Vulnerability mining method based on improved generative adversarial network framework
A vulnerability mining and network framework technology, applied in biological neural network models, neural learning methods, neural architectures, etc., can solve problems such as low vulnerability mining rate and low reception rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] specific implementation plan
[0021] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
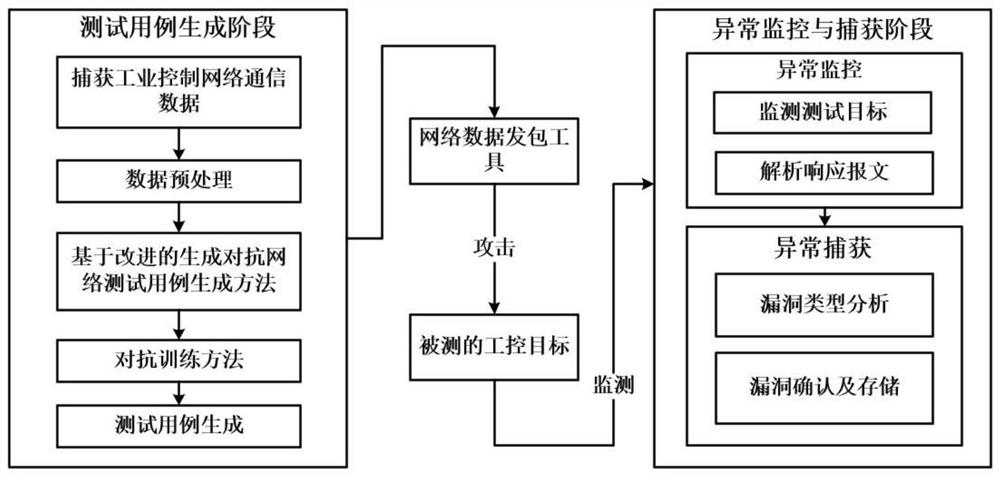
[0022] figure 1 It is a schematic diagram of the overall research idea of the vulnerability mining method in the present invention, which is divided into two stages: test case generation and exception monitoring and capture.
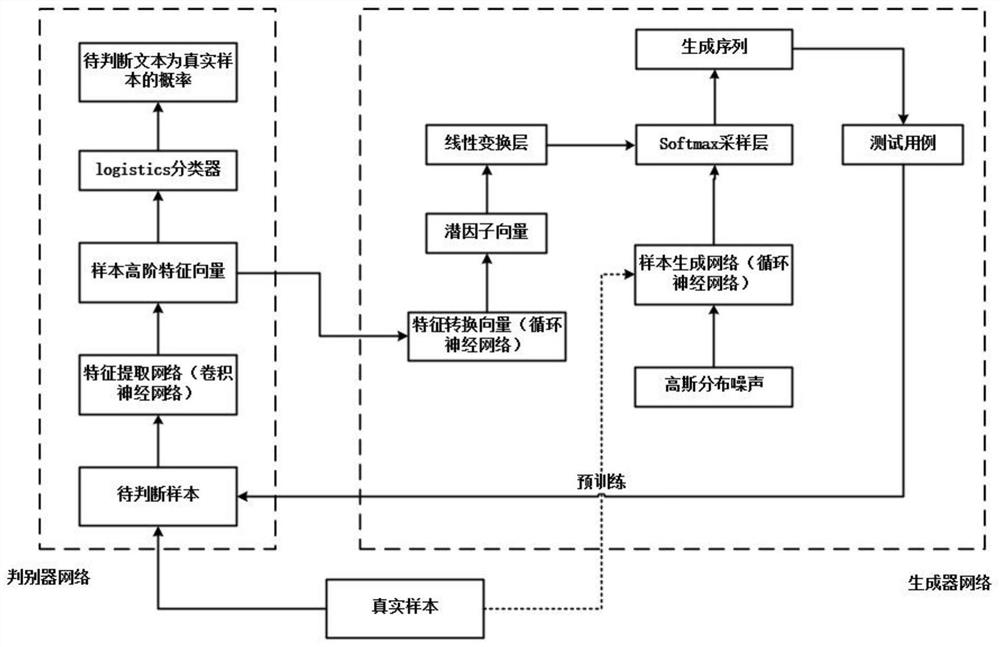
[0023] In the test case generation stage, the training data sets required by the model are firstly captured, which is realized by building a simulated Modbus-TCP protocol communication environment in the present invention, and then these original flow data sets are preprocessed. Then, aiming at the problem of mode collapse in the GAN model itself, an improved GAN framework is proposed; then, for the problem of insufficient feedback information obtained by the discriminator model, a dynamic feedback optimization method is proposed to achieve The goal of efficiently generatin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com