Vulnerability verification method and device, equipment and medium
A verification method and verification method technology, applied in the field of network security, can solve the problems of no repeated vulnerability processing and local vulnerability verification, so as to reduce risks and improve work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
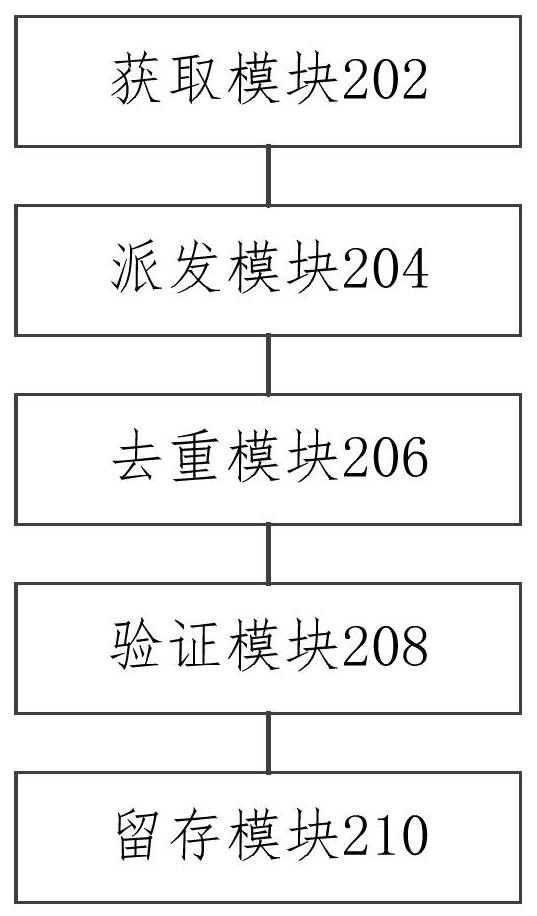
Image
Examples
example 1
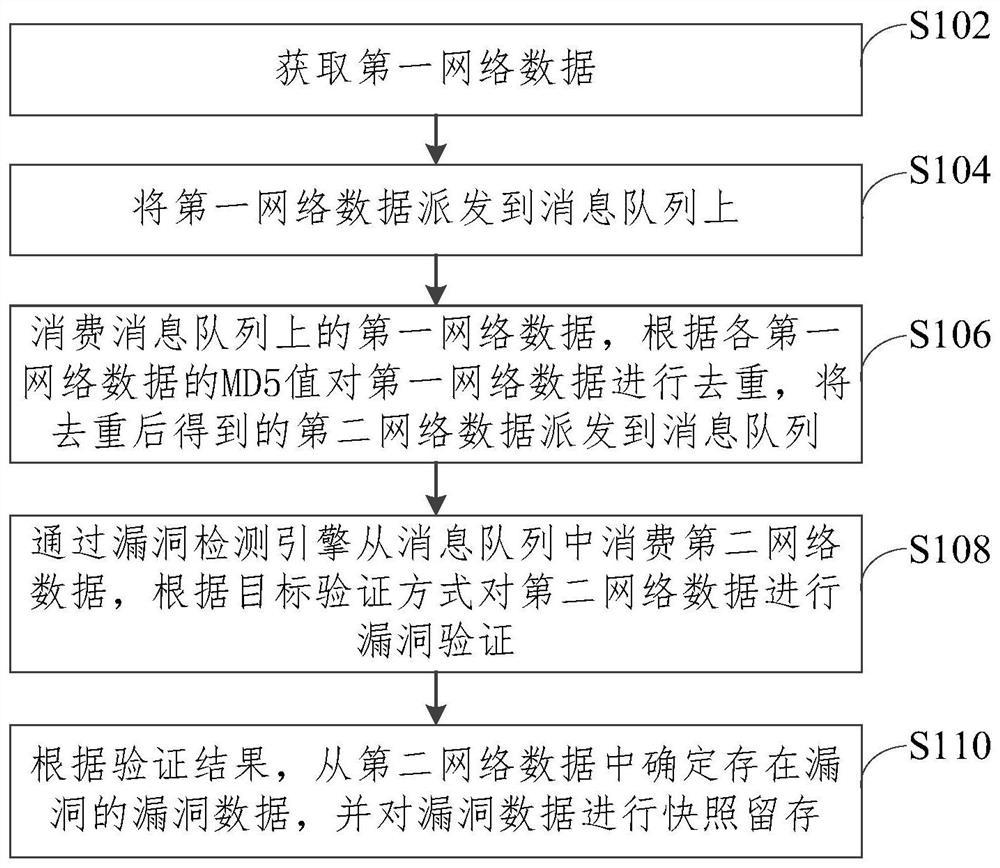
[0053] Example 1: When the second network data is an XXS (Cross Site Scripting, Cross-Stand Script) Vulnerability, the file contains a type of vulnerability or sensitive file reads the vulnerability, the matching target verification method is a web vulnerability verification method. In this case, the second network data is verified according to the web vulnerability verification method; where the web vulnerability verification method is:
[0054] Re-constructing the URL of the second network data, checks if the second network data after reconstructing the URL contains a preset data information or response state; if included, it is determined that there is a vulnerability in the second network data. Of course, if not included, there is no vulnerability in the second network data.
example 2
[0055] Example 2: When the second network data is the type of SQL injection, the target verification method that matches is the open source penetration test tool SQLMap, which is also vulnerable to the second network data using SQLMAP.
example 3
[0056] Example 3: When the second network data is a Struts Vulnerability or SSL (Secure Sockets Layer Socket Layer) Vulnerability, the second network data is validated by integrating or writing plugins through the Struts Scan tool. Specifically, for the Struts Vulnerability SSL Vulnerability This vulnerability type is unable to use a simple replacement parameter, you can use the Struts SCAN tool to integrate vulnerability verification; or can provide plug-in writing function, perform different vulnerabilities Write a plugin to implement vulnerability verification of the second network data by writing a plugin.
[0057] The vulnerability detecting engine provided in this embodiment includes a variety of verification methods to enhance the type of overlay verification vulnerability to avoid hosted hidden vulnerabilities, reduce the risk of vulnerability.
[0058] Step S110, according to the verification result, determine the vulnerability data of the vulnerability from the second ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com