Extensible Internet of Things big data and service security management method based on side chain
A security management and Internet of Things technology, applied in the field of Internet of Things big data and service security management, can solve problems such as poor security, large data and service security limitations, achieve security and fairness, reduce load, and improve payment efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
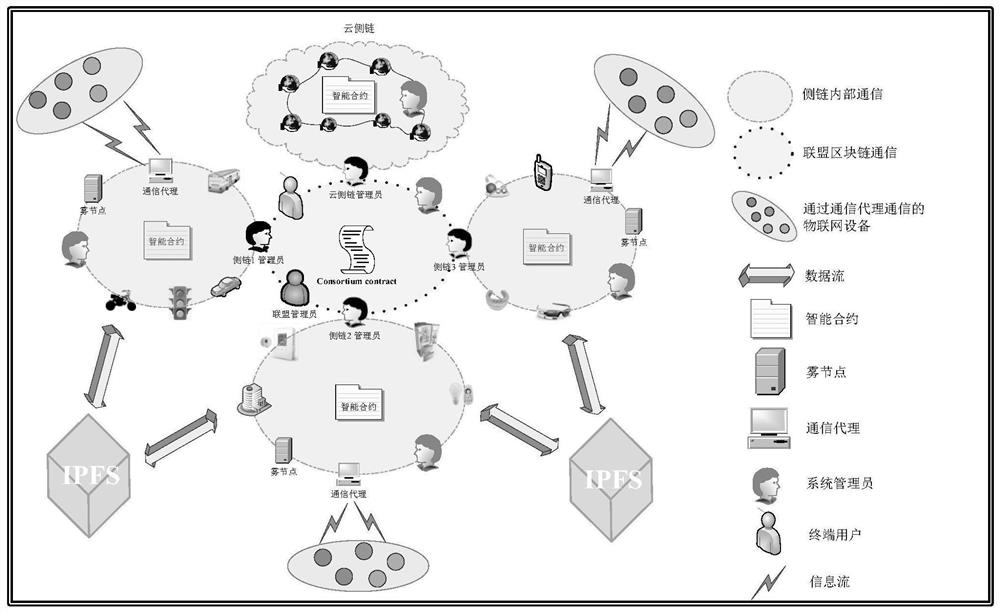
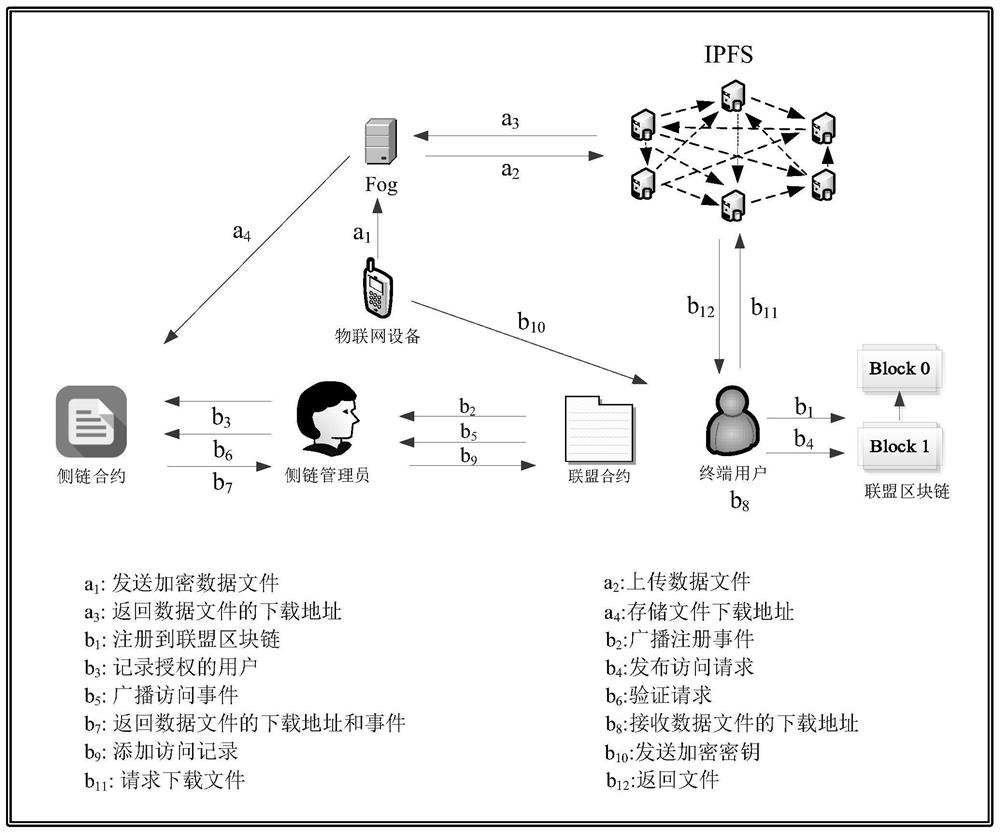
[0075] In the method of the present invention, a system administrator is designated to initialize the alliance block chain and side chain, and three types of smart contracts are designed, including alliance contract, side chain contract, and cloud side chain contract, and the entity authentication mechanism and access control The rules are embedded in the smart contract, and then the alliance contract is deployed in the alliance blockchain, the sidechain contract is deployed in the sidechain, and the cloud sidechain contract is deployed in the cloud sidechain.
[0076] The present invention is specifically as follows:
[0077] to combine Figure 1 ~ Figure 2 , Step 1. System initialization: System initialization includes two stages: initializing the blockchain and initializing the smart contract;
[0078] Step 1 is specifically implemented according to the following steps:
[0079] Step 1.1. Initialize the blockchain:
[0080] The system administrator sets the initial param...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com