Hardware implementation method and system for elliptic curve digital signature and signature verification
An elliptic curve and digital signature technology, applied in the field of information security, can solve the problems of high computational complexity, insufficient hardware performance, and difficult acceleration, and achieve the effects of low computational complexity, low hardware resource consumption, and easy hardware implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
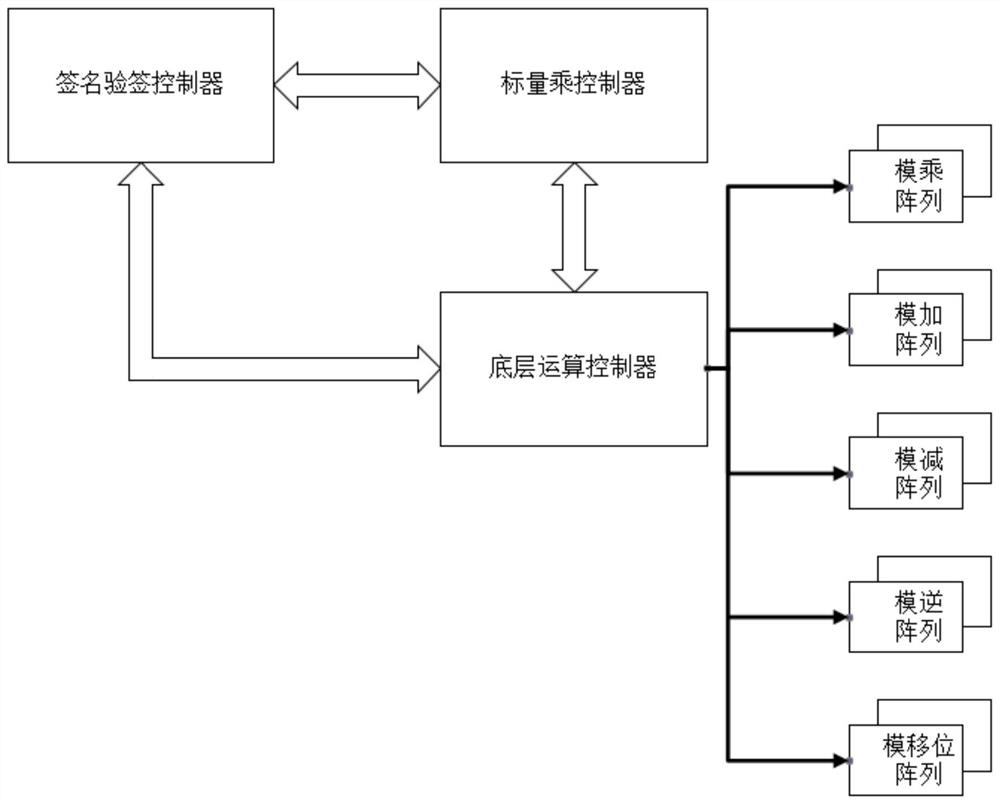
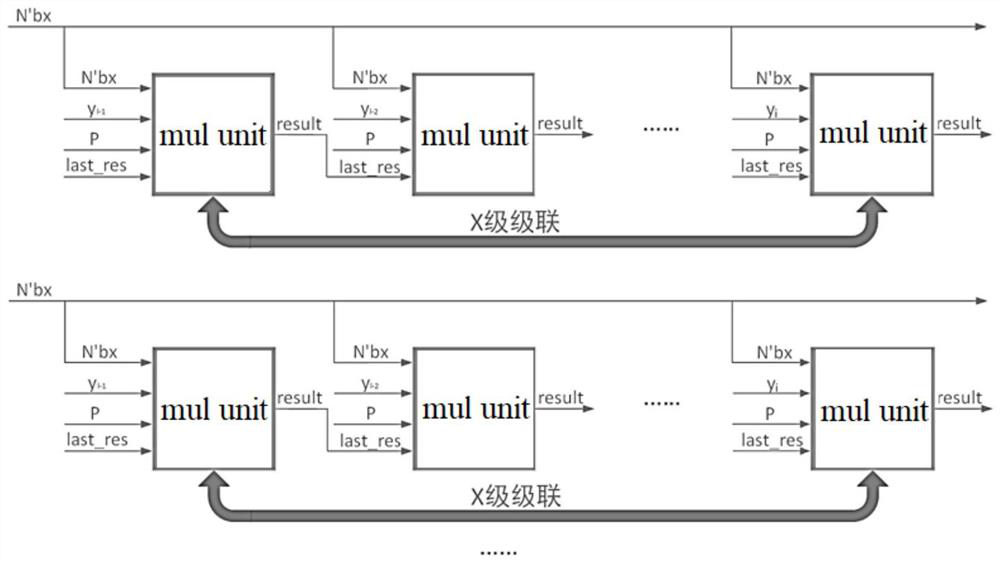
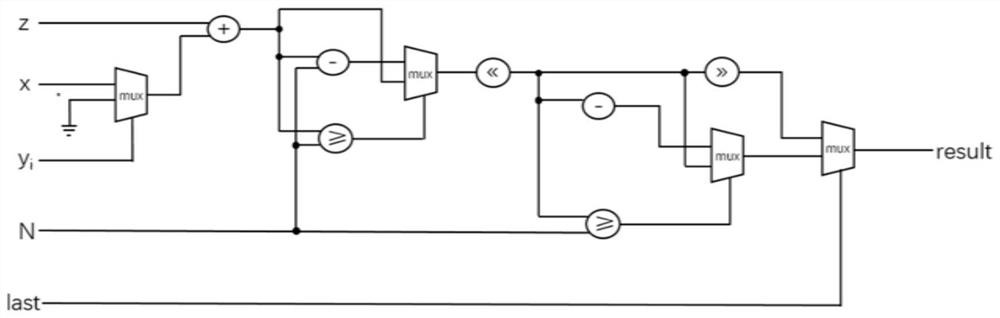
[0104] This embodiment discloses a hardware implementation method of high-performance elliptic curve digital signature and signature extension. First, the calculation path of the elliptic curve digital signature algorithm is analyzed, and the entire algorithm is divided into four levels. The highest level (that is, the fourth level) is the elliptic curve. Digital signature and signature verification calculation scheduling, the third level is scalar multiplication calculation, the second level is point addition and doubling point operation, the first level is various modular operations (modular multiplication, modular inverse, modular addition, modular subtraction, modular shift bits). In the implementation method of this embodiment, in order to reduce additional hardware overhead, the modulus for generating signature verification parameters in the signature and signature verification steps is replaced by a modulo addition calculation with an addend of 0, which avoids additional...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com