Docker operation method and device, server and storage medium
An operation method and technology of operation instructions, applied in the direction of program control devices, instruments, program control design, etc., can solve problems such as poor security and user data leakage, and achieve the effect of strengthening management, improving security, and avoiding leakage risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
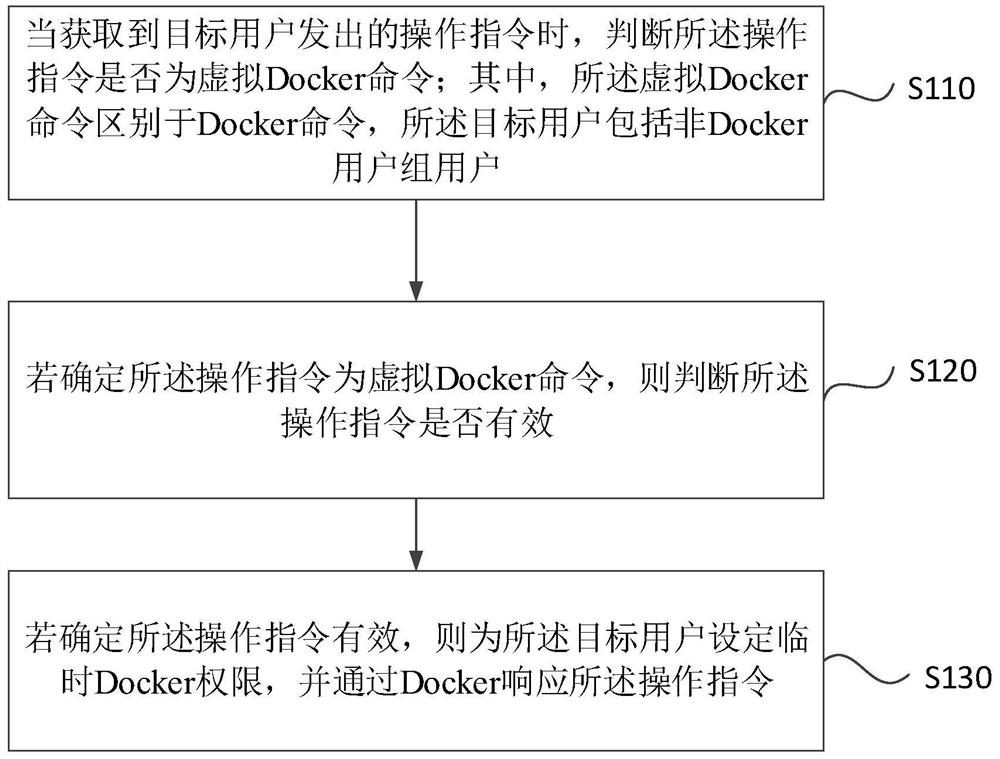
[0033] figure 1 It is a flow chart of a Docker operation method provided by Embodiment 1 of the present invention. This embodiment is applicable to a situation where a non-Docker user group user executes a corresponding operation in Docker through a Docker command in a multi-user environment. The method can Executed by the operating device of Docker in the embodiment of the present invention, the device can be implemented by software and / or hardware, and integrated in a server, typically, it can be integrated in a management server equipped with a Linux system. The method specifically includes the following steps :
[0034] S110. When the operation instruction issued by the target user is obtained, judge whether the operation instruction is a virtual Docker command; wherein, the virtual Docker command is different from the Docker command, and the target user includes a non-Docker user group user.
[0035]A Docker command consists of at least two identification information, na...
Embodiment 2
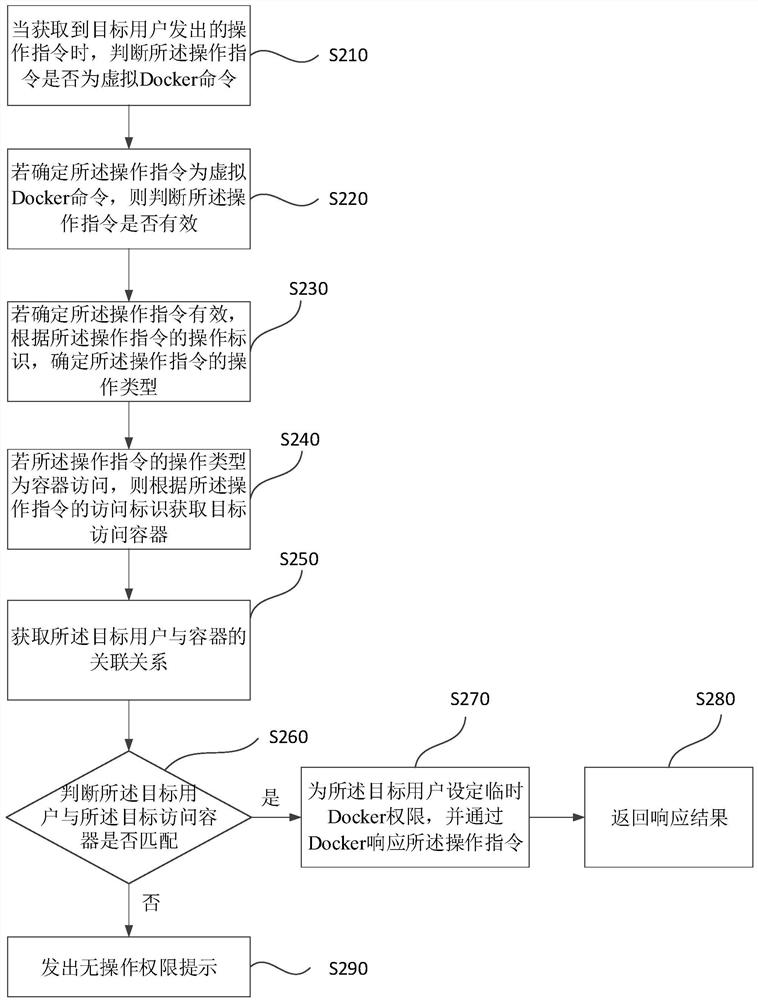
[0051] figure 2It is a flowchart of a Docker operation method provided by Embodiment 2 of the present invention. This embodiment is embodied on the basis of the above technical solution. In this embodiment, the operation type of the operation instruction is determined to be container access. The method Specifically include:
[0052] S210. When the operation instruction issued by the target user is obtained, judge whether the operation instruction is a virtual Docker command; wherein, the virtual Docker command is different from the Docker command, and the target user includes a non-Docker user group user; perform S220.
[0053] S220. If it is determined that the operation instruction is a virtual Docker command, determine whether the operation instruction is valid; execute S230.
[0054] S230. If it is determined that the operation instruction is valid, determine the operation type of the operation instruction according to the operation identifier of the operation instructio...
Embodiment 3
[0067] image 3 A flowchart of a Docker operation method provided by Embodiment 3 of the present invention. This embodiment is embodied on the basis of the above-mentioned technical solution. In this embodiment, judging whether the operation command is valid includes judging whether the target user is a virtual Docker user group user, and judging whether there is an identical target operation identification with the operation identification of the operation instruction in the operation identification of at least one target Docker command, the method specifically includes:
[0068] S310. Create a virtual Docker user group; execute S320.
[0069] S320. Encapsulate at least one target Docker command through an encapsulation script; wherein, the encapsulation script includes an encapsulation identifier; perform S330.
[0070] S330. Obtain an operation instruction issued by the target user; wherein, the target user includes a user who is not in the Docker user group; perform S340....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com