Java security protection method and device based on JVM sandbox and black and white lists and medium
A black-and-white list and security protection technology, applied in the field of Java security protection, can solve the problems that the security of Java applications cannot be guaranteed, and the white list cannot be pre-written for safe operation, so as to achieve the effect of network resource isolation and security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
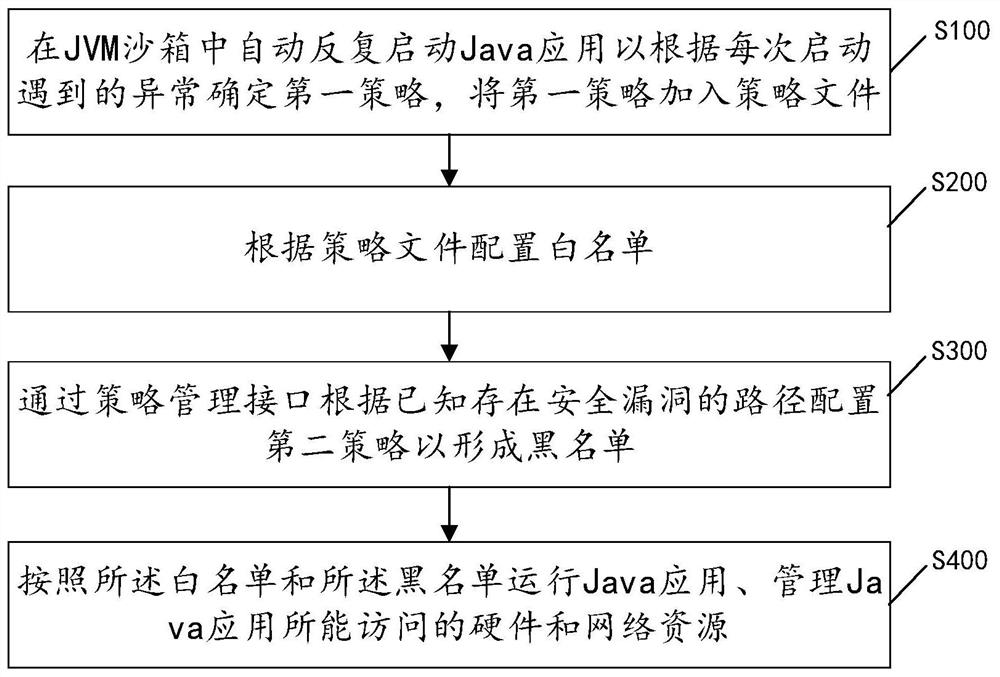
[0060] refer to figure 1 As shown, the embodiment of the present application provides a Java security prevention method based on JVM sandbox and black and white list, including:
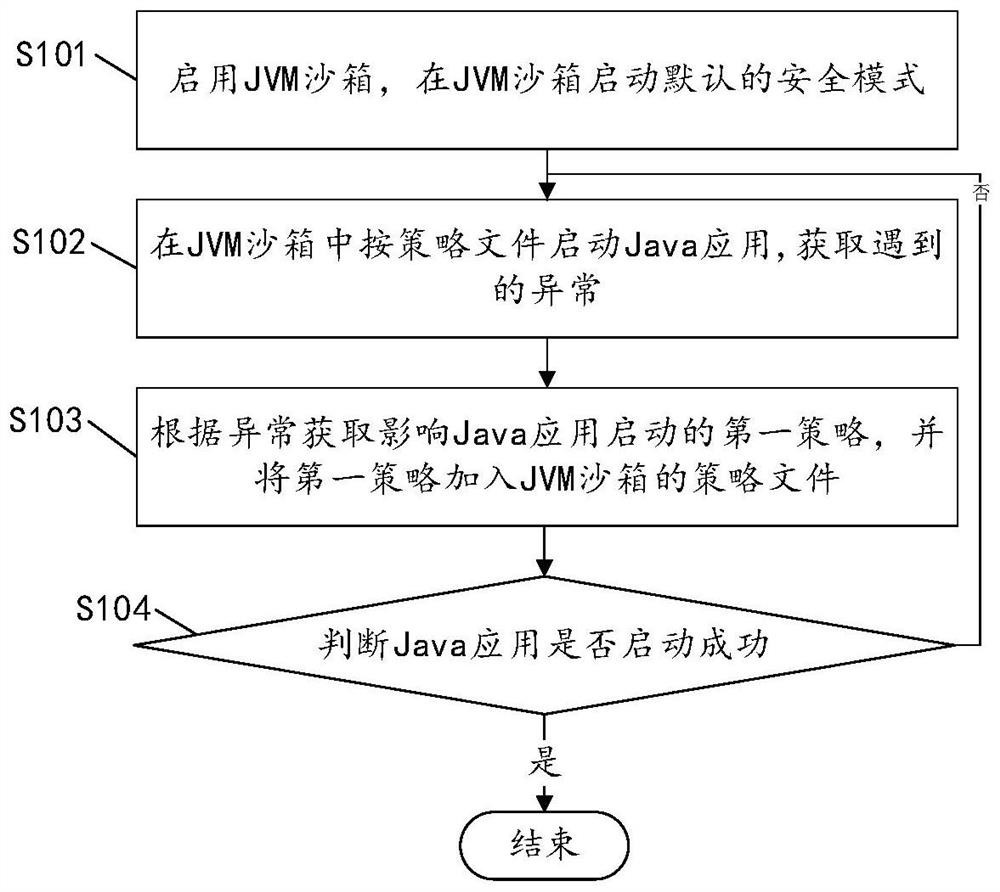
[0061] S100, automatically and repeatedly start the Java application in the JVM sandbox to determine the first strategy according to the exception encountered each time, and add the first strategy to the strategy file until the Java application starts successfully; for the specific implementation process, refer to figure 2 As shown, the specific process includes:
[0062] S101, enabling the JVM sandbox, and starting a default security mode in the JVM sandbox; no parameters are configured in the default security mode policy file, and the content is empty.
[0063] S102, start the Java application in the JVM sandbox according to the policy file; since the relevant first policy is not provided in the policy file at the initial stage, that is, the class loader and security manager of the JVM are not co...
Embodiment 2
[0092] The embodiment of this application provides a device for realizing Java security protection based on JVM sandbox and black and white list, refer to Figure 8 As shown, the device for implementing Java security protection based on the JVM sandbox and black and white lists includes:
[0093] A strategy extraction module, the strategy extraction module is used to control the repeated automatic restart of the Java application in the JVM sandbox, and obtains the first strategy that affects the startup of the Java application according to the exception encountered at each startup, and adds the first strategy to the policy file;
[0094] a whitelist configuration module, the whitelist configuration module configures a corresponding whitelist according to the policy file;
[0095] A blacklist configuration module, the blacklist configuration module provides a policy management interface, and the administrator configures a second policy to form a blacklist according to paths kn...
Embodiment 3
[0100] The embodiment of the present application provides a storage medium for realizing the Java security protection method based on the JVM sandbox and the black and white list. The storage medium for realizing the Java security protection method based on the JVM sandbox and the black and white list stores at least one instruction, and executes the described The instructions implement the Java security prevention method based on the JVM sandbox and the black and white lists.
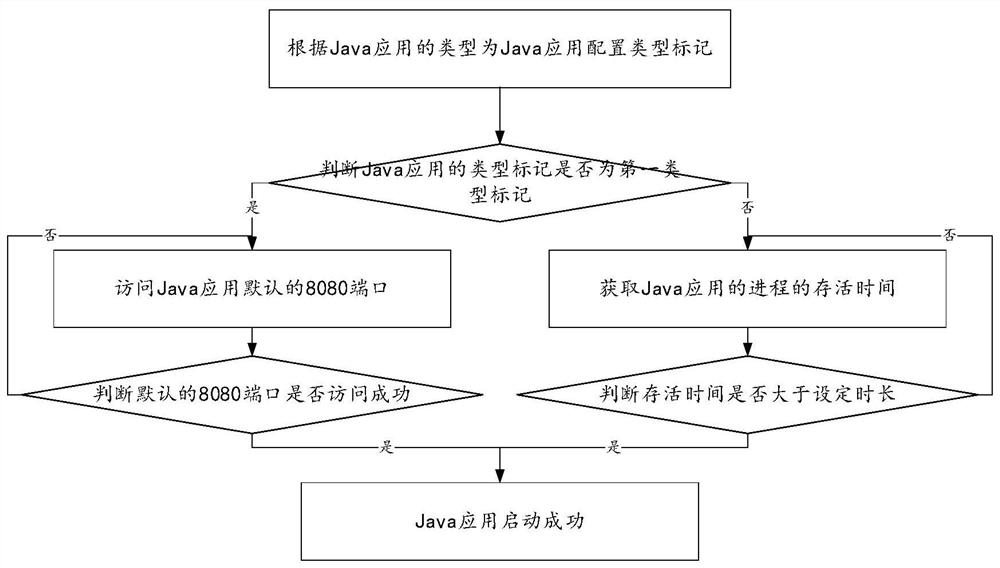
[0101] This application repeatedly starts the Java application in the JVM security sandbox until the Java application starts successfully, traverses and obtains all exceptions that affect the startup of the Java application, determines the first strategy for handling exceptions and adds it to the policy file, and configures the whitelist according to the policy file to achieve Automatic customization of the whitelist.
[0102] This application uses the formed whitelist combined with a custom blacklist ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com