Method and system for multi-stream correlation analysis and identification of private encrypted data
A technology of encrypted data and correlation analysis, applied in the direction of digital transmission system, transmission system, character and pattern recognition, etc., can solve the problem of low accuracy and efficiency of feature code identification of encrypted data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
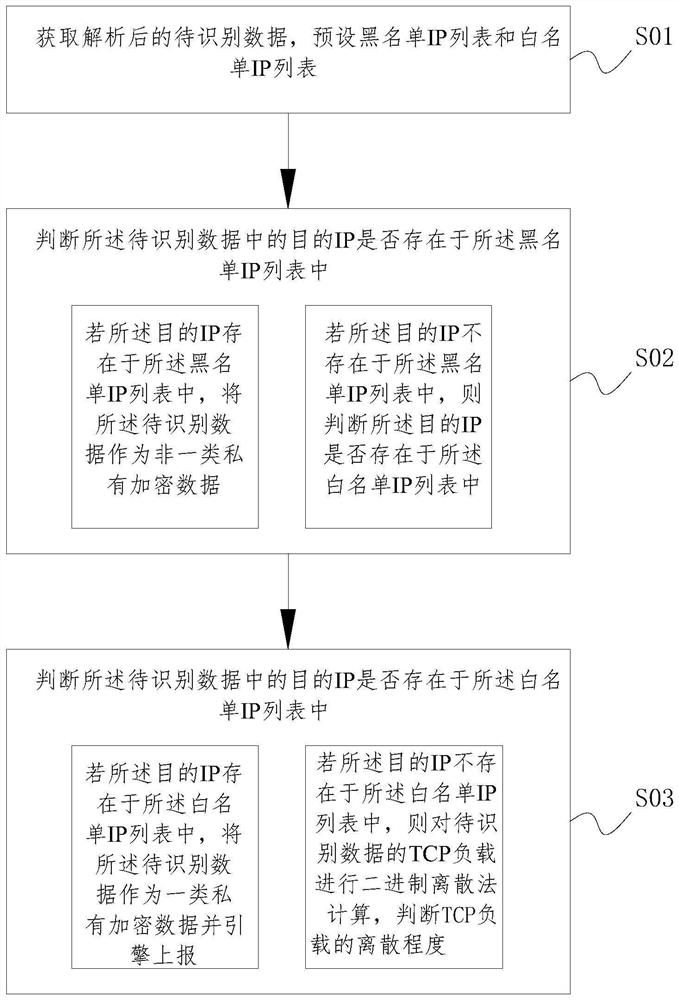
[0079] In Embodiment 1, during the loading process of the data to be identified, the data is collected through a Gigabit (or 10 Gigabit Ethernet port) in cooperation with the high-speed drive module of the network card.
[0080] According to the collected data, it is analyzed according to the four-layer protocol of TCP / IP (Ethernet layer, network layer, transport layer, application layer), and the standard protocol field is obtained, and the standard protocol field is used as the comparison object, as the basis for the logic judgment of the private protocol identification . The specific protocol analysis process and content of different layers are as follows:
[0081] 1) Ethernet layer protocol analysis:
[0082] Analyze VLAN protocol, PPPOE protocol, MPLS protocol, analyze user-defined Ethernet protocol or add additional private protocol data to Ethernet; analyze to get mac address, vlan id, network layer protocol id and other fields.
[0083] 2) Network layer protocol anal...
Embodiment 2
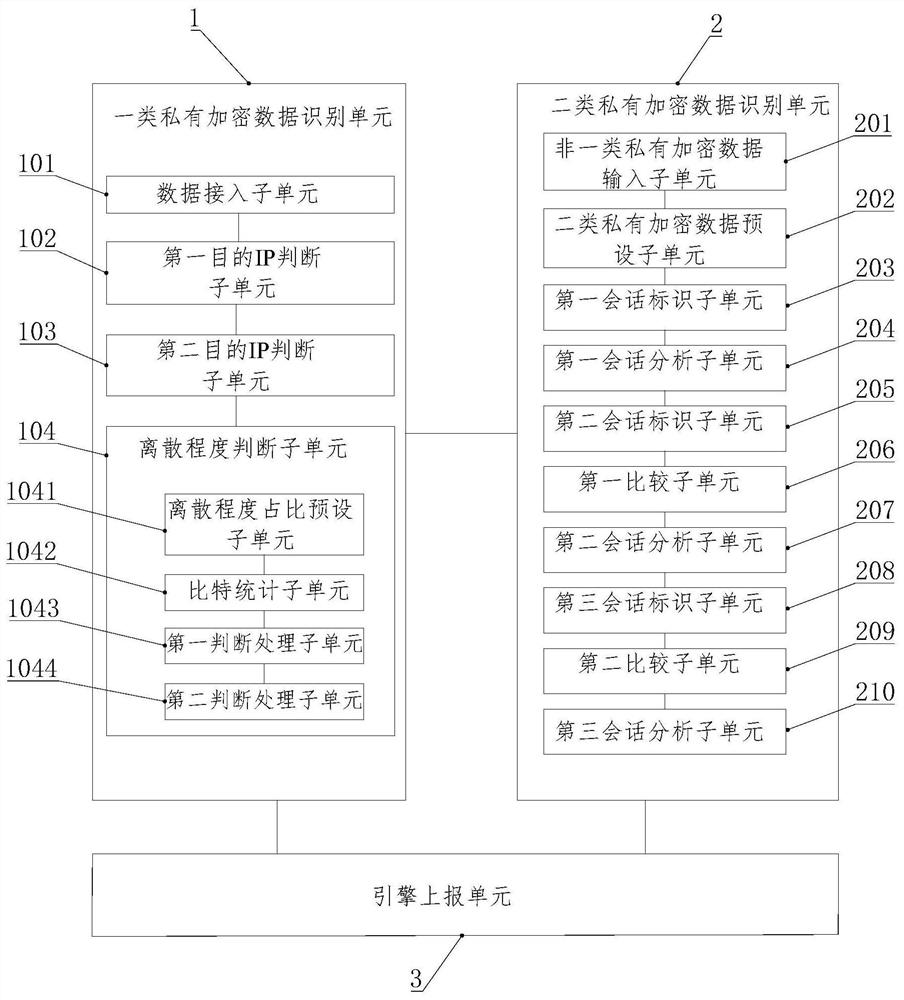
[0122] see image 3 Embodiment 2 of the present invention also provides that the present invention also provides a system for multi-stream correlation analysis and identification of private encrypted data, including a first-class private encrypted data identification unit 1, a second-class private encrypted data identification unit 2, and an engine reporting unit 3; The first class of private encrypted data identification unit 1 obtains non-class one private encrypted data; the second class of private encrypted data identification unit 2 performs second class private encrypted data identification from the non-class one private encrypted data; the engine reports Unit 3 reports the identified private encrypted data of type 1 and private encrypted data of type 2 to the engine;
[0123] The second type of private encrypted data identification unit 2 includes:
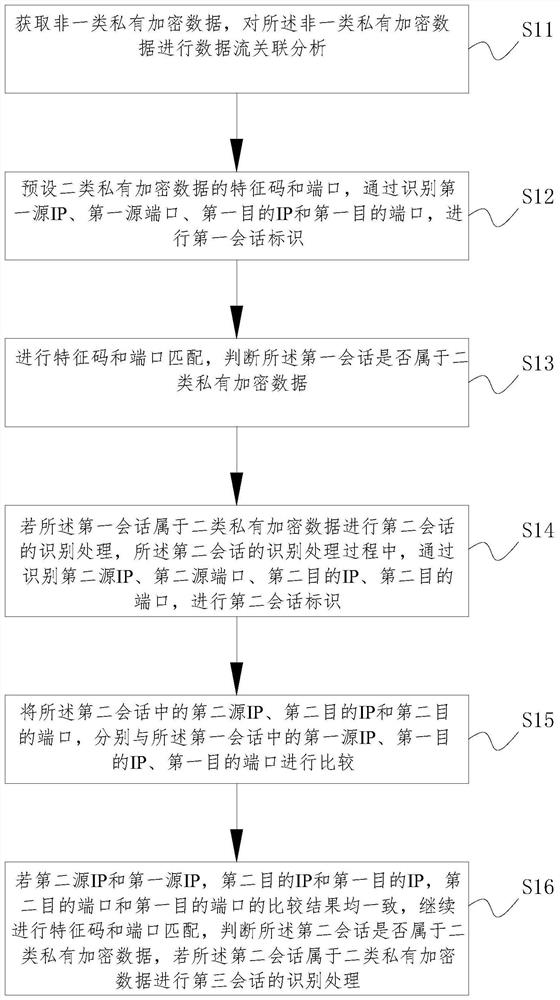
[0124] The non-class private encrypted data input subunit 201 is used to obtain the non-class private encrypted data, an...
Embodiment 3
[0154] Embodiment 3 of the present invention provides a non-transitory computer-readable storage medium. The computer-readable storage medium stores program code for a method for identifying private encrypted data through multi-stream correlation analysis. Instructions for multi-stream correlation analysis of Example 1 or any possible implementation thereof to identify methods of private encrypted data.
[0155] The computer-readable storage medium may be any available medium that can be accessed by a computer, or a data storage device such as a server, a data center, etc. integrated with one or more available media. The available medium may be a magnetic medium (for example, a floppy disk, a hard disk, or a magnetic tape), an optical medium (for example, DVD), or a semiconductor medium (for example, a solid state disk (SolidState Disk, SSD)).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com