QR code authentication method, communication equipment and storage medium
An authentication method and two-dimensional code technology, which are applied in the fields of communication equipment and storage media, and two-dimensional code authentication methods, to achieve the effects of avoiding computational burden, improving security, and safe and effective authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
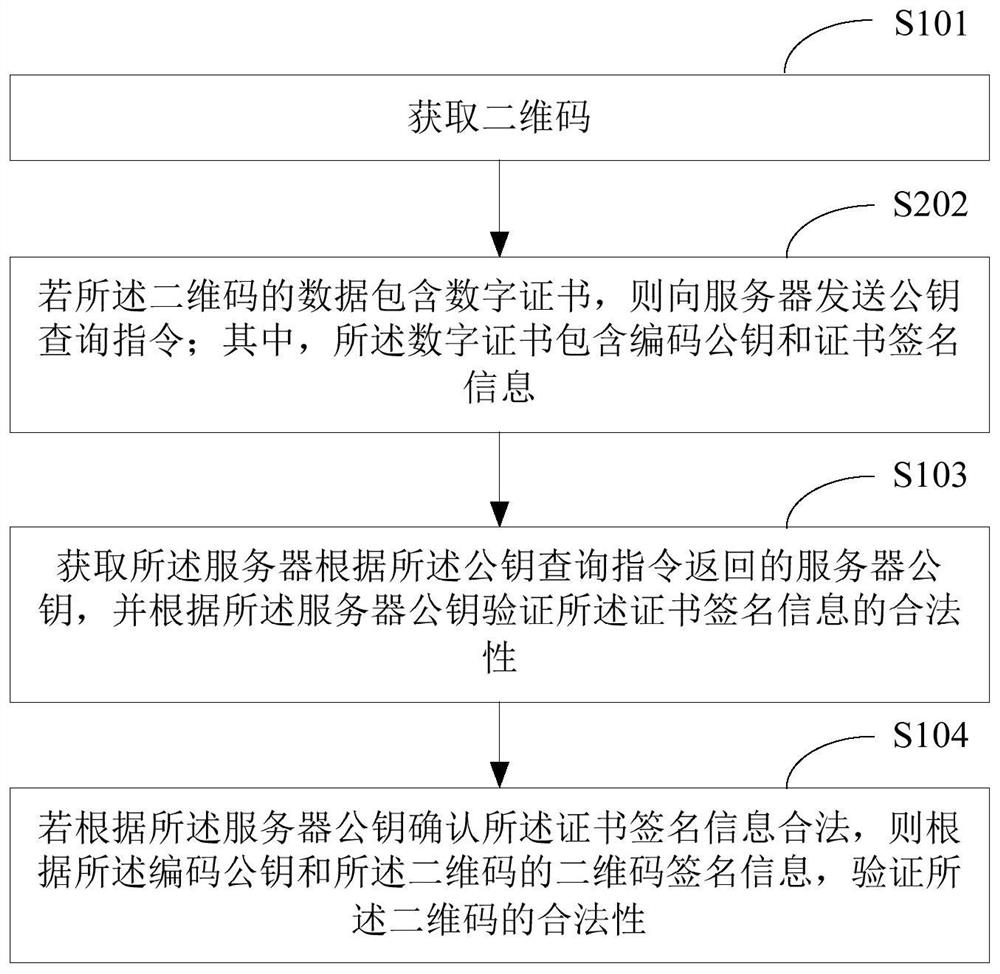
[0058] see figure 1 , figure 1 It shows the implementation flowchart of the first two-dimensional code authentication method provided by the embodiment of the present application. The execution body of the method is a user terminal, which includes but not limited to smart phones, tablet computers, notebooks, desktop computers, etc. Such as figure 1 The QR code authentication method shown is detailed as follows:
[0059] In S101, a two-dimensional code is acquired.
[0060] In the embodiment of the present application, the user terminal reads the data of the two-dimensional code by scanning the two-dimensional code. The two-dimensional code can be a two-dimensional code displayed on the display screen of the communication device, or a two-dimensional code printed on paper or other object planes, or a two-dimensional code contained in a picture received by the user terminal itself. code.
[0061] The above-mentioned two-dimensional codes include but are not limited to stack...
Embodiment 2
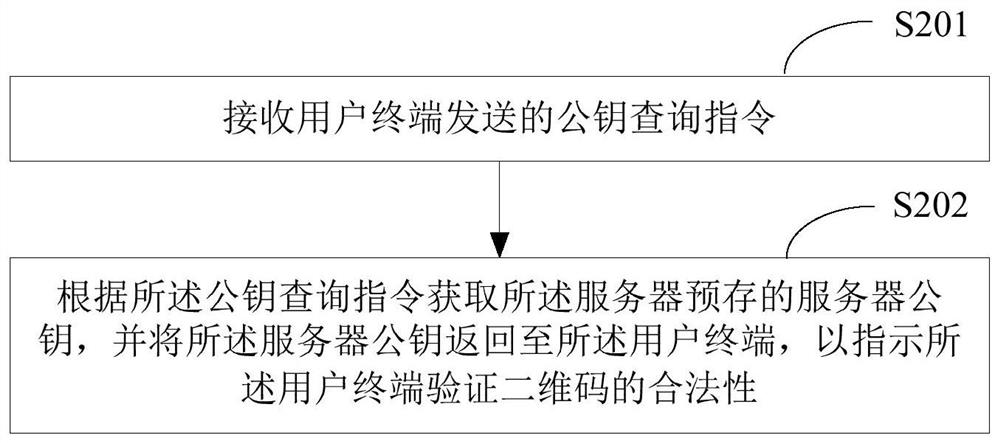
[0123] see figure 2 , figure 2 It shows the implementation flowchart of the second two-dimensional code authentication method provided by the embodiment of the present application, and the execution body of the method is the server. Such as figure 2 The QR code authentication method shown is detailed as follows:
[0124] In S201, a public key query instruction sent by a user terminal is received.
[0125] Corresponding to step S102 in Embodiment 1, the server may receive a public key query command sent by the user terminal, and the public key query command is an command sent by the user terminal after confirming that the data of the two-dimensional code contains a digital certificate.
[0126] In S202, obtain the server public key pre-stored in the server according to the public key query instruction, and return the server public key to the user terminal, so as to instruct the user terminal to verify the legitimacy of the two-dimensional code.
[0127] After receiving t...
Embodiment 3
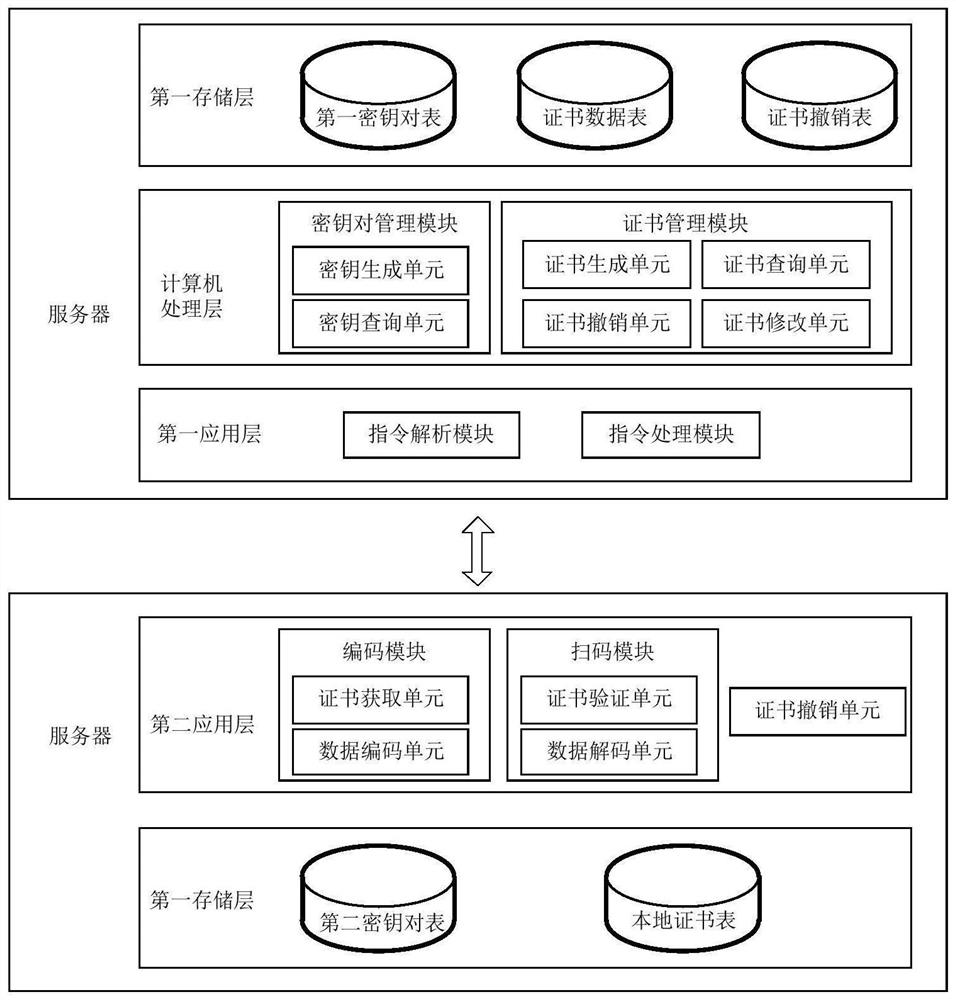
[0157] Figure 10 It shows a schematic structural diagram of a first two-dimensional code authentication device provided by the embodiment of the present application. The first two-dimensional code authentication device is applied to a user terminal. part:
[0158] The first two-dimensional code authentication device includes: a two-dimensional code acquisition module 101 , a public key query module 102 , a public key acquisition module 103 , and a two-dimensional code legality verification module 104 . in:
[0159] The two-dimensional code acquisition module 101 is configured to acquire the two-dimensional code.
[0160] The public key query module 102 is configured to send a public key query instruction to the server if the data of the two-dimensional code includes a digital certificate; wherein, the digital certificate includes encoded public key and certificate signature information.
[0161] The public key obtaining module 103 is configured to obtain the server public ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com