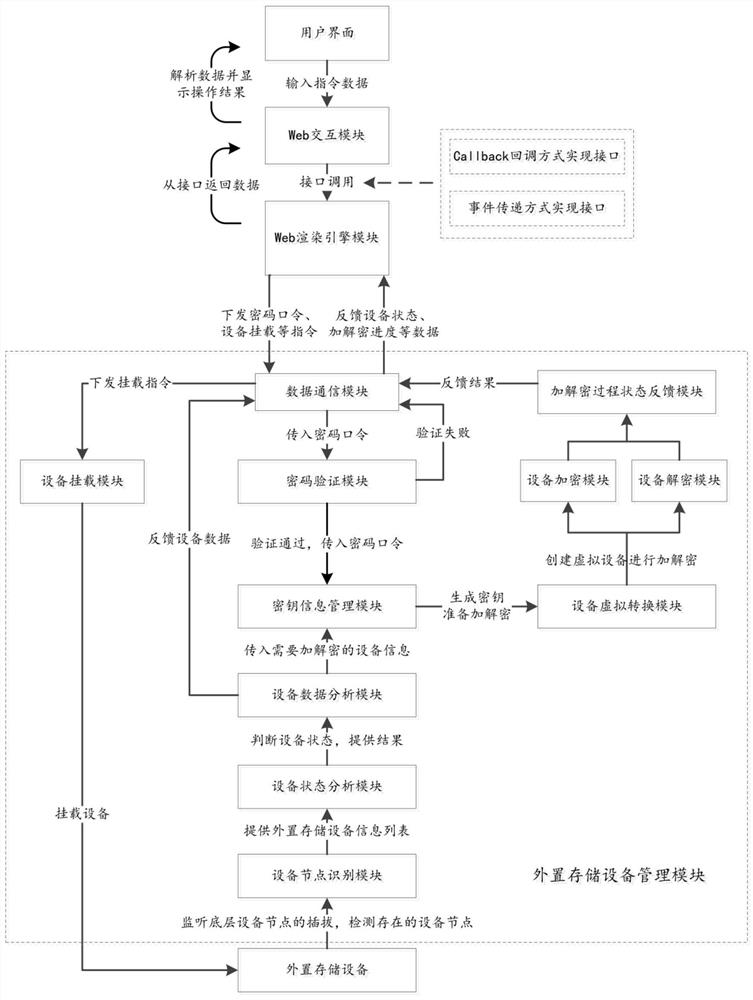
[0057] Such as figure 1 As shown, this embodiment proposes an external storage device encryption and decryption system based on the Kirin mobile operating system, including:
[0058] The Web interaction module is used to obtain operation instructions, call the encryption and decryption interface and input operation instructions to the encryption and decryption interface, and wait for the feedback data of the encryption and decryption interface;
[0059] The Web rendering engine module is used to provide an encryption and decryption interface, obtain operation instructions from the encryption and decryption interface and forward them to the external storage device management module, and wait for the feedback data from the external storage device management module, and then pass the encryption and decryption interface Send the feedback data to the Web interaction module;
[0060] The external storage device management module is used to identify the external storage device and f...
Embodiment 2
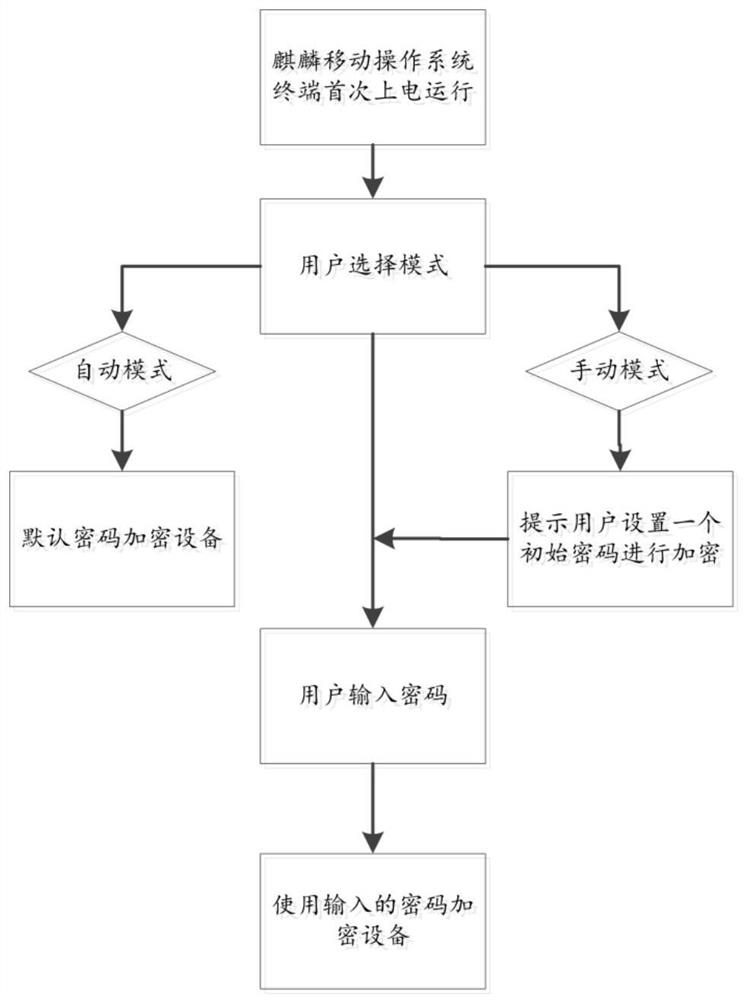
[0086] This embodiment proposes a method for encrypting and decrypting an external storage device based on the Kirin mobile operating system based on Embodiment 1, including the following steps:
[0087] S1) The Web interaction module obtains the operation instruction, calls the encryption and decryption interface and inputs the operation instruction to the encryption and decryption interface;
[0088] S2) The Web rendering engine module obtains the operation instruction from the encryption and decryption interface and forwards it to the external storage device management module;
[0089] S3) The external storage device management module obtains the operation instruction from the Web rendering engine module, mounts the corresponding virtual device after determining the target external storage device according to the operation instruction, and generates an encryption key or decryption key, and then passes the virtual device Encrypt or decrypt the data in the target external sto...
Embodiment 3
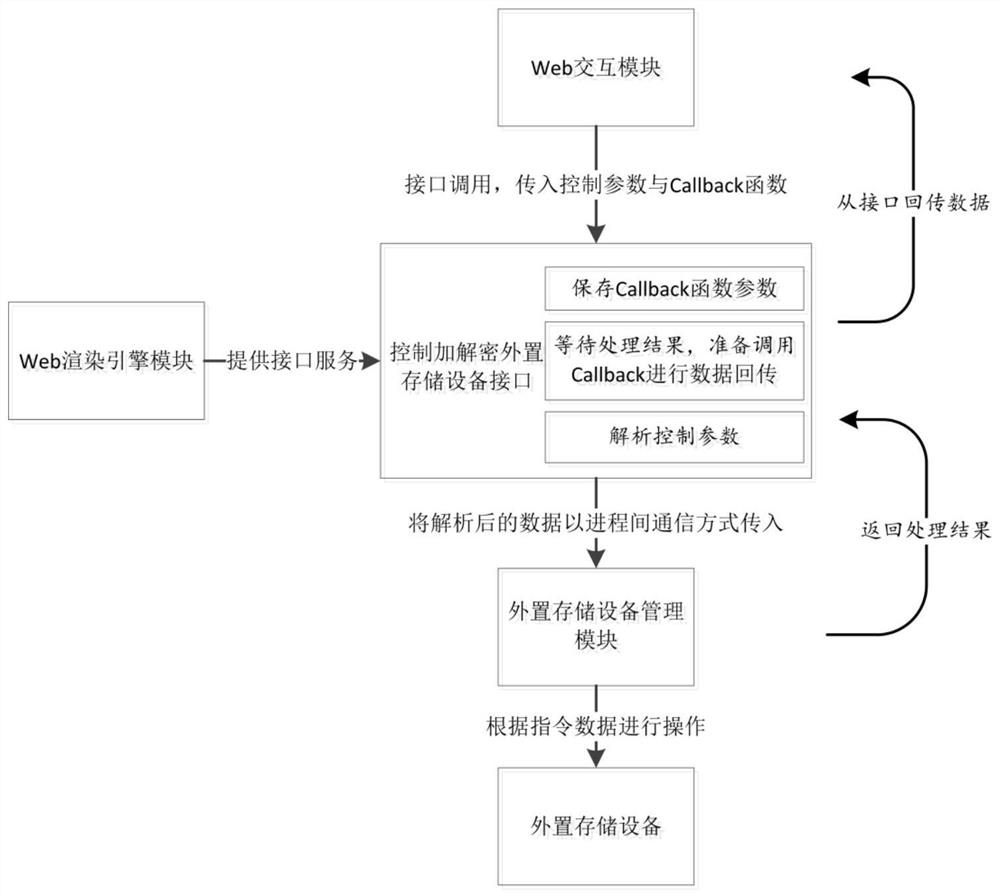
[0123] This embodiment is basically the same as Embodiment 2, the difference is that, as Figure 5 As shown, the implementation of the encryption and decryption interface in this embodiment is as follows:
[0124] Interface input: data parameters such as control commands and passwords.
[0125] Interface output: event.
[0126] In this embodiment, the Web rendering engine module registers parameters for processing and storing encryption-related event attributes, creates and initializes event processing functions, and then dispatches events. The Web interaction module calls the encryption and decryption interface of the Web rendering engine module, passes in the control parameters and performs event monitoring, the control parameters are input, and the event monitoring is used to receive the events dispatched by the Web rendering engine module. The event object includes the events sent by the Web rendering engine module to The data of the Web interactive module. After the We...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com